The comments feature of Google Docs has been used for spear-phishing attacks
- January 06, 2022

In December 2021, a new pattern in phishing attempts developed, with cyber attackers leveraging the Google Docs commenting functionality to send out emails that appeared legitimate. Since many people working or interacting remotely use Google Docs, the majority of the recipients of these emails are familiar with these messages. Because Google is being “misled” into distributing these emails, the odds of them being flagged as potentially dangerous are probably minimal.
The technique has been under continuous exploitation since October of last year, and while Google has moved to reduce the problem, it has not yet been totally addressed. This current initiative is gaining traction and is being closely studied by Avanan threat experts.
Hackers write a comment to a Google Doc in this malicious technique. The target is mentioned with an “@” sign in the comment. An email is sent to that person’s inbox as a result of this action.
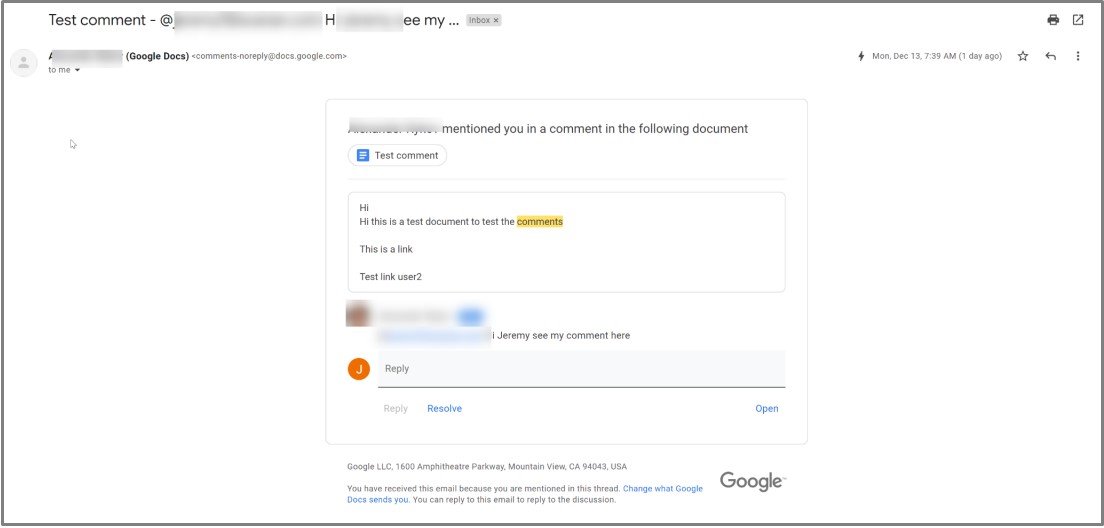
There are definitely no verifying procedures in place because the email comment can contain harmful hyperlinks that redirect to malware-dropping websites or phishing sites. Furthermore, the threat actor’s email address is not displayed in the notification, leaving the recipient with only a name to go on. This enables impersonation incredibly simple, while also increasing the hackers’ likelihood of succeeding.
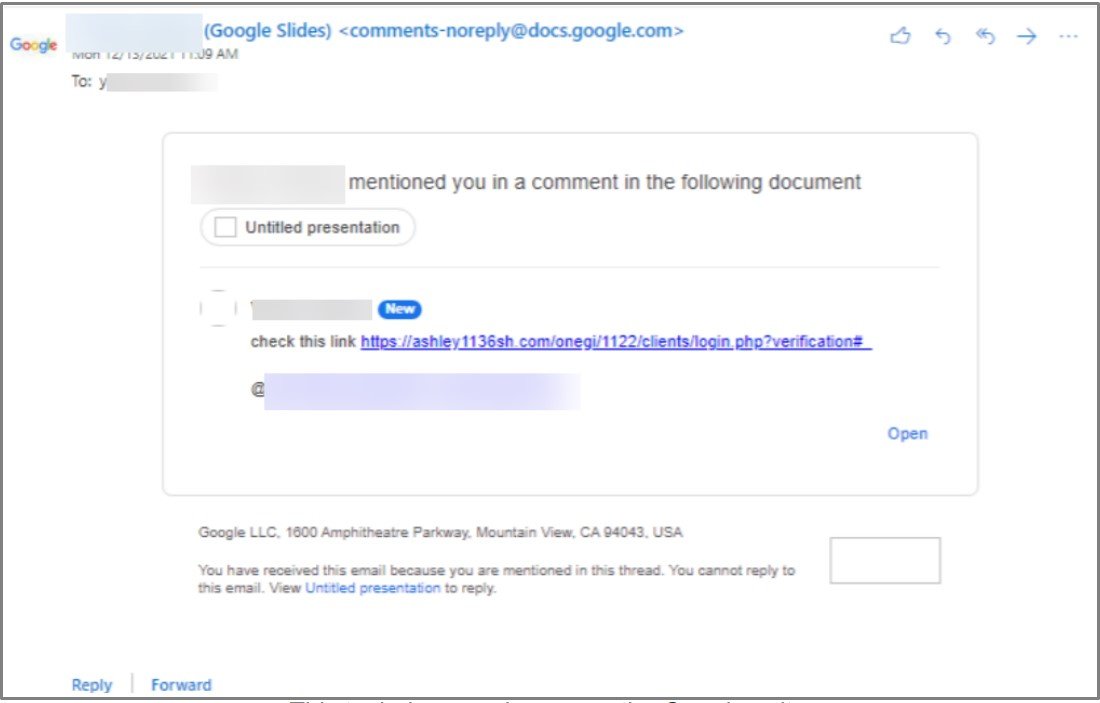
The same methodology may be used on Google Slide comments, and Avanan claims to have witnessed people using it on several Google Workspace features. To make matters worse, intruders don’t even need to share the document with their victims because simply referencing them triggers malicious notifications.
What you can do to mitigate?
The cyber attackers behind all these assaults tend to prefer Outlook users, although the intended audience is not restricted to them, according to Avanan. Over 100 Google accounts are being used in this continuing spear-phishing attack, which has now reached 500 inboxes across 30 firms.
The best method of prevention of this and related attacks is to do the following:
- Verify that the sender email corresponds to your friend’s.
- Beware of clicking on links contained in comments that you get via email.
- Implement extra security precautions for Google Workspace, such as stronger file-sharing policies.
- Use a phishing URL prevention web security product from a reputable vendor.
