Conceal Data With Steghide
Steghide is a steganography tool written in C++ for Linux and Windows, released under the GNU/GPL license. It gives clients a chance to exploit Windows Bitmap and JPEG pictures and Windows Wave and Sun/NeXT AU sound documents as cover files; any data may instead be utilized as the payload. Information in the payload might be encrypted by using the MCrypt and MHash libraries and compressed with Zlib library. The cryptography calculation in this tool, by default, is utilized Rijndael with 128-bit keys in cipher block chaining mode. It is regardless conceivable to choose any cryptography calculation among 18 potential outcomes, every one of which may work in different ways.
Debian Linux systems had the Steghide package in the official repository, so we can easily install it through Apt Package Manager or Apt-Get Package Manager.
Ex: (root@kali:~# apt install steghide).

Type the “help” command to view all available options that we can use to hide data.
Ex: (root@kali:~# steghide – – help).

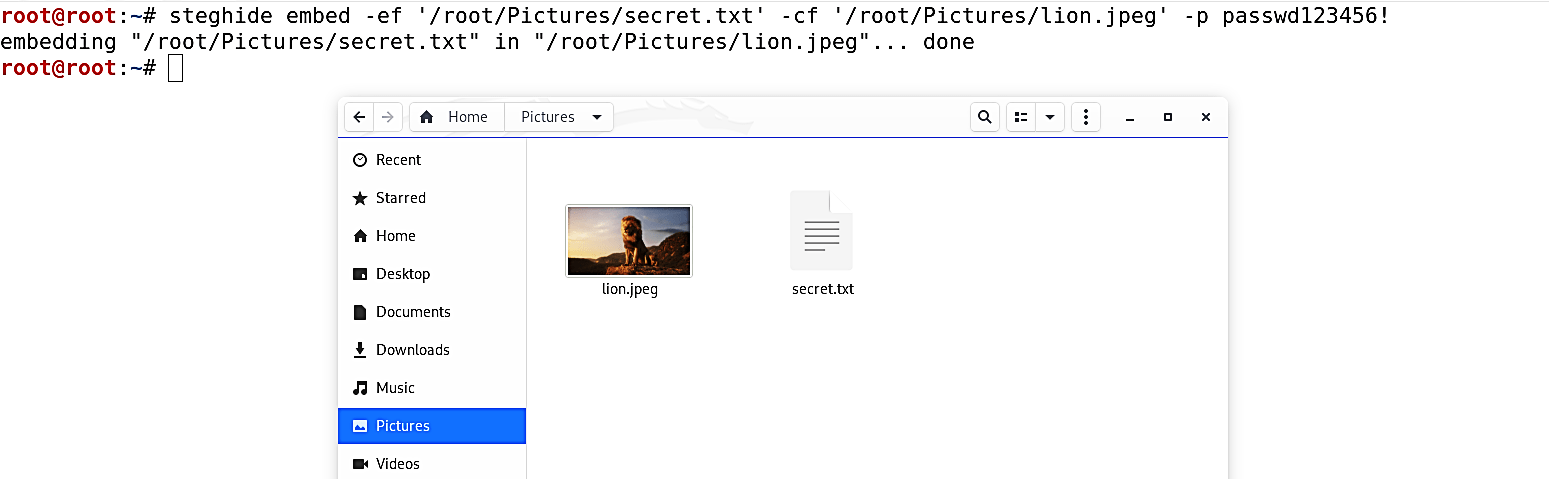
In this example, we are going to embed the “secret.txt” file into the “lion.jpeg” image file. Use the “embed” command to insert a secret text inside a cover file. Here, we will use the “-ef” (embed file) operator and specify the location of the hidden data file, and the “-cf” (cover file) operator to determine the location of the cover file. For cryptographic purposes, we can also protect our data with a passphrase (-p), which will be requested on extraction later on.
Ex: (root@kali:~# steghide embed -ef ‘/root/Downloads/secret.txt’ -cf ‘/root/Downloads/lion.jpeg’ -p passwd123456!).
Once you hit “Enter,” the image file “lion.jpeg” in the “/root/Downloads” directory will be altered and contain the hidden data.
To extract the hidden data, we are going to use the “extract” command. The usage is straightforward, and there are fewer parameters applied to the executable. First, we have to specify the name of the stego file (-sf) from which to attempt extraction, and then provide a passphrase (-p). It’s possible to choose the name of the output file; the extracted data will be saved by specifying the “-xf” operator.
Ex: (root@kali:~# steghide extract -sf ‘/root/Downloads/lion.jpeg’ -p passwd123456! -xf ‘/root/Desktop/extract.txt’).

Once you hit “Enter,” the hidden data will be extracted and saved into the location you specified where you could view and read quickly.
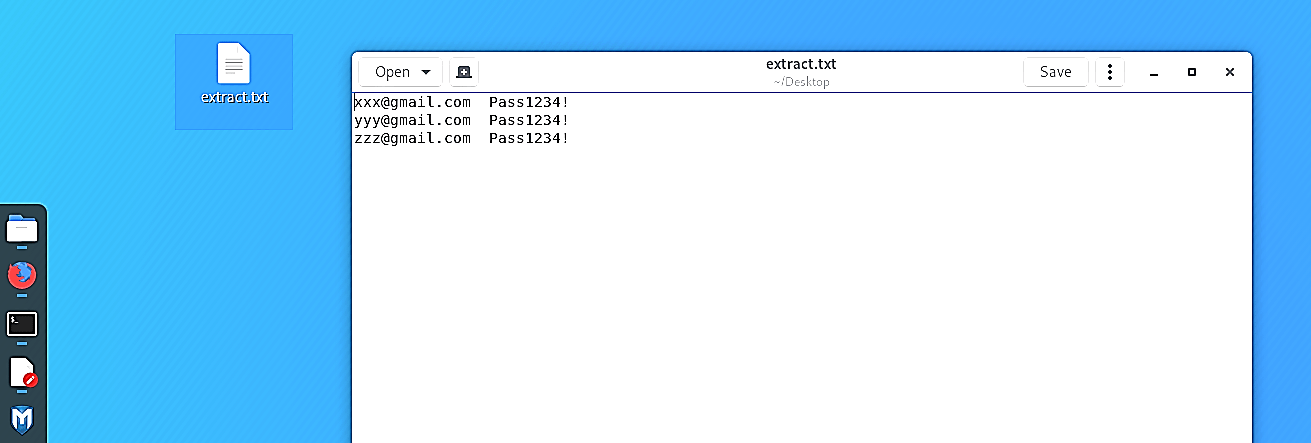
Image Steganography has numerous applications, particularly in the present modern, high-tech world. Privacy and anonymity are a worry for the vast majority on the web. Steganography takes into consideration two parties to convey furtively and secretly. It takes into account some ethically cognizant individuals to securely whistle-blow on inner activities; it considers copyright assurance on excellent records utilizing the message as a digital watermark.
One of the other fundamental uses for Image Steganography is for the transportation of high-level or top-secret documents between international governments. While Image Steganography has many legitimate applications, it can likewise be very evil. It very well may be utilized by hackers to send infections and Trojans to compromise computers, and by terrorists and different associations that depend on clandestine tasks to impart covertly and securely.
