Replicating websites with HTTrack and harvest credentials
The Social-Engineer Toolkit (SET) is an open-source pen-testing system for Social-Engineering attack strategies. It was made and composed by Dave Kennedy, the organizer of TrustedSec. SET has various custom assault vectors that enable you to create a trustworthy assault in a small amount of time. Let’s take a look at how to run certain types of attacks and avoid getting detected by any anti-virus protection.
In this tutorial, we will show you how to clone any website with the “HTTrack” tool and use it later on in social engineering attempts.
HTTrack is a free and straightforward to-utilize offline browser utility. It enables you to download a World Wide Web webpage from the Internet to a local directory, constructing all registries recursively, getting HTML, pictures, and different records from the server to your PC. HTTrack organizes the first site’s relative connection structure. It can likewise refresh a current reflected website, and resume interrupted downloads. HTTrack is entirely configurable and has a coordinated assistance framework.
To use this tool, go to “Applications/03-Web Application Analysis” and click on “httrack.”

It will load the usage and help the manual page of HTTrack. We suggest you spend some time and read the manual; hence, it provides valuable information regarding the tool.
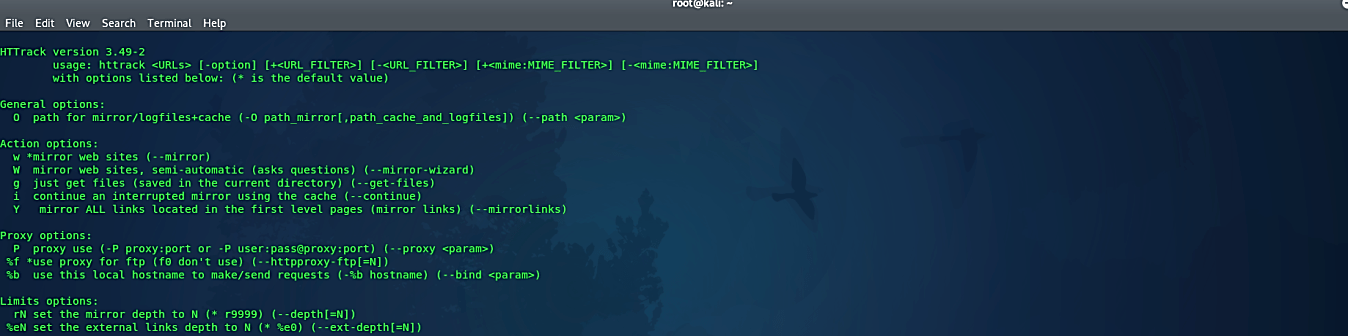
Type “httrack” and hit “Enter,” you’ll be asked to enter a project name. In this example, we will be replicating Yahoo’s login page, so we named it “Yahoo_Login.”

Open up your favorite browser and search for the website page you want to replicate and copy the URL link.

In the HTTrack framework, you’ll be asked to enter the URL and select a suitable action to mirror the website. Paste the URL link you copied and select the second option, “Mirror Web Site(s) with Wizard.”

For the “Ready to launch the mirror?” option, type “Y” and hit “Enter” to start the replicating process.

When the whole process is complete, you’ll have a new folder called Yahoo in the “Home” directory. This folder contains all necessary packages to run the replicated website offline.

Go into the Yahoo folder and run the “index.html” file to make sure that the website you replicated was successful.

As you can see in the image below, the replication of the website was successful, and all the hyperlinks in the site work as they are supposed to work.

Now, it is time to use some social engineering skills and fool our victim to compromise his/her computer.
For this, we’ll be using the SEToolkit form “Applications/13-Social Engineering Tools/SET”.

Once you launched the tool, you’ll be presented with a main menu option. Select option “1” to list all available social engineering attack options.

Since our attack is based on the website attack vector, select option “2” to view all attack methods.

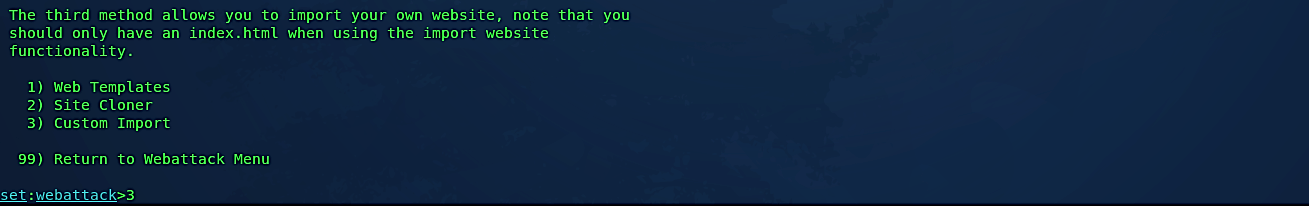
From the list of attack methods, we’ll be using the third option, which is the “Credential Harvester Attack Method.”

Next, select option “3” to import our custom replicated website and hit “Enter.”
Set your IP address for the POST back in Harvester and provide the full path to the folder of the replicated website where the “index.html” file is located. In our example, it is located in the “/root/Yahoo/Yahoo_Login/” directory. If the “index.html” file is found by the tool, you’ll be asked whether to copy the entire folder or just “index.html.” Select option “2” to copy the whole folder. Next, you’ll be prompted to provide an original URL link to the website you replicated. Copy the URL of the site and paste it on the SEToolkit page.

If everything is set correctly, you should be able to run the replicated website online and harvest credentials. To test whether it works or not, type your IP address in the URL search bar and hit “Enter.”

As you can see in the screenshot, whenever the victim visits our webserver, he/she will be redirected to the fake Yahoo page, which looks and functions as the original Yahoo login page. To make our link less suspicious and more legitimate, we can use some online link shortener services like “bit.do.”
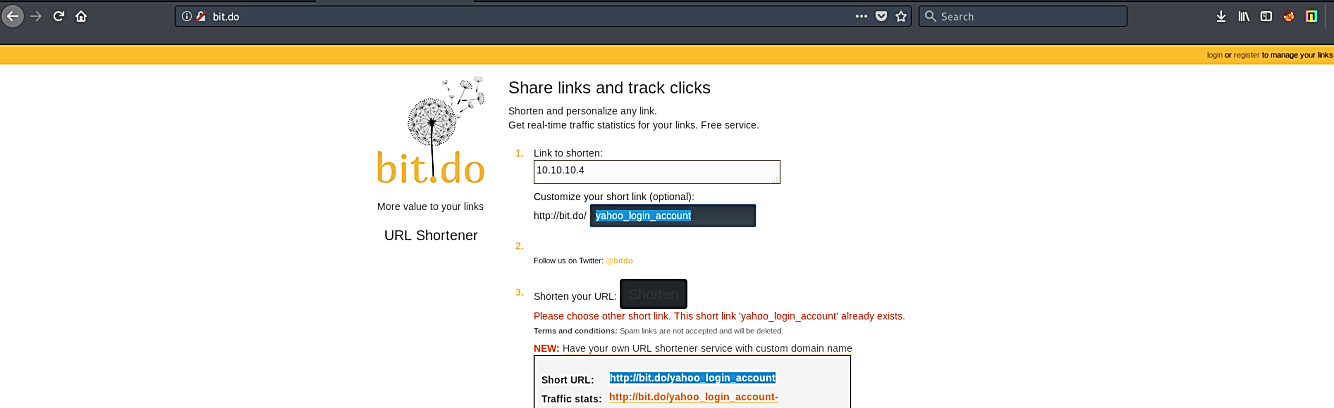
Now, our new (http://bit.do/yahoo_login_account) link looks much better and less suspicious, so we can send it to our victim and wait for the results. Once the victim visits the page, puts the credentials, and hits “Enter,” it’ll redirect to the original login page. The victim will not notice anything and will think that he/she mistyped the password, so the victim will try to re-login again.

On the other hand, the attacker will receive harvested information regarding the victim’s credentials and list them on the SEToolkit page.

As a penetration tester, you might be asked by clients to conduct social engineering attacks on their own workers in order to see whether they are adhering to the company’s policies and security measures.
Employee education is critical because, even though the company uses the most up-to-date anti-phishing tools, workers can be the weakest link by clicking on a link from an unknown source. They must be aware of what constitutes phishing, not to click on any links or provide personal information, and to always check the address bar and everything that does not seem to be usual in order to avoid being scammed.
Always keep in mind that while a system administrator can update and patch a computer or network, there is no such thing as a patch for human unawareness.
