Red Hawk - web application scanner for recon
Red Hawk is a PHP-based web application scanner utilized for information gathering reasons. The information-gathering undertakings that can be accomplished with the Red Hawk instrument cover fundamental web filtering, WHOIS record, Geo IP information, Banner data, DNS record, sub-domain data, reverse IP query, MX record, bloggers explicit information, and WordPress scanning.
In the fundamental web filtering task, Red Hawk gets data like IP address, Content Management System (CMS) recognizable proof, server data, and Cloudflare location. The subdomain scanner gets subdomains and their IP data. The blogger’s clean sweep covers the information that can be valuable in dissecting the web application from an optimization point of view. It includes information about page authority, domain authority, Alexa ranking, social links, and HTTP response of the web pages.
WordPress scanning includes WordPress version detection, WordPress sensitive files lookup, and scanning vulnerabilities that are associated with WordPress versions. Aside from these information-gathering highlights, Red-Hawk has an SQLi scanner that gets links and parameters that might be vulnerable against error-based SQL infusions.
Visit the following GitHub “https://github.com/Tuhinshubhra/RED_HAWK” page, and copy the downloadable link.

Clone Red-Hawk to the “/opt” directory.
Ex: (root@kali:/opt# git clone https://github.com/Tuhinshubhra/RED_HAWK.git).
Since this tool is written with PHP, you can run it from the terminal by typing “php,” followed by the application file name.
Ex: (root@kali:/opt/RED_HAWK# php rhawk.php).
On the welcome page, Red-Hawk will ask us to provide a web application address and communication protocol, whether it is HTTP or HTTPS.
Once the information is provided, Red-Hawk will load all the scanning modules, as shown in the following screenshot.

We currently have alternatives to what we might want Red-Hawk to search. We will go with option “0” and perform a standard survey. As mapping out our target site is one of the initial phases in pen-testing, using Red-Hawk can quickly help speed up this process by having these tools in one place.

We can choose any scanning module by composing its succession number in the terminal. For example, we can select the Whois filtering module by composing its succession number “1” in the terminal, as appeared in the accompanying screenshot.

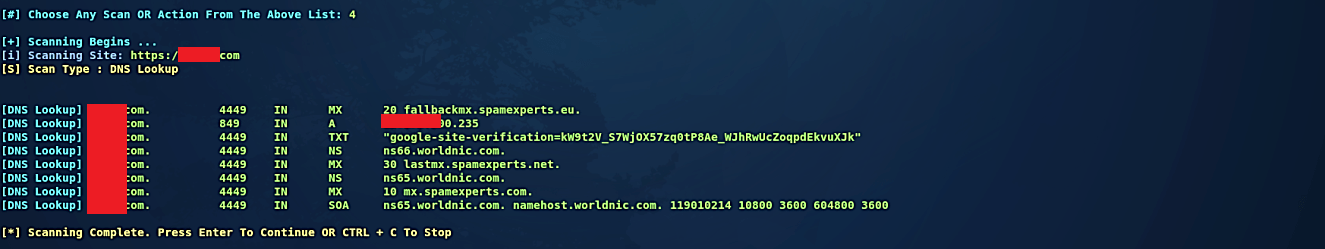
Similarly, we can perform a DNS lookup by specifying the option “4,” and it will show you all DNS records used by the target website.
Aside from these data gathering modules, Red-Hawk has a SQL vulnerability scanner that discovers links with conceivable error-based SQL vulnerabilities. The potential vulnerabilities can be confirmed with the guide of other database infusion apparatuses like Sqlmap.
