Nexpose - Red team’s best friend
Nexpose is one of the main vulnerability evaluation tools. The Nexpose community version is a free program, and different releases are paid ones. In this tutorial, we will utilize the free Nexpose community version, which can filter 32 hosts. The UI is spotless, and the detailing is vigorous. Nexpose provides a simple to-utilize, useful dashboard, and, as the vast majority of the tools we have seen, it bolsters a broad scope of consistency reporting, including PCI compliance. To download Nexpose, proceed to the “https://www.rapid7.com/products/nexpose/” website and complete the registration process.
Once you download the tool, navigate to the “/Downloads” directory and give the downloaded file executable permission.
Ex: (root@kali:~/Downloads# chmod a+x Rapid7Setup-Linux64.bin).
Next, install Nexpose by executing the file.
Ex: (root@kali:~/Downloads# ./Rapid7Setup-Linux64.bin).
To start the Nexpose console type, “service nexposeconsole start.”
Now, open up your browser and type “https://127.0.0.1:3780/login.jsp” to access the Nexpose platform. Provide the credentials you have created during the Nexpose installation and login.

To perform a vulnerability scanning, first, we need to create a site by click on the “CREATE SITE” button on the home screen.

Under the “INFO & SECURITY” tab, give your site a name and a small description of your target.

Select the “ASSETS” tab, and enter the assets you want to scan into the “Assets” field.
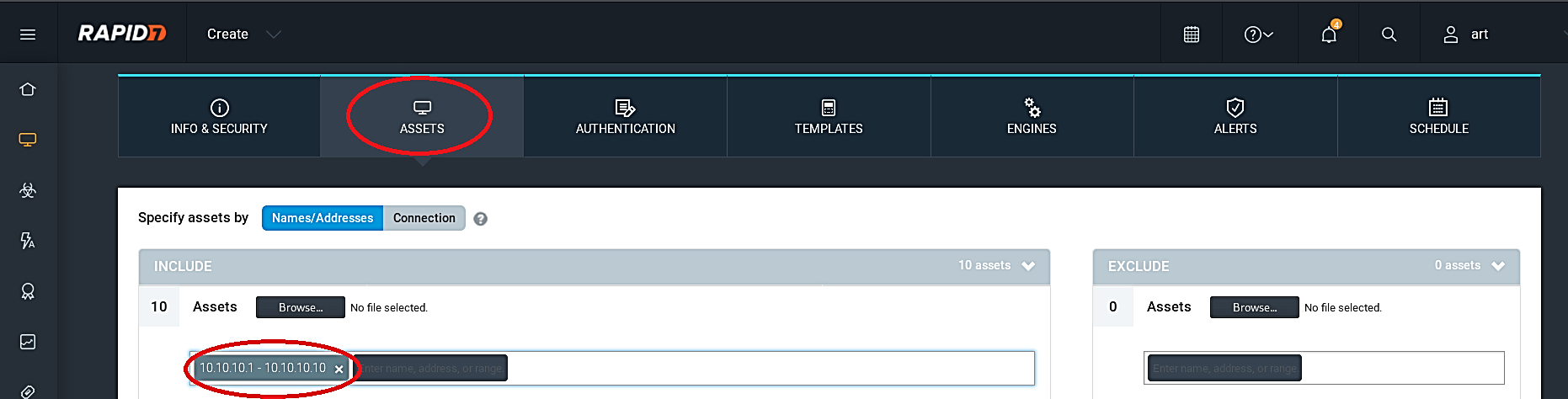
Next, move to the “TEMPLATES” tab and select any template you wish. Here we will be using the “Full audit” template. Templates are the way how scans run. Nexpose have an entire bundle of prebuilt templates like for compliance scanning (SOX, PCI, and so on) or examining SCADA frameworks, and you can likewise duplicate and modify any layout to get into the stray pieces of how Nexpose does its enchantment.
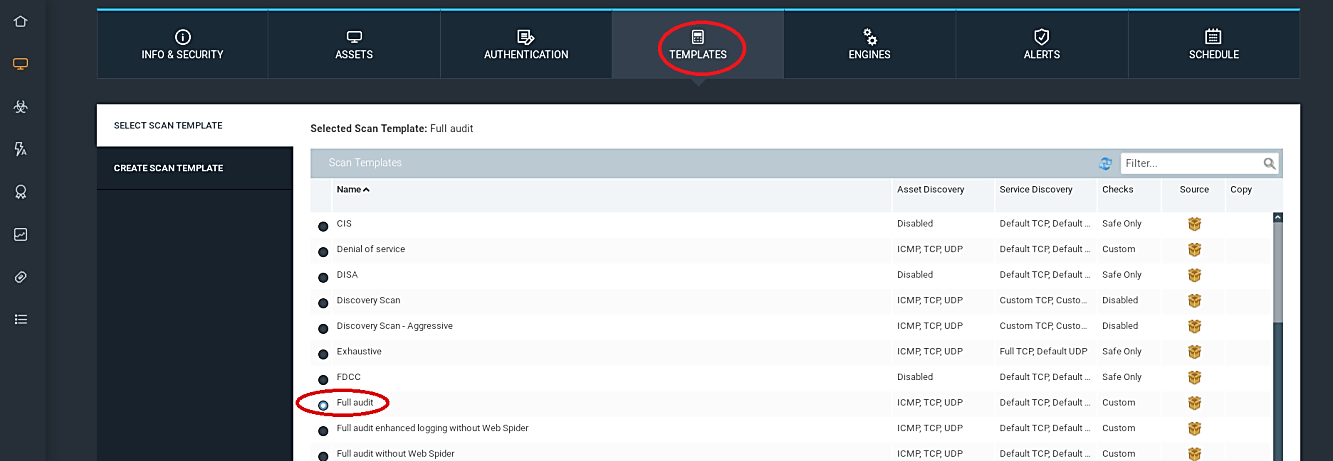
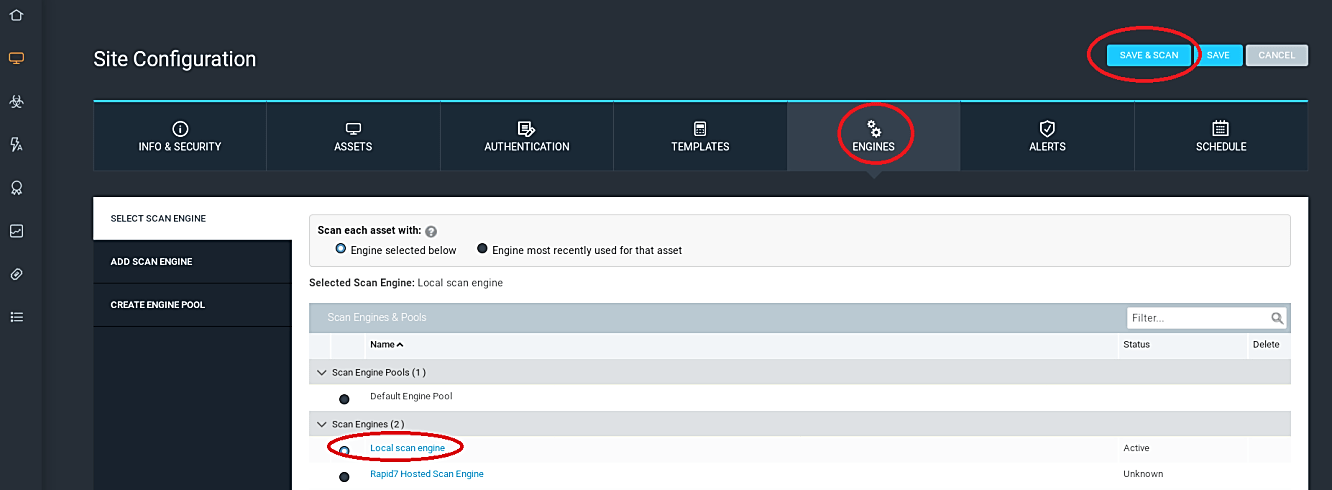
The “ENGINES” tab gives you a chance to choose which scan engine you need to do the sweep. Nexpose has a disseminated design that allows you to convey scan engines in remote areas that you don’t approach from the essential comfort and sweeps locally. Nexpose console will come with a scan engine built-in, so in this example, we chose the “Local scan engine” option to launch the scan from the central console.
Now we can click “Save and Scan” to dispatch our scan immediately. We can likewise go to the “SCHEDULE” tab to effectively plan our sweeps for a later date or set up a simple scan plan.
During the scanning process, it is possible to view some information about completed assets from the “COMPLETED ASSETS” section.
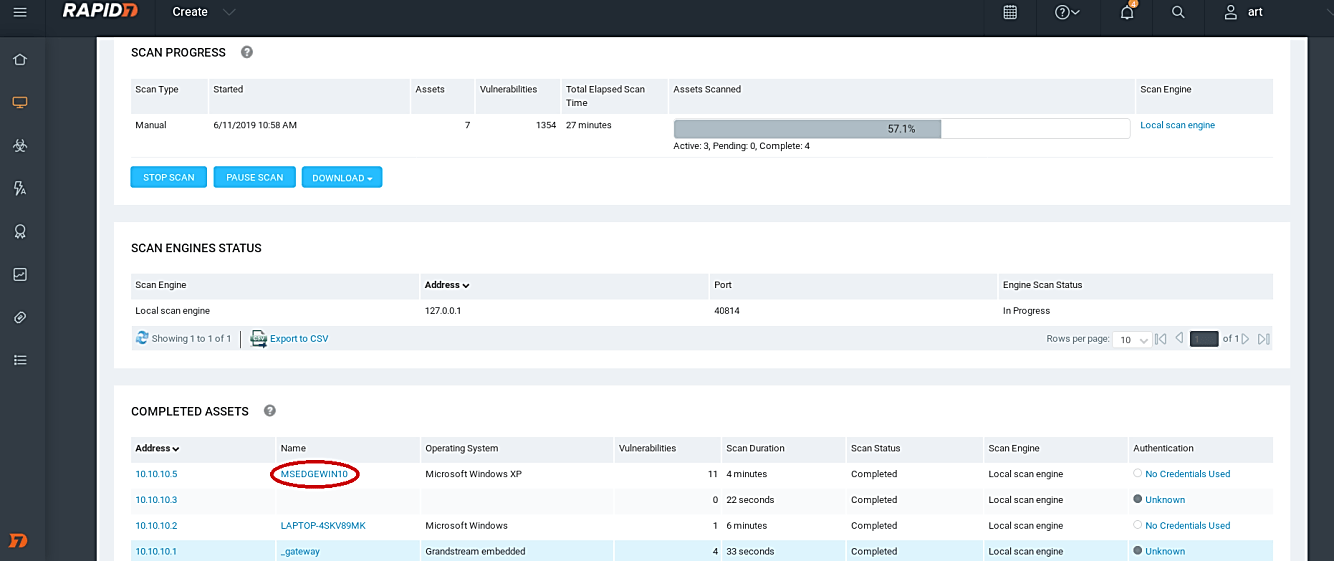
Click on one of the completed assets, and the Nexpose will display detailed information about that particular target.

To view all possible vulnerabilities in the network, click on the “Vulnerability” icon on the left pane. It will list everything based on their severity levels. This option can also show the exploits that are accessible in Metasploit and the ability expected to abuse this vulnerability, which means we can misuse this weakness by utilizing Metasploit. What’s more, it can also demonstrate whether the exploit has been published or not, so we can download those exploits from the exploit database.

After the whole scanning process is complete, we can save all these findings to show them to our clients or use them to perform further intrusion in our penetration testing. Click on the “Reports” icon from the left pane and give it a name in the “Name” field. Next, select your template type and save your report.
Nexpose will create a report and generate a direct link to access it. Click on the link to view the report.

Vulnerability scanners like Nexpose were intended to help security specialists to distinguish potential vulnerabilities in their networks and systems; however, the keen hacker can utilize them to recognize potential targets and their weaknesses. No more guessing which exploits to use, Nexpose and other vulnerability scanners can pinpoint not only the weaknesses but also the exploits used to hack them.
