Spear-phishing attack with Social Engineering Toolkit
Spear-phishing is an email trick focused on a particular individual, association, or business. Albeit frequently planned to take information for malignant purposes, cybercriminals may likewise mean introducing malware on a targeted client’s PC. If you’re looking for a way to communicate with an organization or get something to run on the inside, email is always the way to go. Since it is the internal door to an enterprise, it seems that phishing will continue to be a vector for quite some time.
Spear-phishing’s success is due to a mixture of technological and psychological factors. Since they are so specific, spear-phishing emails are difficult to identify. They appear to be regular business emails with regular business talk, making it difficult for spam detection systems to identify them as spam. Spear-phishers take advantage of this because you don’t want your spam filter to block legitimate emails, causing end users to become irritated and business processes to break down.
Spear-phishing is extremely difficult to detect if it is written with enough personalization, in the right language, and with the right message. Emails with a high level of personalization have a far higher level of authenticity. The more personal details a victim sees in an email, the more likely they are to believe it is genuine.
In this tutorial, we will show you how to use a spear-phishing attack vector with SEToolkit.
First, start the social engineering tool kit from the “Applications” menu.

Once the tool is launched, you’ll be presented with a main menu option. Select option “1” to list all available social engineering attack options.

Let’s now select option “1” from the menu and begin our spear-phishing attack.

On the following page, the SEToolkit will display some information on spear-phishing assault and the attack options. In this example, we selected option “2” to create a “FileFormat” payload.

After selecting the attack option, we need to specify the exploit type we want to utilize. In this tutorial, we will use the “Microsoft Word RTF pFragments Stack Buffer Overflow (MSMS10_087).” This exploit type will create a Word document that will overflow a buffer and enable us to put a listener or rootkit on the target’s PC. Type the option “6” and hit “Enter.”

Since we have chosen what kind of file we need to use in our assault, our following stage is to determine what sort of listener we need to leave on the victim framework. Here we chose the option “2) Windows Meterpreter Reverse_TCP.”

Set your local IP address and the port number you want to listen to, then hit “Enter” to continue.
The SEToolkit will create a malicious file as “template.rtf” and then ask you whether you want to rename it or not. If you want to change the name, select option number “2.”

Give it an appropriate name and hit “Enter.” Then select option “1” to send an attack email to your target.

Since we have made the malignant document, we now need to make the email. It is crucial, in case we’re to get the victim to open the file, the email must look real. SET prompts us whether we need to utilize a pre-defined format or a one-time-use email layout. Let’s pick option “2. One-Time Use Email Template” and create our own.

SEToolkit will prompt us for the subject of the email. Here we used “Sales Department Report.” Then it will ask us whether we want to send it in HTML or plain text. Type “p” for the plain text option. Next, write the body of the email and then press on “Ctrl + C” when you are finished. Finally, provide the “Send to” email address and hit “Enter.” When everything is configured correctly, SET will ask us whether we need to utilize a Gmail account or send it from our SMTP server. In most scenarios, we will need to use a Gmail account.
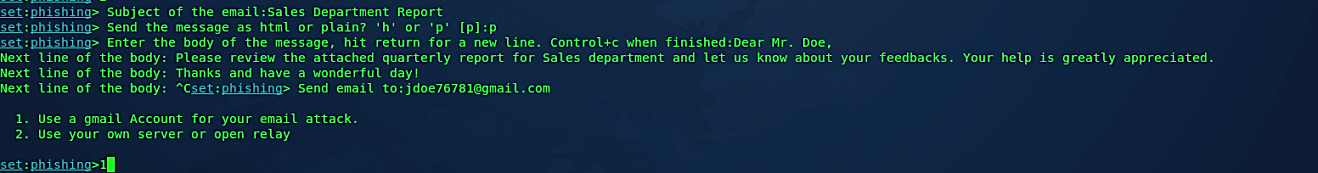
Type in your Gmail address; you need to make an anonymous email for this purpose, and SEToolkit will send the email you made with the malignant connection from this Gmail account.

Once everything is set correctly, the SEToolkit will automatically start the Metasploit multi-handler listener for you and wait for incoming connections.

To combat the threat of spear-phishing, businesses should implement both technological and human controls. Companies should recommend phishing simulation exercises, user training, and providing an existing mechanism for users to report suspicious emails to the IT security team, in addition to standard controls such as spam filters, malware detection, and antivirus.
Simply marking emails as they come in at the gateway and placing ‘external’ in the subject line is one of the simple ways that companies can combat problems like business email compromise. This won’t actually deter an attack, but it will give end-users the impression that something isn’t quite right.
While user education and awareness are important in reducing the risk of phishing, the security department should also be active in protecting business processes to limit attackers’ windows of opportunity. It takes a delicate touch to get everyone on board with policies to better combat spear-phishing. Security practitioners must act more like team builders than policy dictators, and they must have a much better understanding of how the business operates and what the best approaches are for protecting it.
