Make professional and convincing Linux trojans
Trojans, viruses, worms, and other forms of malware that affect the Linux operating system are known as Linux malware. More than half of all web servers on the internet run a Linux distribution.
A Trojan is a form of the virus that appears to be legitimate code but does something else, such as allowing an attacker to take your website/web-server and perform actions such as reading, deleting, or updating data. Many trojans serve as a backdoor to your website, allowing attackers to access it and conduct unauthorized activities, as well as Ransomware attacks.
One of the professional and convincing methods to create a Linux-based Trojans is though embedding backdoors into legitimate Linux packages. In this article, we will show you how to insert a backdoor in a “chromium” browser application and send it to our target computer for exploitation.
Since our target computer is Ubuntu, we need to search for Ubuntu packages. Go to the “https://packages.ubuntu.com/” page and select the correct version of Ubuntu your target computer is running.
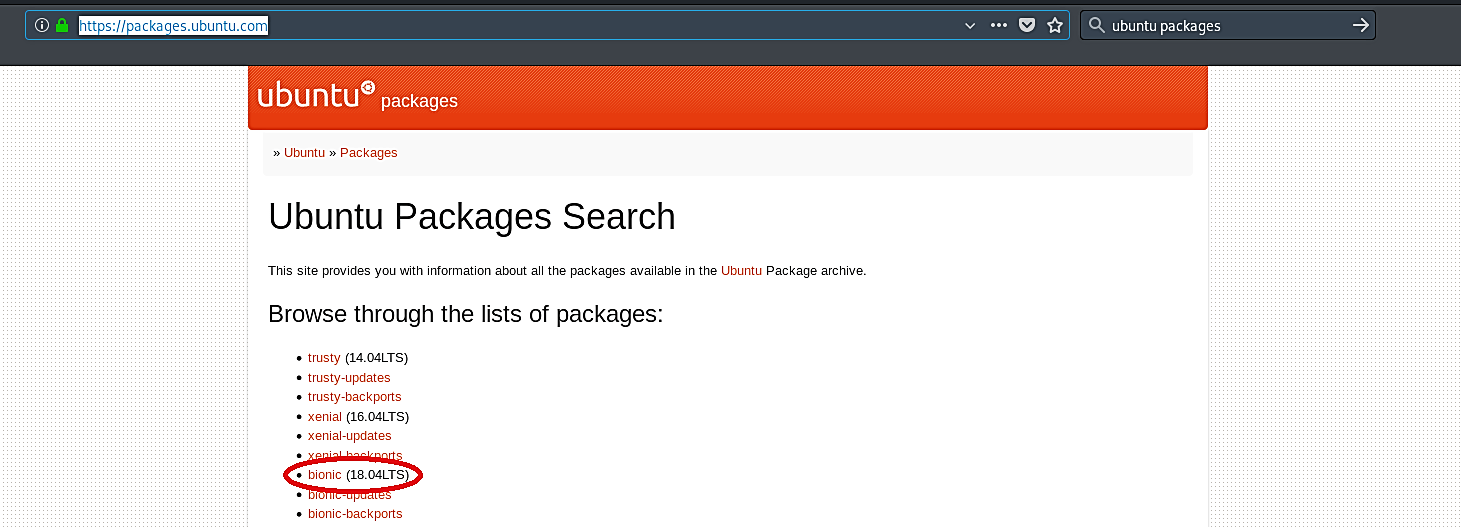
Then scroll down and find the link related to “Web Software.”

Once you are on the web software page, search for the “chromium-browser” application.

Specify the correct architecture and download it to your computer.
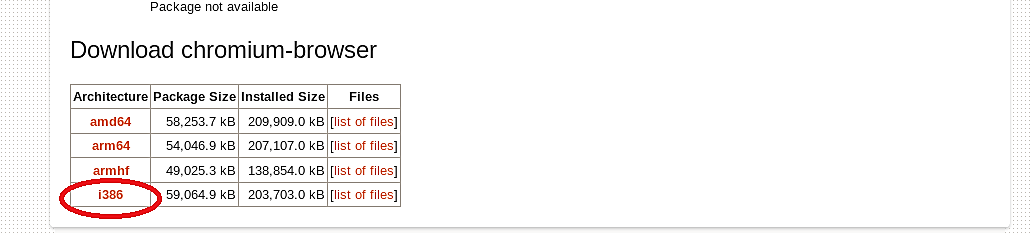

Next, we need to un-package the downloaded file using the “dpkg -x” command.
Ex: (root@kali:~/Downloads# dpkg -x chromium-browser_73.0.3683.75–0ubuntu0.18.04.1_i386.deb chromium-browser).
Here we created a folder named “chromium-browser” and un-packaged some of the contents “.deb” file to that folder. To un-package the rest of the contents, we should use additional commands.
Ex: (root@kali:~/Downloads# ar -x chromium-browser_73.0.3683.75–0ubuntu0.18.04.1_i386.deb).
These commands will un-package the “control.tar.xz” file, which we can use later.

Once everything is unpacked, navigate to the “Downloads” folder and extract the “control.tar.xz” folder. This folder contains two critical files that will be used in embedding codes.

Go to the “control” folder and copy “control” and “postinst” files. Sometimes “postinst” file may not be available, so in this case, you can create your own, open any text editor and save it with the name “postinst.”
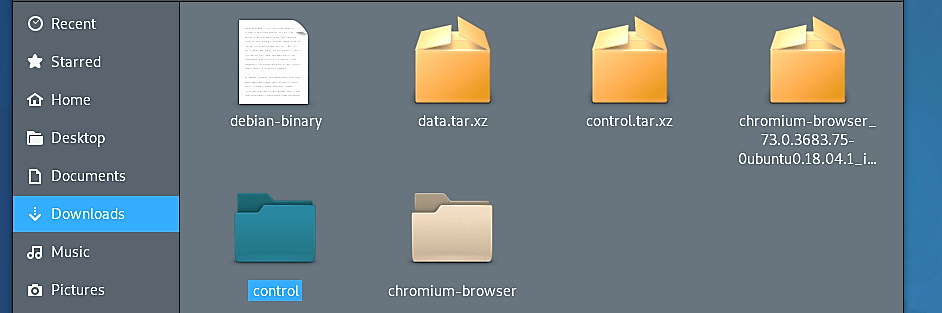

Go back to the “chromium-browser” folder and create a new folder called “DEBIAN” and paste copied files into that folder.
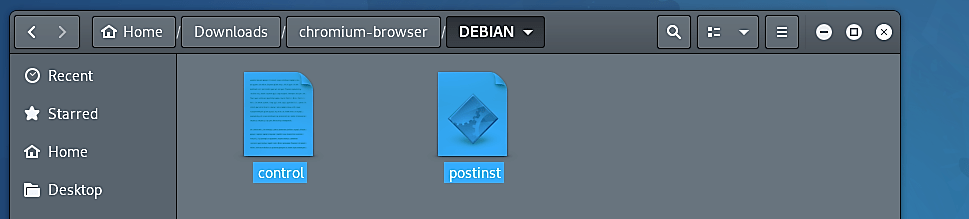
Once you pasted the files, open a “postinst” and put your backdoor inside. For this example, we will use a simple bash script that can send us a TCP shell connection.

You may put any backdoor, malicious code, keylogger, and so on. The options are endless and depend on your imagination.

Next, we need to change the permission of the “postinst” file to make it executable using the “chmod +x postinst” command.

Now our “chromium-browser” folder is ready to become a package and sent to the target computer. To build a package in Linux OS, use the command “dpkg-deb – -build.”
Ex: (root@kali:~/Downloads# dpkg-deb – -build chromium-browser/).
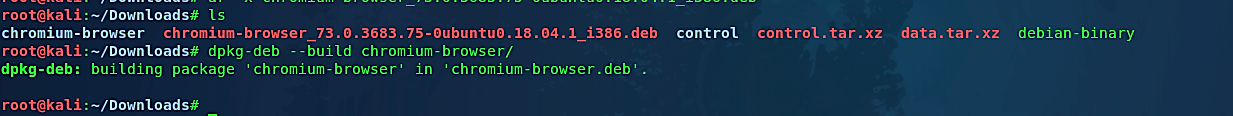
As you can see in the screenshot, we managed to create a Debian package. Let’s move the “chromium-browser.deb” package to our web server so we can quickly deliver it to the target machine and start listening for an incoming connection.
Ex: (root@kali:~/Downloads# mv chromium-browser.deb /var/www/html/Evil-Files/)
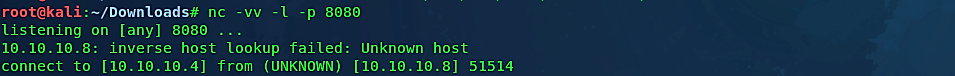
(root@kali:~/Downloads# nc -vv -l -p 8080).

Go to the target computer and download the package.

Once it is executed, the legitimate package installation window will pop up prompting to install the application.

After installation is complete, the target computer will have a fully functional “chromium Web Browser” application, but at the same time, our backdoor will run in the background and send a remote connection to an attacker machine.

“Happy Hunting!”
There isn’t a universal formula to detect a trojan or a rootkit. All you can do if your machine has been corrupted by an unknown trojan is reinstall it. If you know how the trojan works — for example, if you know the trojan doesn’t infect the kernel — there might be a less invasive way to recover. However, this is entirely dependent on understanding how the trojan operates. There is no general strategy if all you have are symptoms: the trojan detector must be smarter and lucky than the trojan designer.
A stable delivery channel is in place in many systems. When you use an apt-based tool like “apt-get install” to install a package from the Ubuntu repository, the tool verifies that the package is validated by someone Ubuntu trusts. When you install a package from an unknown source, the only information you have is that the source owner validated it, which is useless if you have no reason to trust the source in the first place.
Inherently, stealth malware has an advantage over “detectors.” This is valid if you restrict yourself to malware detection methods that depend on signatures or heuristics. However, there is another method for detecting malware: scanning for identified items. Tripwire, AIDE, and other similar programs will check files on disk. Second Look will check the kernel and processes that are currently operating. Second Look examines the operating system, active systems, and programs directly using memory forensics. It compares the code in memory to what the Linux distribution provider has published.
