Local file inclusion using PHP filter (Base64 encoding)
Another very interesting method of local file inclusion is to use the “php://filter” function. A “php://filter” allows a pen tester to include local files and then let the base64 function encode the output. Therefore, any base64 output then needs to be decoded to reveal the contents.
To see this in action, type the following command “php://filter/read=convert.base64-encode/resource=/etc/passwd” after “10.10.10.6/bWAPP/rlfi.php?language=“ and then hit “Enter”.

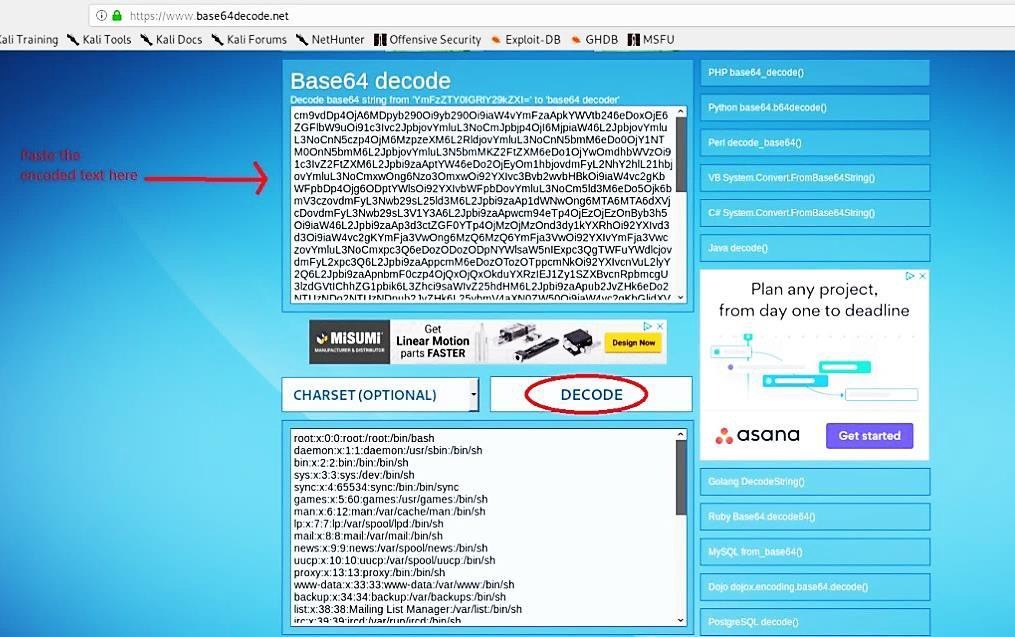
It should generate a base64 encoded text. Copy the text to use later on in the base64 decoding tool.
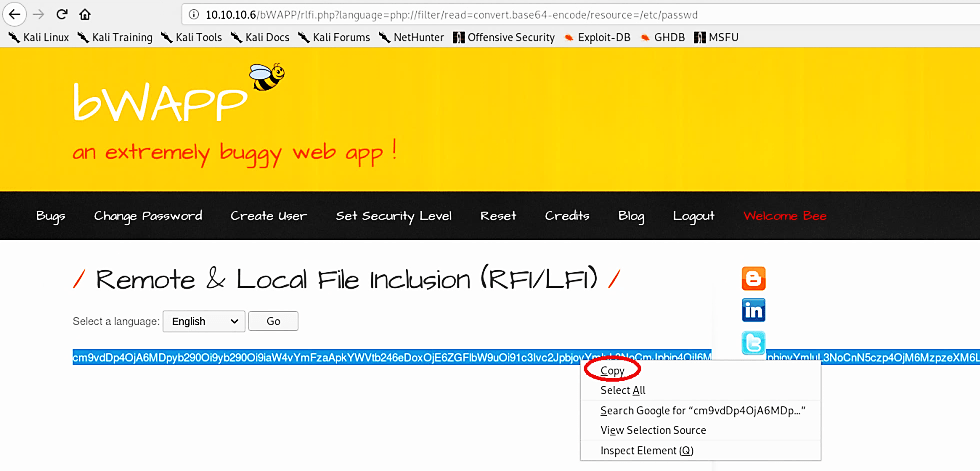
Open up a new tab on your browser and search for “online base64 decoders”. Click on any available link and then paste the text to decode it to reveal the information (Note: you can perform this task from the “Hackbar” Firefox add-on tool).
Suggestions for allowing users to securely read or download files
Save the file paths in a database and give each one a unique ID.
Users would only be able to see the ID and not be able to access or alter the direction as a result of this.
Ignore all other filenames and routes and use a whitelist of files.
Using a whitelist of files to ignore all other filenames and paths.
Instruct the server to submit download headers automatically and not to execute files in a particular directory like /download/.
You can then direct the user to the file on the server without having to write any additional download code.
Attackers have a range of filenames to use for knowledge disclosure or code execution, so blacklisting filenames is a good idea. It is virtually impossible to keep such a list up to date. It’s also not enough to blacklist files like /etc/passwd or /etc/hosts, which are often used for LFI testing.
