Social engineering WPA/WPA2 Wi-Fi networks with “Fluxion”
Fluxion was first presented as the change of Linset. It’s a social engineering inspecting tool to gain WPA/WPA2 passphrase by using methods like Wireless Phishing or facilitating a Fake Access Point.
Fluxion is an exceptional tool that uses a WPA handshake, not just to control the behavior of the login page yet the functioning of the whole script. It jams the network and makes a clone AP with a similar name, alluring the detached client to re-join. Once the client re-joins the network, a fake login page will pop up, telling that the router needs to restart or load firmware and requests the router secret phrase to continue. The tool utilizes a captured handshake to check the secret phrase entered and keeps on jamming the objective AP until the right secret phrase is entered. Upon successful confirmation of the passphrase, the key will be logged, and Fluxion will shut down.
To download this tool, visit the “https://github.com/FluxionNetwork/fluxion“ page and copy the downloadable link.

Change your directory to “/opt” and use the “git clone” command to download the “fluxion.”
Ex: (root@kali:/opt# git clone https://github.com/FluxionNetwork/fluxion.git).
Navigate to the “/fluxion” folder and type the “./fluxion.sh” command to start the tool. You will be presented with the main page and prompted to select your language. Select one and hit “Enter” to continue.

Next, you will be asked whether you want to capture a handshake first or perform a Rogue AP attack. If you already captured a handshake, you can skip the second part. In this example, we will first obtain the handshake and then create a captive portal, so select the second option and hit “Enter.”
Now, to play out a successful Rogue AP assault, at least two wireless cards are required, one of them should support promiscuous mode and packet injection. Assortments of Wireless connectors are available; however, not all support what we need. We’ll be utilizing the Alpha AWUS036NH external wireless adapter for facilitating an Access Point and internal Wi-Fi for a de-authentication reason. Select option “1” to use an external wireless adapter.

This particular Alpha AWUS036NH external wireless adapter supports only 2.4GHz frequency so we can monitor only those adapters that run on 2.4GHz frequencies. Select option “1” to watch all channels in 2.4GHz.

Now a new window will appear on your screen, which is monitoring all the Wi-Fi channels. When your target Wi-Fi is listed in that window, hit “Ctrl+C” to stop the search.
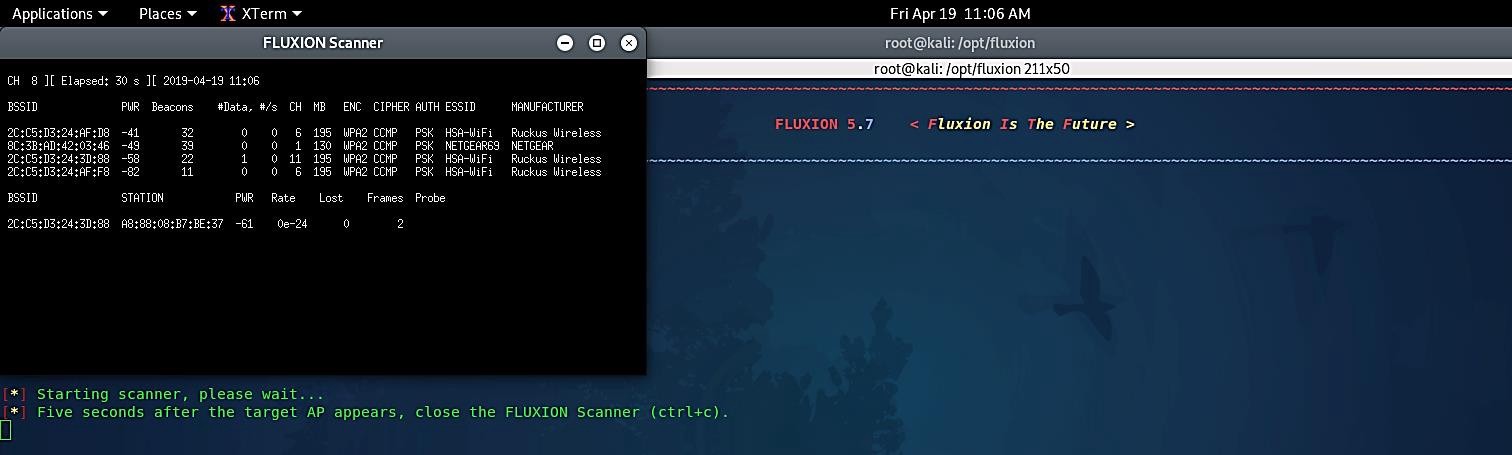
Once you exit out from the monitor window, you’ll be presented with the list of all available Wi-Fi around you. Select the one you are targeting and hit “Enter” to continue.

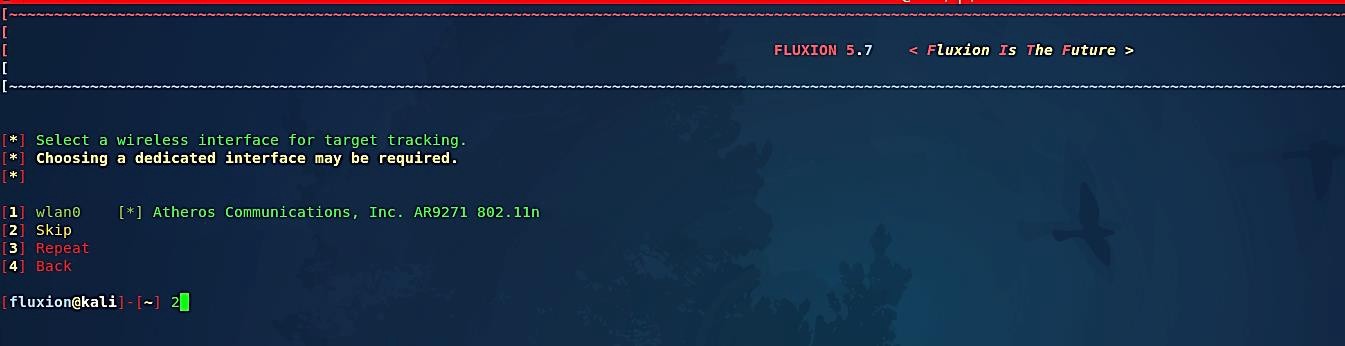
Then you’ll be prompted to select your external wireless interface for target tracking again; in this case, you may skip it by choosing option number “2.”
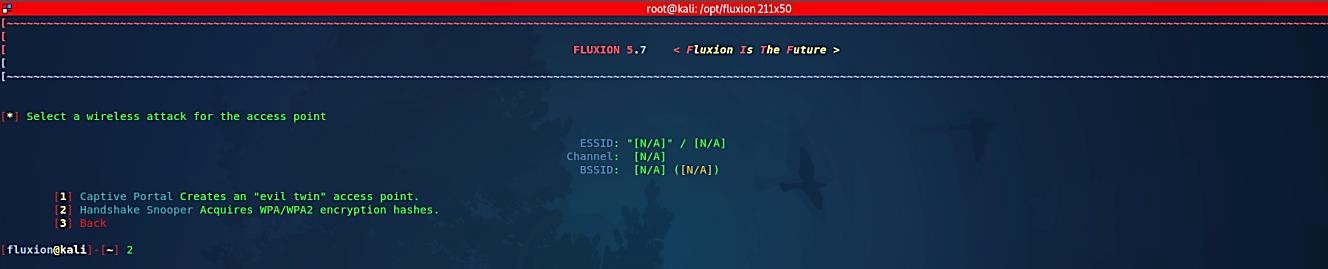
Select option “2” to de-authenticate our target Wi-Fi for a few seconds, so devices that were connected to the Wi-Fi can be disconnected and reconnected again. This way, we can retrieve a handshake.

Select a method of verification of the hash. In this example, we selected the option “1 pyrit verification” to verify the hash.

Now, choose the duration of how often the verifier should check for a handshake. Here we wanted to check it every 30 seconds.

Since our computer is not super-fast, we selected the option “2” for verification occurrence.

Once you selected your option and hit “Enter,” it will start the handshake snooper and try to capture the handshake.

While the snooper is doing its job, we can select another attack vector.

Now, it’s time to create an “evil twin” access point by selecting the “captive portal” option.

Since we are targeting the same access point, we can continue to stick with this target by typing “Y” when you are prompted.

Next, you’ll be asked to select your external wireless interface for target tracking again; in this case, you may skip it by choosing option number “2.”

Then select an interface to launch the Rogue Access Point. Make sure the adapter you use is powerful enough to throw signals on the long range.
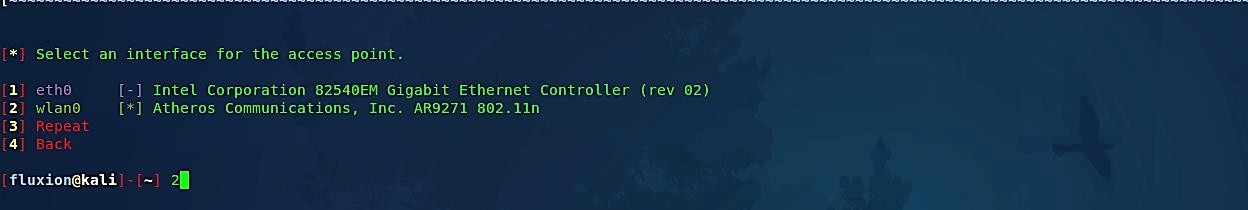
Depending on your wireless adapter chipset, you can select either hostapd or airbase-ng. Airbase-ng is slower than the hostapd but supports a broader range of wireless chipsets. Since hostapd supports our wireless adapter, we’ll go with hostapd by selecting option number “1.”

Next, you will be asked for a handshake. We’ve captured a handshake of target AP with Fluxion earlier. So, we’ll go with the option “1 Use hash found.”

Cracking the right password is an essential factor in all of this attack. We need to find the right key. For this, when anything will be entered into the fake page, it will be manipulated and matched against the correct hash derived from a handshake.
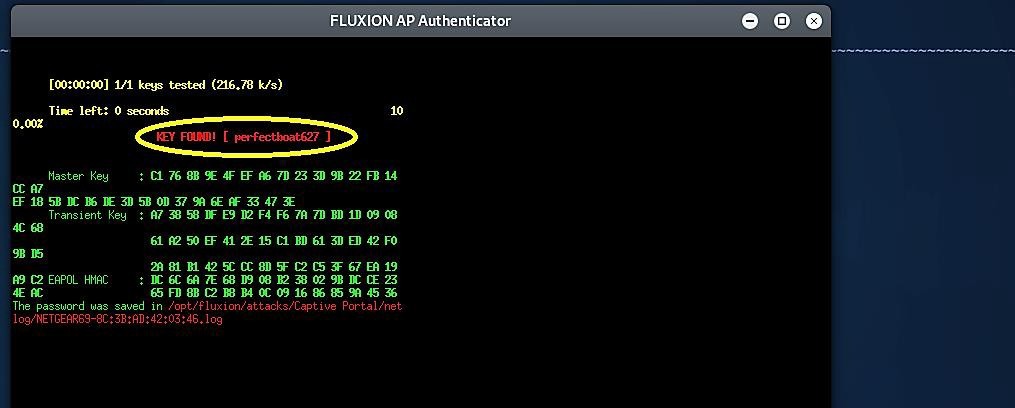
Upon successful cracking, the key will be printed on the screen, and Fluxion will stop. So, select one of the cracking software accordingly and choose a method of verification of the hash. In this example, we chose the option “1 pyrit verification” to verify the hash.

Next, create an SSL certificate for the captive portal by selecting option number “1.”

Select an internet connectivity type for the rouge network. Here we selected option “1,” which was recommended by Fluxion because we don’t want to provide the users with an internet facility.

Lastly, choose the fake login page from the available list to create a captive portal interface. Since our target access point is Netgear, we selected the option “51.”


Let’s play the victim role. If a user connects to our Rogue Access Point, the captive portal will be displayed, redirecting the user to the fake login page.

If the user enters the correct WPA/WPA2 passphrase in the fields, rogue AP will shut down, and the key will be printed on Fluxion’s screen.
People are always looking for free internet, so wifi password hacking has become common. However, due to technological advancements, hacking wifi and cracking passwords have become difficult challenges. As a result, users are strongly encouraged to secure their WiFi networks with a secure password that includes numbers, letters, and special characters, as they are difficult to crack, which will secure your wireless network from being hacked.
