post-exploitation techniques part-6
Scanning for open ports through pivoting (post-exploitation techniques part-5)
The Metasploit framework incorporates some port scanners that could be used in circumstances where we have to compromise a framework that is behind a NAT Firewall, and we need to complete a port sweep to whatever is left of the system, or we are merely performing an internal penetration test.
In this example, we will perceive how we can play out a basic TCP port sweep by utilizing the modules of the Metasploit called “auxiliary/scanner/portscan/tcp” on one of the discovered live hosts (10.10.11.4).
Ex: (msf post(windows/gather/arp_scanner) > use auxiliary/scanner/portscan/tcp).

Scanners and most other auxiliary modules utilize the “RHOSTS” choice rather than “RHOST.” RHOSTS can take IP ranges (10.10.11.1–10.10.11.20), CIDR ranges (10.10.11.0/24), multiple ranges separated by commas (10.10.11.0/24, 10.10.10.0/24), and line-separated host list records (file:/tmp/hostlist.txt).
As a matter of course, the majority of the scanner modules will have the “THREADS” value set to “1”. The “THREADS” value sets the number of simultaneous threads to utilize while scanning. Set this incentive to a higher amount to accelerate your outputs or maintain it lower in control to diminish network traffic yet make sure to stick to the following rules:
1. Keep the THREADS value under 16 on local Win32 frameworks.
2. Hold THREADS under 200 when running MSF under Cygwin.
3. On Unix-like operating frameworks, THREADS can be set as high as 256.
Configure all necessary options as it is shown in the screenshot and run the auxiliary. This module will list all open ports on that particular target.

As you can see, Metasploit’s built-in scanner modules are efficient in finding open ports for us. It’s just another awesome tool to have in your arsenal if you happen to be running Metasploit on a system without Nmap installed.
Compromising the target device through pivoting
The target device that we scanned previously has a few ports open. To compromise a target through one of those ports, we need first to perform some information gathering techniques to find their vulnerabilities.
Let’s take a look at port 22 (SSH) and try to find what version it runs using the “ssh_version” auxiliary.
Ex: (msf auxiliary(scanner/portscan/tcp) > use auxiliary/scanner/ssh/ssh_version).
Set all the necessary options and run the module.

Once the process started, it’ll try to find the SSH version.

As it is shown in the screenshot, we found the version of the service that runs on port 22 (ssh-2.0-openssh_4.7p1). Based on this information, you can search for vulnerabilities on Google and compromise your target further. In this tutorial, we’ll use the “ssh_login” auxiliary to crack the user name and password of the SSH service.
Ex: (msf auxiliary(scanner/ssh/ssh_version) > use auxiliary/scanner/ssh/ssh_login).
Set the “RHOST” option to 10.10.11.4 and “USERPASS_FILE” to the default “userpass” file that comes preinstalled with Kali Linux located in (/usr/share/metasploit-framework/data/wordlists/root_userpass.txt). You can also use any available wordlist by providing a direct location to that file. If you want to see live outputs, you may set the “VERBOSE” option to “true.”

The cracking process may take a while, and the success depends on how good your wordlist is.
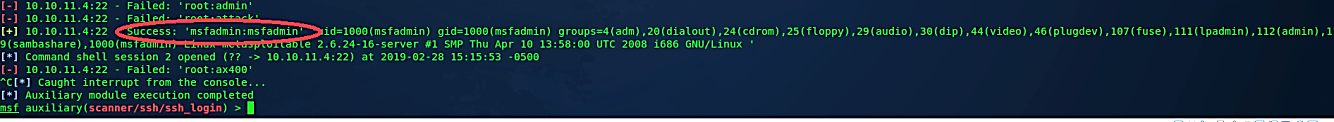
After a few minutes, we successfully managed to get the default username and password for the SSH service. Now let’s put that information in the auxiliary module that we used previously. Set the “USERNAME” option to “msfadmin,” set the “PASSWORD” option to “msfadmin,” and lastly, unset the option “USERPASS_FILE” and run the module.


Now we have an open shell in session “4” waiting for us to be connected. To interact with it, type “sessions -i 4,” and you will be presented with a compromised target shell.
You must be very familiar with the meterpreter at this stage. We hadn’t gone over each and every command in this suite, but we had used the one that was most important. Since Meterpreter is constantly updating, you should explore and enjoy the rest of this suite. It has a ton of support from developers. If you’ve mastered the fundamentals, you can begin writing your own scripts, or at the very least be comfortable with new scripts. If you want to learn more about the structure of the meterpreter and how it functions, you can get the documentation for the meterpreter from Rapid 7.
