Google Dorking
Google is a tool that aids in finding what one is searching for. Google operators are the terms given to us to make our pursuit refined and straightforward. These operators, likewise named as cutting-edge Google operators, provide accurate data. It diminishes the time of the search by instantly giving the data as we don’t need to move from one page then onto the next one. These operators work as an inquiry.
Newsrooms, investigative organizations, security auditors, and tech-savvy criminals employ “GoogleDorking,” also known as “Google hacking,” to query multiple search engines for information hidden on public websites and vulnerabilities exposed by public servers. Dorking is a technique for exploiting the full potential of search engines to penetrate web-based services to depths that aren’t always obvious at first.
To perform a GoogleDork, all you need is a computer, an internet connection, and a basic understanding of search syntax. The fundamental syntax to perform GoogleDork is to specify the “operator:” then provide the “term to be searched.”
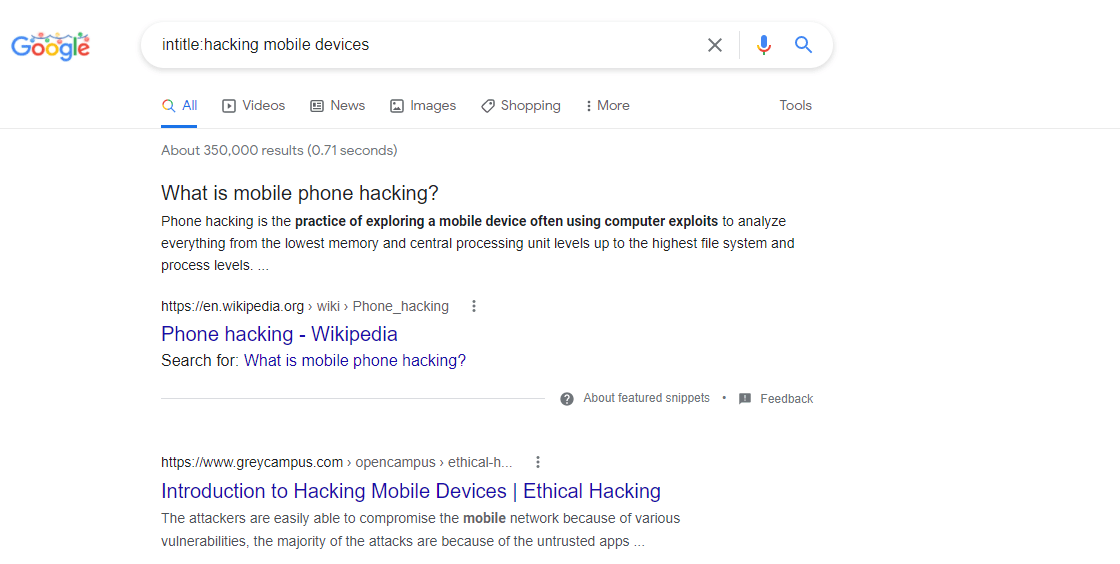
Intitle:
This query returns the pages, which include the entered term in their title.
Ex: (intitle:hacking mobile devices).
Inurl:
This query returns the pages, which include the entered term in its URL.
Ex: (inurl:data breach).

Allinurl:
Same as the previous operator, but only returns matches for URLs that meet all the matching criteria.
Related:
It will provide the result related to the entered query.
Ex: (related:hacking).

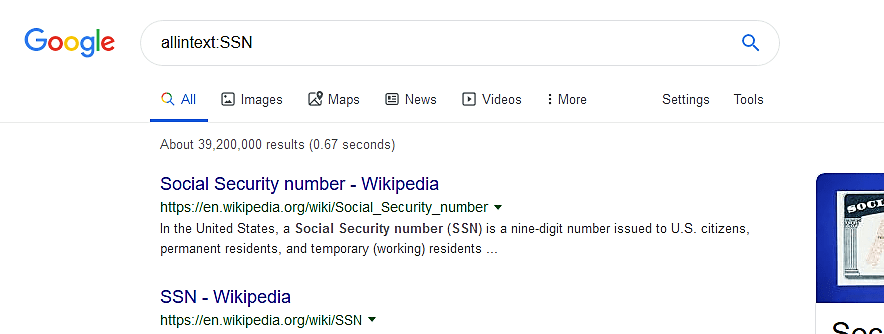
Allintext:
It performs the undertakings of finding a specific string in the text of the webpage.
Ex: (allintext:SSN).
The above-given query will return pages, which include the term SSN in the text.
Intext:
This operator searches the entire content of a given page for keywords supplied by the hacker.
Cache:
This operator shows the cached version of the page in place of the current one. The operator is used with the URL of the page, which you want to view the cached version.
Ex: (cache:thehackernews.com).

Define:
This operator defines a term as a result.
Ex: (define:security).

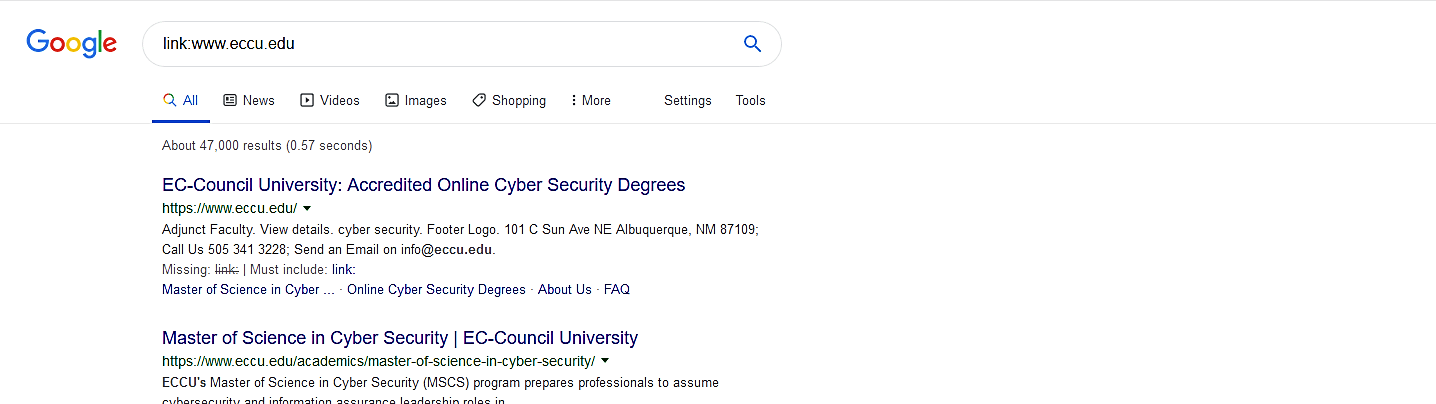
Link:
This operator helps to search the pages which link to other pages.
Ex: (link:www.eccu.edu).
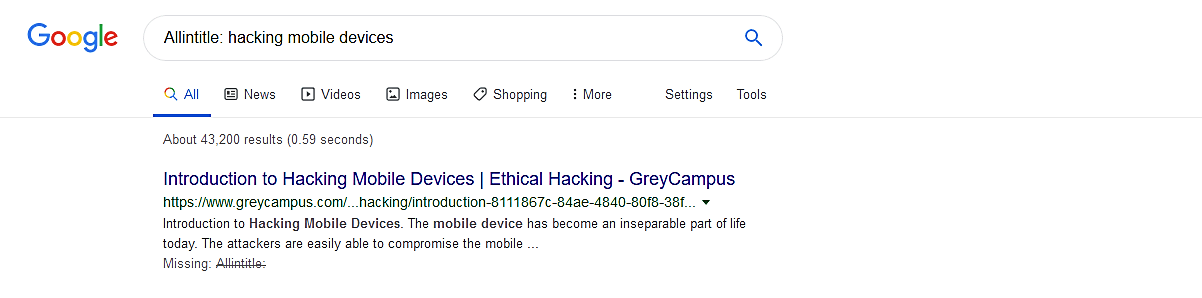
Allintitle:
This operator is a little bit different from the “intitle” operator. In the “intitle” operator, there was no coercion of the term in the query to be present in the title, whereas in the “allintitle” operator, this is a must for the condition in the query to be present in the title.
Ex: (allintitle: hacking mobile devices).
Filetype:
It helps to narrow down search results to specific types of files such as PHP, PDF, or TXT file types.
Ext:
Very similar to filetype, but this looks for files based on their file extension.
Site:
This dork limits the scope of a query to a single website.
Phonebook:
It will search for the phone number related to your victim’s name.
Ex: (phonebook: john doe).
Maps:
Performs searching in the Google maps.
Books:
Google has an online library store. If you want to find exciting books, use this dork.
Ex: (book:Hacker’s Playbook).
Froogle:
Performs searching in Froogle in place of Google. Froogle, which is a mix of the words “Google” and “frugal,” is a searchable shopping index that resembles the Google Directory but focuses on delivering you to an online point of purchase for the item you’re looking for.
Info:
Google searches information about the string entered next to the “info” operator.
Ex: (info:NASA).
Movie:
You can find information about films on google using this dork.
Ex: (movie:watch Terminator online)
Weather:
You can find information about the weather on google using this dork.
Ex: (weather: 09/08/2019 New York)
Google Dorking has been used broadly for both intrusions and information mining. Valuable information like email addresses, phone numbers can be mined out from the search engine. Even credit card information is sometimes leaked through vulnerable applications. Google hacking assists as a useful tool in penetration testing, as well. Tools like Metasploit, recon-ng, and Nmap now have automated scripts that search google for helpful information related to a particular site or organization.
Google Dorking also finds excellent use in social engineering attacks and carrying out phishing campaigns. Even though Google hacking is an old topic and technique, it remains sufficient even to this day, only because vulnerable websites, misconfigured servers keep coming up now and then all over the internet, and Google monitors it all.
