Scan your network with Unicornscan
Unicornscan is expected to give a specialist a powerful interface for bringing an upgrade into and estimating a response from a TCP/IP empowered gadget or system. A portion of its highlights incorporates asynchronous stateless TCP filtering with all varieties of TCP banners, asynchronous stateless TCP banner grabbing, active/passive remote OS, and application and component identification by analyzing responses. In the wake of getting the response, the TTL value is determined for each port and accordingly recognizing the operating framework. For instance, if the ttl=128, the operating system is Windows, etc.
Pentesters utilize this apparatus when standard port examining doesn’t function as the objective may have empowered port scanning discovery or has empowered IDS/IPS or honeypots. One exciting element of this tool is that it utilizes various strings to convey packets and to get them in contrast to other port scanners.
It comes pre-installed with all Kali Linux versions; to start the tool, type “unicornscan” in the terminal.

Let’s perform a TCP scan using immediate mode (-I) to display things as we find them on the specific interface (-i) and use the TCP SYN profile (-mT).
Ex: (root@kali:~# unicornscan -v -I -i eth0 -mT 10.10.10.7).
This command will try to find all open TCP ports with the running services.
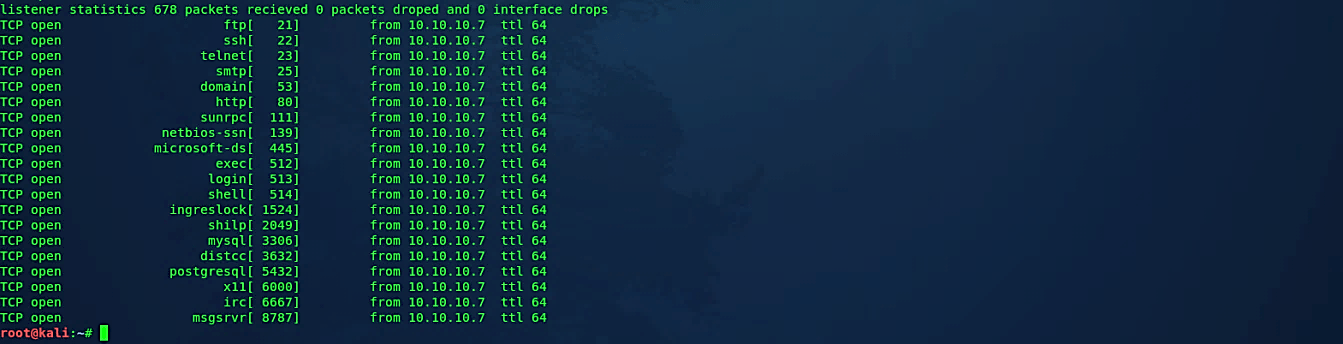
The same scanning technique can be performed using the UDP scanning profile to determine open UDP ports.
Ex: (root@kali:~# unicornscan -v -I -i eth0 -mU 10.10.10.7).

While performing network scanning with unicornscan, turn on Wireshark also to see the packets going out. You can see the pattern which unicornscan sends out.
