Generate a QR Code Attack Vector
QR codes are almost ubiquitous nowadays. You can find them in any product, on theater tickets, and even in street commercials. The primary objective of QR Codes is to be used for advertisements or to provide more detail about a particular product or service to people who are interested. However, attackers and penetration testers may benefit from the widespread use of QR codes. Hackers can use QR codes to target untrustworthy users, and penetration testers can incorporate this form of attack into their social engineering interactions.
When a QR code is scanned, attackers can easily embed a malicious URL containing custom malware, which can then ex-filtrate data from a mobile device. They may also provide a malicious URL in a QR code that guides users to a phishing site and invites them to reveal their credentials.
If you’re running a penetration test and want to use this form of assault, it’s a simple process to do so. In reality, there are a plethora of forms and variations to try with this attack vector, but in this article, we’ll show you how to use Social Engineering Toolkit to carry it out.
After starting “Social Engineering Toolkit” in your Linux terminal, select option “1” for social engineering attacks and hit “Enter.”

Select the option “8” to generate a QR code attack vector.

This attack vector will create a QR code for you with whatever URL you want. When you have the QR code generated, select an additional attack vector within SEToolkit, and deploy the QR code to your victim. You may redirect the victim to any malicious website you want, but here in our example, we will be redirecting our victim to “https://www.imdb.com/movies-coming-soon/” web page.
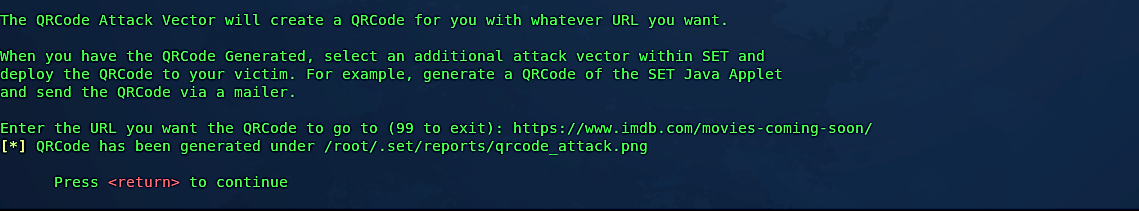
Once everything is set correctly, the QRCode will be generated under the “/root/.set/reports/” directory as “qrcode_attack.png.”
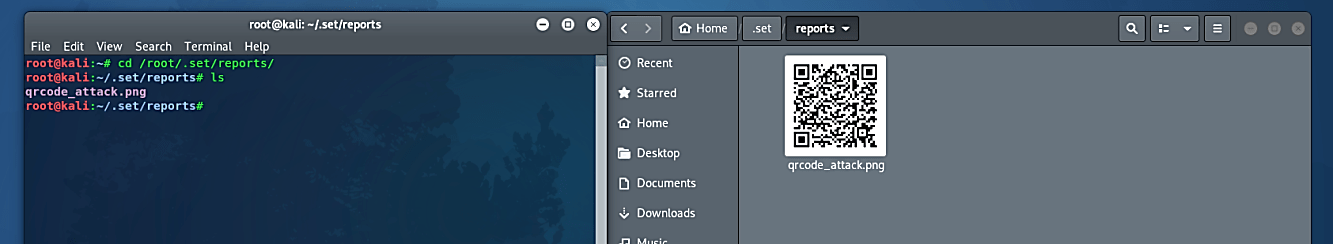
This simple experiment shows how easily malicious content can be embedded in a QR Code. Since QR phishing requires so little effort to be effective, it’s become increasingly common. Furthermore, since QR codes are widely used for contactless communication, attackers have several chances to paste their own codes over existing ones without anyone noticing.
Cybercriminals may use QR phishing to gain access to your company’s confidential information. Your employee, for example, might scan a code that takes them to a bogus bank login page. An intruder may use software that crawls the internet for other sites with that employee’s username once their login credentials have been entered. When a match is identified, the program logs into the account using the phished login credentials. An attacker may gain access to your organization’s infrastructure if your employee uses the same login credentials for multiple accounts, even those related to work.
Mobile phishing is effective whether or not QR codes are used since mobile devices are personal. Anybody that has lost a phone or tablet understands how often we depend on them in our daily lives, whether it’s to text a friend, pay for food, or travel from point A to point B. Mobile devices have become the tools we use to remain active at home and at work while we continue to work remotely. You need a way to distinguish trustworthy sources from those attempting to steal your employees’ information now more than ever. In other words, you need protection that can deal with phishing even though your workers aren’t within the office’s security perimeter.
