Steganography technique with S-Tools
S-Tools is a program composed by Andy Brown. It is maybe the most broadly perceived steganography instrument accessible today. You can use BMP, GIF, and WAV file types to cover documents that hide the secret data. The simplicity of the tool lets you drag and drop files easily. S-Tools will conceal the secret message inside the cover file through random accessible bits. These available bits are resolved using a pseudorandom number generator. This nonlinear addition makes the presence and extraction of secret messages increasingly troublesome.
As we mentioned before, using this tool is very easy, drag and drop the cover image file, and then your secret message file on top of it.

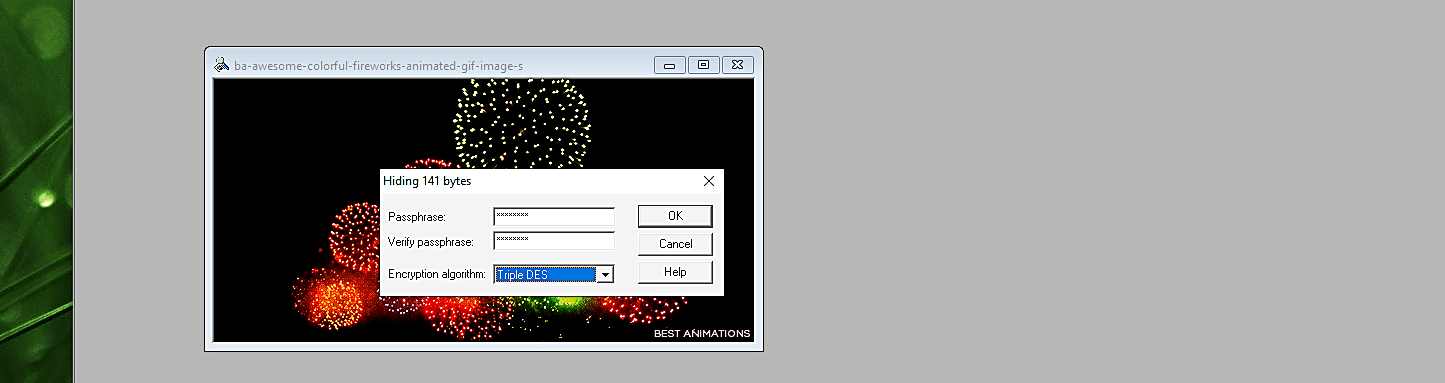
On the main display, a small window will pop up asking you to encrypt the stego file. Create a new password for the encryption and click on the “OK” button.
It will generate a new stego image. To save the stego file, right-click on the image and select the “Save as…” option.
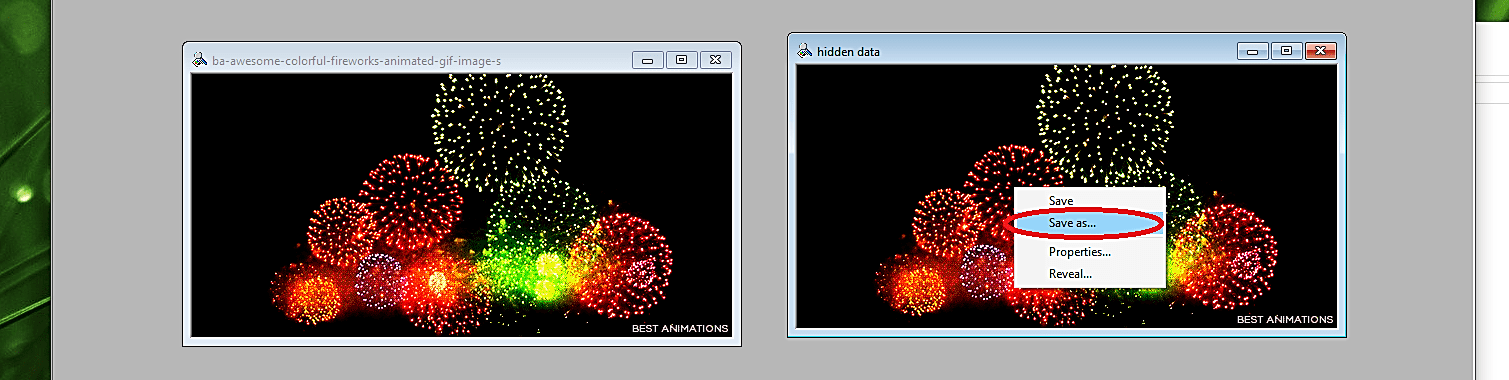
Specify the destination to save the stego image and click on the “Save” button.

To extract the concealed information from the stego image, run the S-Tools and then drag and drop the file into it. Right-click on the image and select the “Reveal…” option from the drop-down menu.
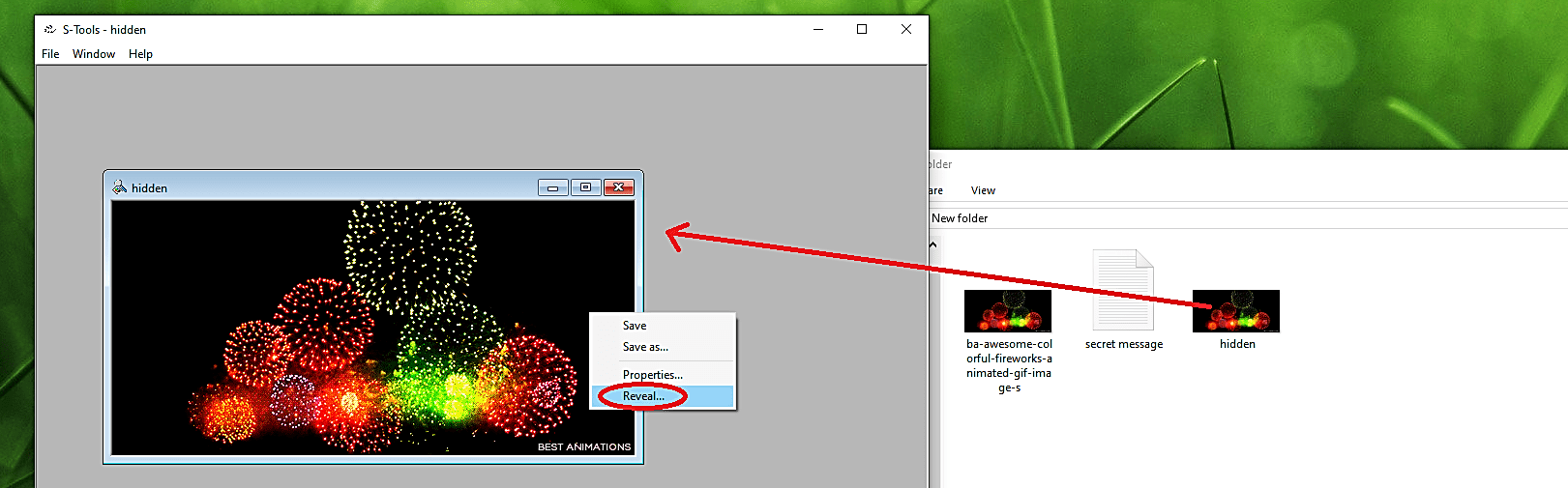
It will open up a “Revealed Archive” window displaying the secret message file name. Right-click on the file name and then select the “Save as…” option to save it in a location of your choice.

Once done, navigate to the specified location, and you will be able to view the secret message file.

S-Tools is 589 kb in size, making it small enough to fit on a floppy disk, and like many other steganography applications, leaves nothing in the way of a trace. S-Tools, on the other hand, has a well-known signature. The number of colors in the cover file is reduced to a minimum of 32 by S-Tools. Grayscale images are affected as a result. There is a more comprehensive description available, but it goes beyond the scope of this article.
To summarize, due to changes in the palette indices, a true grayscale image can no longer be a true grayscale image. As a result, this palette signature can be used to differentiate one image from another that contains a hidden file. The secret data, on the other hand, has a very good chance of remaining a secret due to the strong encryption that can be set.
