OSINT-SPY - Hacker’s search engine
OSINT-SPY is a tool that helps in performing OSINT scans on several online resources and checking information for email, domain, IP address, and organization. It can be used by Infosec Researchers, Data Miners, Penetration Testers, and cybercrime investigators to find in-depth information about their target.
To download this tool, go to the “https://github.com/SharadKumar97/OSINT-SPY“ webpage.

Copy the downloadable link and clone it into the “/opt” directory.
Ex: (root@kali:/opt# git clone https://github.com/SharadKumar97/OSINT-SPY.git).
Navigate to the “OSINT-SPY” folder and install the tool using the “python” command.
Ex: (root@kali:/opt/OSINT-SPY# python install_linux.py).
We will need to generate API keys from several sources and integrate them with the configuration. Change your directory to “/modules” and open the “config.py” file with any text editor.
Ex: (root@kali:/opt/OSINT-SPY/modules# nano config.py).
At the moment, the tool supports the following sources:
Clearbit API: Register yourself at Clearbit and activate your account. Once you log in, you will find one section of the API. Copy the secret API Key and paste it inside the “config.py” file.
Shodan API: Sign up yourself at Shodan and activate the account. Login to Shodan, and you will find an API key in the overview tab. Copy the key and paste it inside the “config.py” document.
FullContact API: Register at Full Contact, and sign up by using your email, or you can Sign Up with Google. Once you log in, you will find the API Key on the dashboard. Just copy that key and paste it inside the “config.py” file.
VirusTotal API: Register yourself at VirusTotal. Once you log in, you will find the “My API Key” section in the profile menu. Copy the public API Key and paste it into the “config.py” file.
EmailHunter API: Register at Email Hunter. Once you log in, go to the API tab and click on the “EYE” icon to view your API Key. Copy your API Key to the “config.py” file.

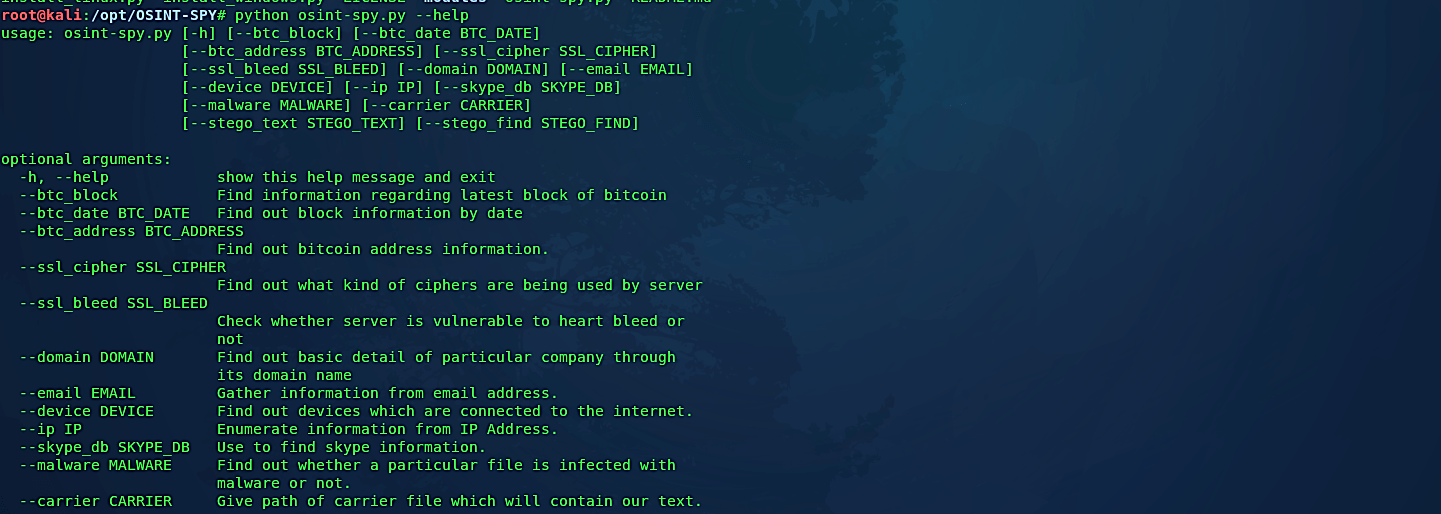
To start OSINT-SPY, use the “python” command and type the “- -help” option at the end to view detailed help and usage information.
Ex: (root@kali:/opt/OSINT-SPY# python osint-spy.py – -help).
Let’s perform a simple example and try to gather information from an email account. To do so, use the same command we used before but instead of the “ – -help” type “- -email” option and then provide the victim’s email address.
Ex: (root@kali:/opt/OSINT-SPY# python osint-spy.py – -email nxxxxxxxxxxw@gmail.com).

This tool will use the resources above and gather all possible information regarding the target.
OSINT-SPY is a very handy tool and easy to use. All you have to do is just have to pass values to parameters. Below, are some useful parameters that you might use.
- –btc_block: parameter gives you the information of the latest bitcoin blockchain. Ex: python osint-spy.py — btc_block
- –btc_date: parameter will give you information on the bitcoin blockchain from a given date. Ex: python osint-spy.py — btc_date 20170620
- –btc_address: will give you a piece of information about a particular bitcoin owner. Ex: python osint-spy.py –btc_address 1DST3gm6JthxhuoNKFqXrdpzPFfz1WgHpW
- –ssl_cipher: will show you all the ciphers supported by the given website. Ex: python osint-spy.py — ssl_cipher google.com
- –ssl_bleed: will find out whether the given website is vulnerable to heartbleed or not. Ex: python osint-spy.py –ssl_bleed google.com
- –domain: will give you in-depth information about a particular domain including whois, DNS, ciphers, location and so more. Ex: python osint-spy.py — domain google.com
- –email: will gather information about the given email address from various public sources. Ex: python osint-spy.py –email xxxx@yyyyyyyyy.org
- –device: will search for a given device from shodan and will list out all the available devices on public IP. Ex: python osint-spy.py –device webcam
- –ip: will gather all the information of the given IP Address from public sources. Ex: python osint-spy.py — ip 127.0.0.1
- –skype_db: will find out all the contacts and message history from the given skype database. This can be useful for forensics investigators. In Windows, the Skype database can be found in AppData\Roaming\Skype\(Your username)\main.db and in Mac OSX, the database can be found in /Users/(Your mac user name)/Library/Support/Skype/(your skype username)/main.db. Ex: python osint-spy.py –skype_db main.db
- –malware: will send a given piece of the file to virustotal and will give you a result whether a given file is malware or not. Ex: python osint-spy.py –malware abc.exe
- –carrier and –stego_text: is used to hide text behind any image. –carrier will specify the image behind which you want to hide the text. –stego_text will specify the text you want to add. Ex: python osint-spy.py –carrier image.jpg –stego_text This_is_secre_text
- –stego_find: will find out hidden text behind any image. Ex: python osint-spy.py –stego_find hidden.jpg
