Network traffic analysis and sniffing using Wireshark
Network traffic analysis is a troublesome and requesting task that is a crucial piece of a Network Administrator’s job. Network Administrators are continually endeavoring to keep up the smooth task of their systems. If a network were to be down notwithstanding for a short time, productivity inside an organization would decline, and on account of public service departments, the capacity to give essential services would be undermined. To be proactive instead of reactive, executives need to monitor traffic movement and performance all through the network and confirm that security breaches don’t happen inside the system.
While other network security devices, for example, firewalls and IDS/IPS tools center around checking vertical traffic that crosses the edge of a network domain, network traffic analysis solutions are centered around all interchanges — regardless of whether those are conventional TCP/IP style packets, “virtual system traffic” crossing a virtual switch, traffic from and inside cloud workloads, and API calls to SaaS applications or serverless processing instances. These arrangements likewise center on operational innovation and Internet of things (IoT) systems that are generally totally invisible to the security group. Progressed network traffic analysis devices are even compelling when system traffic is encoded.
This article will talk about various network traffic analysis methods, their functionalities, and a usage process in the real environment.
Wireshark
Wireshark is a network or protocol analyzer (otherwise called a network sniffer) accessible for free at the Wireshark website. It is utilized to dissect the structure of various system conventions and can show encapsulation. The analyzer works on UNIX, Linux, and Microsoft Windows operating frameworks, and uses the GTK+ gadget toolbox and pcap for packet capturing. Wireshark and other terminal-based free programming renditions like Tshark are released under the GNU General Public License.
Wireshark shares numerous attributes with tcpdump. The thing that matters is that it underpins a graphical user interface (GUI) and has data filtering highlights. What’s more, Wireshark permits the user to see all the traffic being passed over the network.
Wireshark has a loaded list of capabilities which includes the following:
· Profound investigation of many protocols, with more being added all the time.
· Live capture and offline investigation.
· Standard three-pane packet browser.
· Multi-stage: Runs on OS X, Windows, Linux, Solaris, FreeBSD, NetBSD, and numerous others.
· Captured network information can be perused using a GUI, or through the TTY-mode TShark utility.
· The most dominant display filters in the business
· Rich VoIP examination
· Files that are compressed with gzip can be decompressed on the fly.
· Vital information can be perused from Ethernet, IEEE 802.11, PPP/HDLC, ATM, Bluetooth, USB, Token Ring, Frame Relay, FDDI, and others.
· Coloring standards can be applied to the packet list for speedy, natural examination.
· Output can be sent out to XML, PostScript, CSV, or plain content.
· Decoding support for many protocols, including IPsec, ISAKMP, Kerberos, SNMPv3, SSL/TLS, WEP, and WPA/WPA2.
This instructional tutorial will get you up to speed with the nuts and bolts of capturing packets, filtering them, and assessing them. You can utilize Wireshark to review a suspicious program’s network traffic, examine the traffic stream on your system, or troubleshoot network issues.
You can download Wireshark for Windows or Mac OS from its official site. In case you’re utilizing Linux or another UNIX-like framework, you’ll presumably discover Wireshark in its package repositories. For instance, in case you’re using Ubuntu, you’ll find Wireshark in the Ubuntu Software Center.
Warning: Many organizations and companies don’t permit Wireshark and similar tools to run on their systems. Try not to use this device at work except if you have authorization.
Launch the Wireshark and select a network interface you want to listen to. Then click on the fin icon to begin capturing packets on that interface. If you need to capture traffic on your wireless system, then you need to select a wireless interface.

As soon as you select the interface’s name, you’ll notice the packets start to appear in real-time. Wireshark captures each packet that is passing through your system.

Analyzing patterns and signatures of Ping sweeps
This sweep is useful to discover which IPs are dynamic in the system. Ping Sweep can be performed utilizing ICMP, TCP, or UDP protocols. The most mainstream one is ICMP Ping Sweep. In the ICMP type 8 — echo request is trailed by ICMP type 0 — echo reply packets, while in TCP/UDP ping sweep packets are bound to TCP/UDP port 7, the echo port. On the off chance that the target host doesn’t bolster echo service, at that point, this TCP/UDP ping scope won’t work. Consequently, for the most part, the ICMP ping sweep is utilized. However, if there is a firewall in the middle, then even ICMP ping sweep is useless.
In this situation, the ARP scan/ARP sweep can be utilized, which will discuss later. To distinguish ICMP ping sweep in Wireshark, apply simple filter “icmp.type==8 or icmp.type==0”. TCP ping sweep can be distinguished with the “tcp.dstport==7” filter, and for UDP ping sweep “udp.dstport==7” filter can be utilized. After applying these filters, on the off chance that we are getting more than anticipated packets, at that point, a ping sweep may be going on in your system. We should be cautious about the volume of such traffic as it may be typical ping traffic. It ought to be considered as an output mark just if you are getting an unexpected increment in ICMP traffic.
Analyzing patterns and signatures of ARP sweeps
As we mentioned in the previous topic, when a firewall is implemented, and the ICMP is blocked, at that point, we can’t utilize ICMP ping sweep. In such a situation, an ARP scan is used to discover dynamic IPs in the system. Here, the aggressor sends ARP broadcast for every single imaginable IP in the selected subnet, and on the off chance that he gets ARP response; at that point, it demonstrates that IP is dynamic.
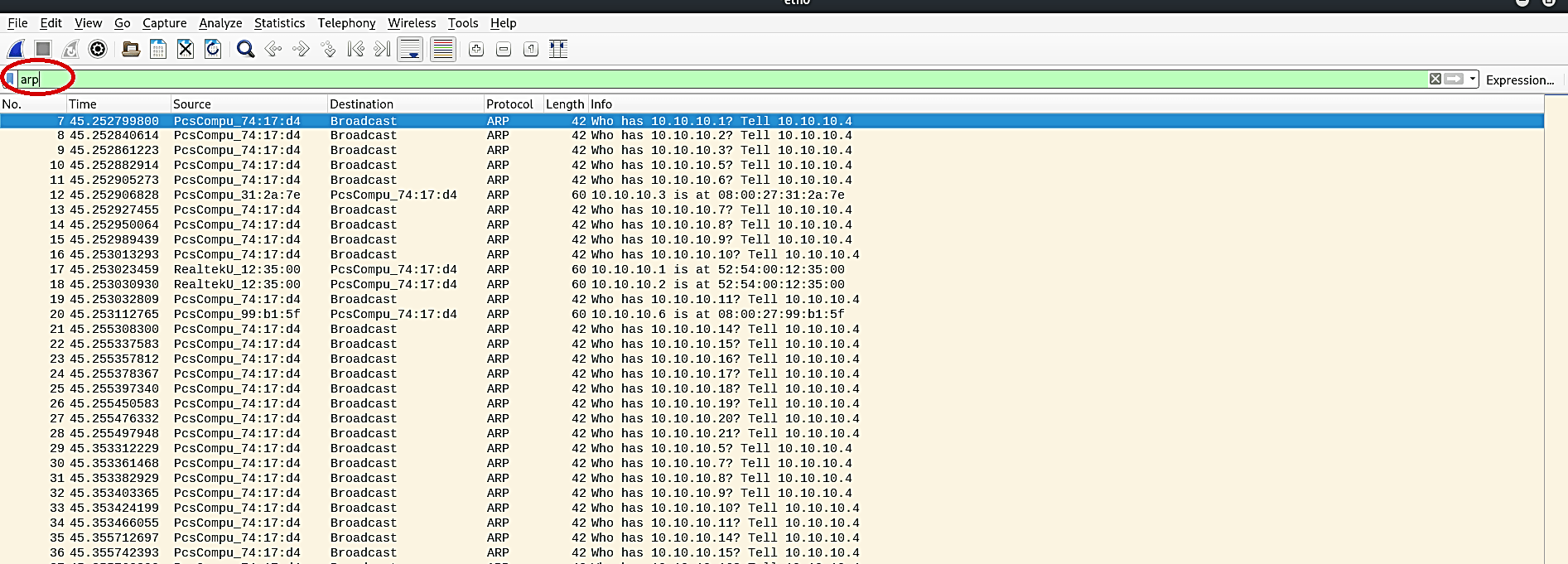
The bit of leeway of this sweep is that ARP correspondence can’t be filtered or disabled because all TCP/IP correspondence depends on it. Blocking or disabling ARP communication will break TCP/IP communication, or it will force static ARP entries, and the drawback of this output is that it can’t cross layer-three devices. This sweep can be effectively recognized with the “arp” filter. On the off chance that we are getting staggering numbers of ARP queries as appeared in the screenshot, it is an indication for ARP scan or ARP sweep.
Analyzing patterns and signatures of Stealth port scans
To identify open or closed TCP ports on the target system, a Stealth scan is the regularly used method. In this scan, the aggressor sends an SYN packet on the objective port like a typical TCP correspondence. If the port is open, the attacker will get SYN+ACK and RST packets or RST+ACK packets if the port is closed. After getting SYN+ACK packets on the open port as a response, the aggressor will send the RST packet because the attacker wouldn’t want to open a TCP session with an objective. On the off chance that the target port is firewalled, at that point expected response would be the ICMP type 3 packets with code 1, 2, 3, 9, 10, or 13.
So, if we are getting a great deal of RST packets or ICMP type 3 packets, it very well may be an indication for Stealth scan or TCP Full Connect Scan.
To perform a stealth (SYN) scan on the network, use the “nmap -sS 10.10.10.6” command in the “Zenmap” or “Nmap.”

Next, observe the traffic with a Wireshark and compare the patterns.

Analyzing patterns and signatures of TCP full connect scans
In this scan, the aggressor will perform a total three-way handshake to see whether the port is open or close. The aggressor will send the SYN packet to the objective port. If the port is open, the attacker will get an SYN+ACK packet, and if the port is closed, he will get RST+ACK packets. In the wake of getting SYN+ACK, the attacker will send an ACK packet and attempt to set up a TCP session, and after that, end it.
In Wireshark, we can utilize a comparable technique like TCP Half-open scan to recognize TCP full connect also. If the target port is firewalled, at that point, we will get a similar response, which is the ICMP type 3 packets with code 1, 2, 3, 9, 10, or 13. To recognize TCP scan packets (TCP Half-open and TCP Full Connect), you can use the following filters.
• To get SYN, SYN+ACK, RST and RST+ACK packets, use “tcp.flags==0x012 or tcp.flags==0x002 or tcp.flags==0x004 or tcp.flags==0x014”filter.
• To get ICMP type 3 packets with code 1, 2, 3, 9, 10, or 13, use “icmp.type==3 and (icmp.code==1 or icmp.code==2 or icmp.code==3 or icmp.code==9 or icmp.code==10 or icmp.code==13)” filter.
Analyzing patterns and signatures of NULL scans
In this scan, the attacker sends a TCP packet without setting any banner on it, and if he gets the RST packet as a response, it implies the port is closed. If the port is open or filtered, there will be no response to a Null scan. In the event that he gets ICMP Type 3 packets with code 1, 2, 3, 9, 10, or 13, at that point, the port is by all accounts firewalled. To identify the Null scan in Wireshark, we can utilize a simple “tcp.flags==0x000” filter. It will filter all TCP packets moving without a Flag.

Analyzing patterns and signatures of Xmas scans
Here the aggressor sends a packet with FIN, PSH, and URG TCP banners, and the response is very similar to the Null scan. To distinguish this sort of sweep in Wireshark, we can utilize the “tcp.flags==0X029” filter.

Analyzing patterns and signatures of UDP scans
In the UDP scan, the attacker sends a UDP packet on the objective port, and if that target reacts with ICMP Type 3 Code 3 packet — the port is inaccessible. However, if there is no response, at that point, it may be open or filtered. In the wake of capturing packets in Wireshark, if you are getting high numbers of ICMP Type 3 Code 3 packets, it is an indication of a UDP scan. We can utilize the “icmp.type==3 and icmp.code==3” filter to recognize UDP scans in Wireshark.

Analyzing patterns and signatures of IP protocol scans
IP Protocol Scan is useful in discovering protocols running over IP. The attacker sends packets with various protocol numbers, if he gets the ICMP Type 3 Code 2 packet as a response, at that point, it implies that this protocol isn’t running on the objective framework, while no response indicates protocol is there or filtered. To distinguish this sweep in Wireshark, we can apply the “icmp.type==3 and icmp.code==2” filter.

