Social engineering with Social Fish
Phishing can be performed with the guide of various instruments in Kali Linux. Social Fish is a standout amongst the most incredible asset for phishing social media’s account and is created by Alisson Moretto. Since SocialFish isn’t an inbuilt apparatus in Kali Linux like SEToolkit, it must be downloaded from the official site of the GitHub page.
To download this tool, visit the “https://github.com/UndeadSec/SocialFish” page and copy the downloadable link.
Change your directory to “/opt” and use the “git clone” command to download the SocialFish.
Ex: (root@kali:/opt# git clone https://github.com/UndeadSec/SocialFish.git).
Next, navigate to the “/SocialFish” directory and install the required packages.
Ex: (root@kali:/opt/SocialFish# apt-get install python3 python3-pip python3-dev –y)

Then install everything that is in the “requiremnts.txt” list.
Ex: (root@kali:/opt/SocialFish# python3 -m pip install -r requirements.txt).
Change the mode of the “SocialFish.py” file to an executable (root@kali:/opt/SocialFish# chmod +x SocialFish.py) then run it using “python3” command following by user and password information (root@kali:/opt/SocialFish# python3 SocialFish.py root johdoesecurity).
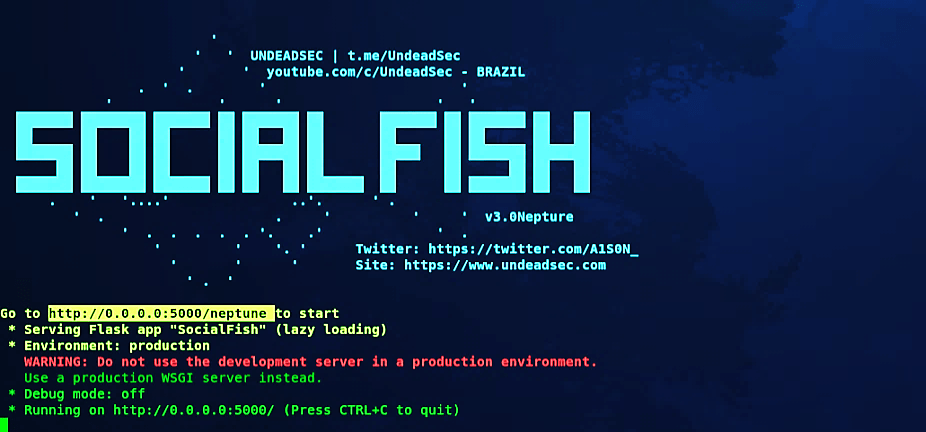
On the SocialFish main page, you’ll be given a local link, use this link to login to the SocialFish web-based page using the provided credentials above.

On the web page, first, provide the website link that you want to clone, second specify the website link that you want to redirect, and lastly, click on the lightning icon to start the attack.

Copy the attack URL and send it to your victim. Once the victim visits the page, puts the credentials, and hits “Enter,” the tool will redirect to the original login page. The victim will not notice anything and will think that he/she mistyped the password, so the victim will try to re-login again.
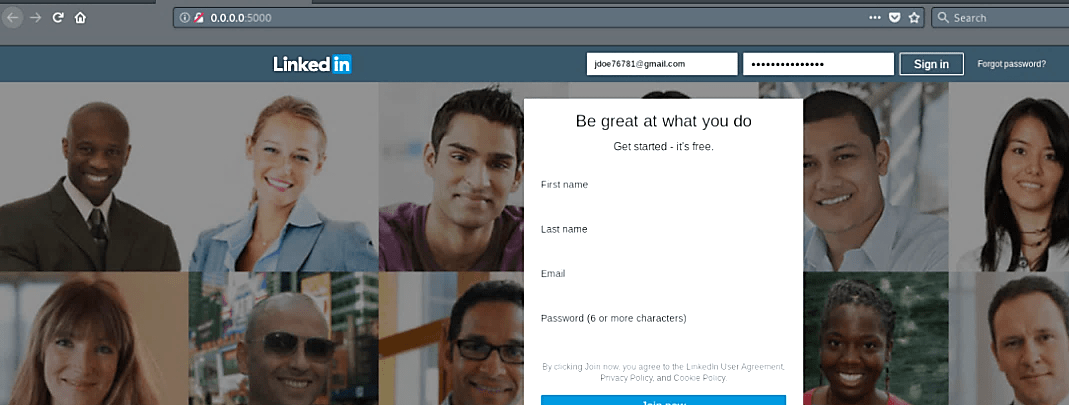
On the other hand, the attacker will receive harvested information regarding the victim’s credentials in the “POST LOG” section.

Click on “View” under the “POST LOG” tab, and it will redirect you to the page with all captured information.

Despite its numerous iterations, SocialFish remains an effective tool for building convincing phishing pages for social media websites. In this article, we won’t go into how to deploy SocialFish across a network, but as you can see in our example, the most difficult part of creating a believable fake page on the go is actually quite simple.
