Spying your targets using Vulcan keylogger
Vulcan is noxious programming that will infuse in your framework. It might show false alerts that your PC has been contaminated. The Keylogger Vulcan infuses into the Operating System to change authorization strategies and to adjust the library. Probably, Keylogger Vulcan was introduced by the client, not realizing that this program is vindictive. The appropriation of Keylogger Vulcan is identified with downloading counterfeit Windows updates, introducing third-party applications “supposedly” required to properly view a webpage or watch videos, clicking on ads or banners, downloading attachments, or receiving files through social media.
Keylogger Vulcan may show a warning message about debased Windows framework records. The removal of such documents may deliver unwanted error messages or crash your framework. All alert scan results or pop-up messages are fake. Keylogger Vulcan may likewise incapacitate another programming on your PC, like anti-virus security suites or the windows firewall. It is a protection mechanism. Also, such rebel programming may adjust your browser settings and hide, which makes the removal quite challenging for beginners.
Go to the “https://cyberoops.blogspot.com/2014/07/vulcan-logger-keylogger-free-download.html” and download the zipped file.

Extract the file and run the application. Provide your email address and a password to receive a keylogger report. You may specify the interval time on how often you should receive the email from Vulcan and add an icon to make the keylogger more convincing or alluring to click on it.

For this example, we used a “Minecraft” icon, which was downloaded from the “http://www.iconarchive.com” page.

In the “Extra Options” tab, you can craft your own “Error,” “Info,” or “Alert” message boxes to your preference.
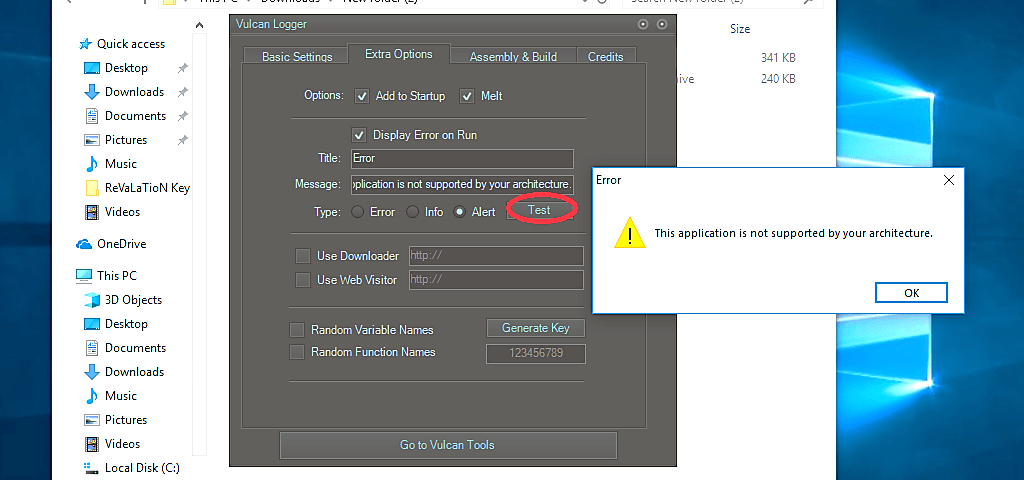
Under the “Assembly & Build” tab, you may put some detailed information regarding this build, or if you want to skip this, click on the “Random Generate” button, and it will generate some gibberish for you. Finally, click on the “Build” button to create a keylogger.

As it is shown in the screenshot below, we successfully created a keylogger that looks like a Minecraft application. Once the victim runs this application, he/she will be prompted with an error message that we crafted during the keylogger creation process.

From this point, we just need to be patient and wait for Vulcan to send us key logging reports.

Note: To remove this keylogger, you can use the “SpyHunter Malware Security Suite.” It is an automatic and fast removal method that is recommended for novice users.
Most modern keyloggers are viewed as real programming or equipment and are sold on the open market. Vendors and developers offer a significant rundown of cases where it would be legal and appropriate to utilize keyloggers, including:
Parental control: guardians can track what their youngsters do on the Internet, and can opt to be informed if there are any endeavors to get to sites containing adult or generally inappropriate content;
Envious mates or accomplices can utilize a keylogger to track the activities of their significant other on the Internet on the off chance that they presume them of “virtual cheating”;
Organization security: tracking the utilization of PCs for non-business related purposes, or the usage of workstations after hours;
Other security (for example, law authorization): using keylogger records to analyze and track incidents linked to the use of personal computers.
These tools can be used for other different reasons also. Moreover, any genuine keylogging system can, in any case, be used with pernicious or criminal expectations. Today, keyloggers are used to steal client information identifying with different online payment systems, and virus writers are continually composing new keylogger Trojans for this very reason. Besides, many keyloggers conceal themselves in the framework (for example, they have rootkit usefulness), which makes them completely fledged Trojan programs.
