Recon-ng - Web application reconnaissance
Recon-ng is a full-included Web Reconnaissance system written in Python. Complete with autonomous modules, database association, worked in comfort capacities, intuitive assistance, and command completion, Recon-ng provides a great environment in which open-source web-based surveys can be conducted quickly and thoroughly.
Recon-ng has a look and feels similar to the Metasploit Framework, reducing the learning curve for leveraging the framework. However, it is quite different. Notwithstanding, it is very extraordinary. Recon-ng isn’t planned to rival existing structures, as it is intended only for open-source electronic surveillance.
This tool comes preloaded in Kali Linux. So type “recon-ng” in the terminal, and you should now be up and running with the Recon-NG console loaded.
Ex: (root@kali:~# recon-ng).

To list all available recon modules, type “show module.”
Ex: ([recon-ng][default] > show modules).
A module is a definitive task that recon-ng will execute based on the parameters you provide. The Recon category has the most modules so far.

Let’s perform a “whois” survey on a website. For this, we need to find a module first, so use the “search” command.
Ex: ([recon-ng][default] > search whois).

Once you find the module use it by typing the “load” command and add the module name.
Ex: ([recon-ng][default] > load recon/domains-contacts/whois_pocs).
To view all editable options for this particular module type “show options.”
Ex: ([recon-ng][default][whois_pocs] > show options).
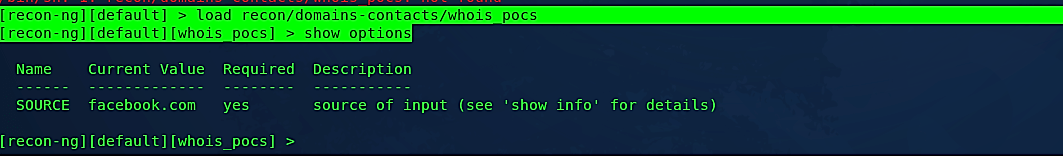
Next, set the “SOURCE” information and type “run” to begin whois reconnaissance.
Ex: ([recon-ng][default][whois_pocs] > set SOURCE yahoo.com
[recon-ng][default][whois_pocs] > run)

Recon-ng is a useful asset that can be additionally investigated by glancing through the rundown of modules above. The assistance inside the support is precise, and with a touch of playing around, it won’t take long to turn into a specialist. When you begin to turn out to be progressively acquainted with the format of the instrument, you will find choices, for example, workspaces that enable you to fragment dependent on association or system. The ascent of bug bounties allows you to play with new devices and investigate Organizations’ Internet confronting footprint.
