Maltego - Comprehensive information gathering
Maltego is an intelligent information mining tool that renders coordinated charts for connection analysis. The device is used in online examinations for discovering relationships between snippets of data from different sources situated on the Internet.
Maltego uses “transforms” to computerize the way toward questioning various information sources.
This data is then displayed on a hub-based chart appropriate for performing a connection examination. Right now, there are three variants of the Maltego, to be specific Maltego CE, Maltego Classic, and Maltego XL. This page will concentrate on Maltego Community Edition (CE).
Every one of the three Maltego clients accompanies access to a library of the standard “transforms” for the disclosure of information from a broad scope of open sources that are regularly utilized in online examinations and digital forensics. Since Maltego can consistently incorporate with about any information source, numerous data vendors have been used Maltego as a conveyance stage for their information gathering, and this likewise implies Maltego can be adjusted to your own, one of a kind necessity.
Maltego comes pre-installed with Kali Linus distro. You need to click on the Maltego icon to run it. Once it starts, select the “Maltego CE (Free)” option from the “Product Selection” window.

Next, you need to register and create an account to log in to use Maltego freely.
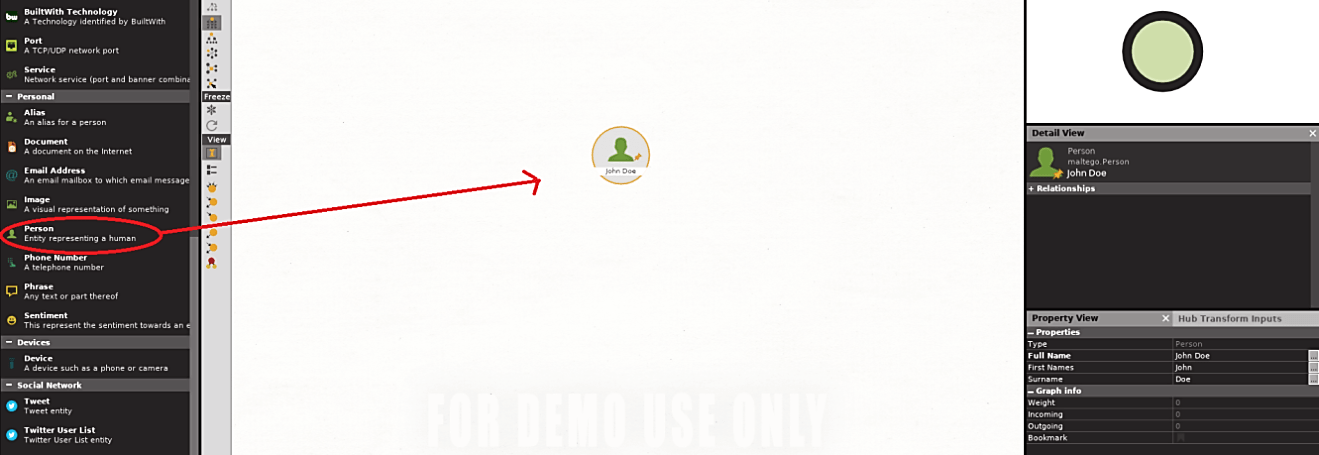
In this Maltego exercise, we will perform a personal reconnaissance. We can list different sorts of data from the name given to us. These incorporate email addresses, URLs, interpersonal organization profiles of an individual, and the shared association between two individuals. This data can be adequately utilized in a social engineering assault to either pawn the victim or to accumulate significantly more data required for the attack. To add a person to the dashboard, drag and drop a “Person” option from the left pane.
Assume that the assailant gets the name of an individual; mining of information identified with the name would begin with focusing on the individual’s email-ID. Maltego offers email-ID “transforms,” utilizing web indexes. To use this “transform,” right-click on the person and select the “Email addresses from Person” option.

As it’s shown in the screenshot below, the search engine query returns a vast number of email addresses. For this Maltego example, we will use one email ID and explain how to proceed further with the OSINT.

Select the email address and right-click to view all available “transforms” to implement. You can either perform a single “transform” search to find phone numbers, related domain names, websites, or use all available “transforms” at the same time by selecting the “All Transforms” option. This option will pull almost every public information and connection related to the target email address.

You may also perform a search on a specific domain name. Select the “Domain” option from the left pane, then drag and drop it to the dashboard. Double-click on the “Domain” icon and provide the domain name of the target website. Then right-click on it and select any “transform” you wish to perform a search. In this example, we will use the “All Transforms” option to view and collect all possible information and connections of our target website.

Maltego will currently start to accumulate information on our objective domain, and show it on the screen. The following screenshot displays all gathered email addresses from the site while Maltego collects the name servers and mail servers’ information.

Maltego completes a great deal of the automated and enormous information correlation for you, and you can spare long stretches of googling searching for data and figuring out where all that data corresponds. It is the place the genuine intensity of Maltego becomes an integral factor, information connections — not the same number of individuals guaranteed with its mining devices.
While the mining is valuable, it’s the connections between the data that will support the social architect; for instance, seeing that an objective’s email address is found on various car sites, you could expect that he/she was keen on autos and gain context on your target.
