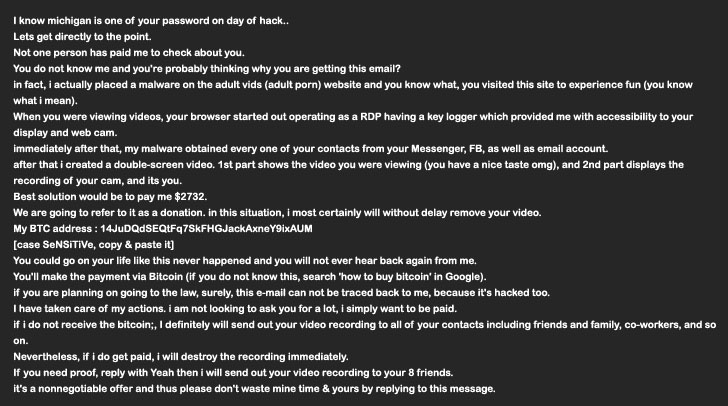
Sextortion emails demand $2,732 in Bitcoin from a new MyloBot variant
- February 15, 2022

A new release of the MyloBot malware has been discovered to distribute harmful scripts which are used to generate sextortion emails requesting $2,732 in crypto currency from victims. MyloBot, which was initially discovered in 2018, is said to include a variety of complex anti-debugging features and replication strategies for trapping infected machines in a botnet, as well as removing traces of rival malware.
It used a 14-day postponement prior to actually trying to access its command-and-control servers and the ability to execute malicious binaries straightforwardly from memory to avoid detection and stay under the radar. To get through process-based defenses, MyloBot uses a method called process hollowing, in which the malicious code is inserted into a suspended and hollowed process. This is accomplished by unmapping the live process’ memory and substituting it with the arbitrary code to be executed, in this case a decoded resource file.
In a study, Minerva Labs researcher Natalie Zargarov stated, “The second stage executable then creates a new subdirectory under C:ProgramData.” “It looks for svchost.exe in a system directory and suspends its execution. It injects itself into the created svchost.exe process via an APC injection mechanism.”
APC injection is a process injection method that, similarly to process hollowing, allows the installation of malicious code into an established victim process via the asynchronous procedure call (APC) queue. The second stage of the intrusion is gaining a presence on the compromised host and using it as a stepping stone to initiate communications with a remote server in order to fetch and execute a payload, which then decodes and runs the final-stage malware.
This malware is intended to exploit the endpoint in order to send extortion emails referencing the victims’ online activities, such as browsing pornographic websites, and threatening to expose a videotape reportedly obtained by breaking into their computers’ webcam. According to Minerva Labs’ research of the malware, it has the ability to download additional files, implying that the malicious attacker has left a backdoor for future attacks.
“This threat actor took great pains to deliver the malware and keep it undetected, just to deploy it as an extortion mail sender,” Zargarov explained. “Botnets are harmful simply because of this yet-to-be-identified threat. It may just as easily infect all affected endpoints with ransomware, malware, worms, or other dangers.”
