Most widely used web application scanner - OWASP ZAP
To build up a protected web application, one should know how they will be assaulted. Here, comes the prerequisite for web application security or Penetration Testing. For security purposes, organizations utilize paid tools, yet OWASP ZAP is an incredible open-source alternative that makes Penetration Testing simpler for security analyzers.
The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools and is adequately maintained by several global volunteers. It can help you consequently discover security vulnerabilities in your web applications while you are creating and testing your applications. It’s likewise an incredible device for experienced pen-testers to use for manual security testing.
ZAP is cross-platform; it generates a proxy between the client and the website. While you explore through all of the highlights of the website, it captures all activities. At that point, it attacks the site with the known techniques.
To start the tool type, “zaproxy” in the terminal and hit “Enter.”
Ex: (root@kali:# zaproxy).
OWASP ZAP has a few different ways to play out an Active Scan. The most direct of these is to utilize the “Quick Start” welcome screen that is displayed by default when ZAP begins. To start, enter the URL you need to check in the “URL to attack:” field, and after that, press the “Attack” button.

It will dispatch a two-stage process:
Firstly, a “spider” will be utilized to crawl the site. ZAP will use the provided URL as a beginning stage to investigate the site to determine the majority of the hyperlinks inside it. The “Spider” tab at the base of the ZAP window will show all discovered connections. While the discovery process is going on, ZAP will simultaneously inactively check all the connections.
Secondly, the Active Scan will launch. When it finishes the crawling process, the active scan will begin. ZAP will dispatch an assortment of assault scenarios at the URLs recorded in the “Spider” tab. You can view all the assault advancements in the “Active Scan” tab.

When the active scan has been completed, the outcomes will be displayed in the “Alerts” tab. It will contain the majority of the security issues discovered during both the “Spider” and “Active” scans. All security threats will be flagged by their risk levels — red for High Priority, and yellow and green for Medium to Low Priority, respectively.
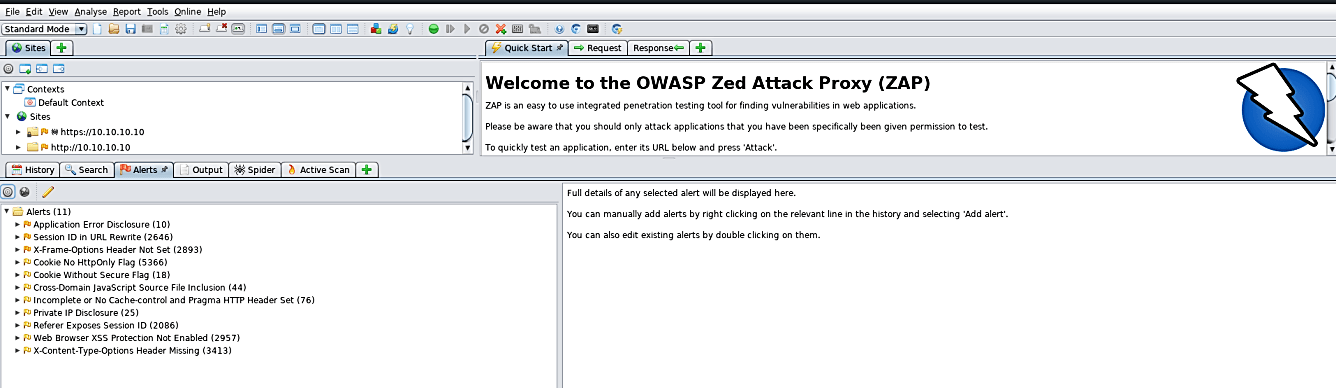
Getting a web application is vital nowadays. With regards to web engineers, fixing the weaknesses should begin from the primary floor; from the designer himself. You as a straightforward engineer not actually need to know all the nitty-gritty stuff of pen-testing. There are a few decent tools for analyzing web applications, and OWASP ZAP is one of them.
