Social engineering with Blackeye
Blackeye is a tool scripted in the shell to perform phishing assault inside and outside LAN joined with ngrok. It can be utilized in social-engineering-related pen-testing occupations. It might likewise prove to be useful for red team people when endeavoring to gather passwords that could be used somewhere else. Blackeye is a complete phishing tool yet with 32 web templates +1 customizable. This tool can collect IP and location information just by clicking the link.
To download this tool, visit the “https://github.com/thelinuxchoice/blackeye” page and copy the downloadable link.
Change your directory to “/opt” and use the “git clone” command to download the Blackeye.
Ex: (root@kali:/opt# git clone https://github.com/thelinuxchoice/blackeye.git).

Navigate to the “/blackeye” folder and type “bash blackeye.sh” to start the tool.
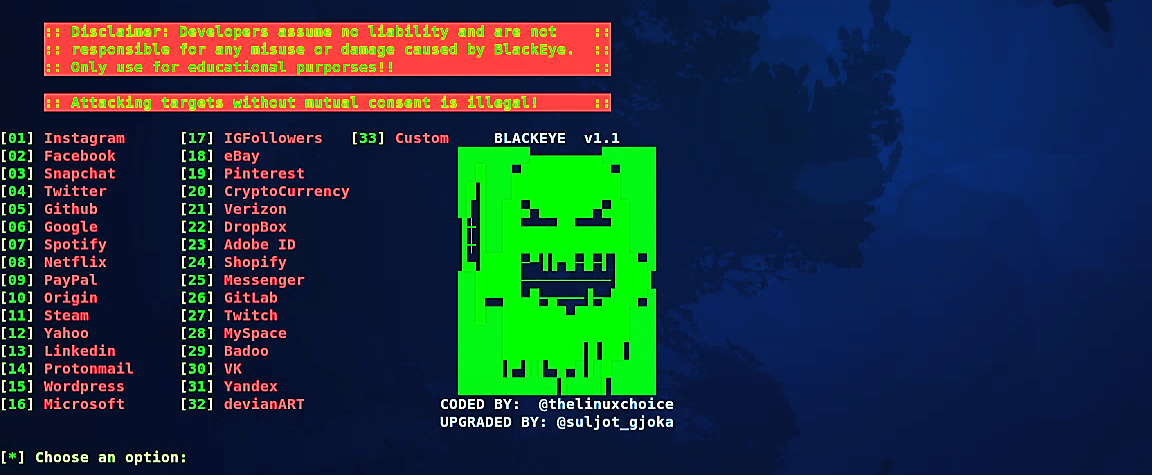
On the main page, you’ll be presented with the 32 most popular web templates. Select the one you like and hit “Enter” to continue. Here we chose option “8” for Netflix.

Provide your local IP address and hit “Enter” to start the PHP server. When anybody tries to browse your local IP address, they will be redirected to the Netflix login page. We suggest changing the IP address link to something less suspicious using some online URL shortener services.

Once the victim visits the page, puts the credentials, and hits “Enter,” it’ll redirect to the original login page. The victim will not notice anything and will think that he/she mistyped the password, so the victim will try to re-login again. But on the other hand, the attacker will receive harvested information regarding the victim’s credentials and list them on the Blackeye terminal page.

Note: The device works on LAN. “AnonuD4y” is taking a shot at changing the content to incorporate Ngrok services with it, so it works over WAN, yet it has a few issues with starting Ngrok. You can look at that form on GitHub. Additionally, you may think about “Modlishka.” It is a tool that can sidestep two-factor verification of sites, including Google services. You don’t have to clone templates. Modlishka works like an intermediary between you and the server that implies the server runs live. These apparatus are taking phishing techniques to the next level. To give it a try, check out the instructional tutorial on Modlishka from the “https://www.zdnet.com/article/new-tool-automates-phishing-attacks-that-bypass-2fa/” website.
