Uniscan - Web application assessment tool
Uniscan is a vulnerability scanner that can search sites and web applications for different security issues like LFI, RFI, SQL infusion, XSS, and so on. It is an open-source tool and can be downloaded from the “https://github.com/poerschke/Uniscan” page.

Copy the downloadable link from GitHub and clone it to the “/opt” directory.
Ex: (root@kali:/opt# git clone https://github.com/poerschke/Uniscan.git).
Before starting the tool, we need to make a few changes in the “uniscan.pl” file. Open up the file with “nano” text editor (root@kali:/opt/Uniscan# nano uniscan.pl) and comment on the following line:
#use lib “./Uniscan”;
Then add two lines below the commented line:
use FindBin qw( $RealBin);
use lib $RealBin;

To start the uniscan tool, and view the help page, use the “perl” command.
Ex: (root@kali:/opt/Uniscan# perl uniscan.pl).

Let’s see this tool in action and perform directory check (-q), file check (-w), robot.txt check (-e), dynamic checks (-d), and static checks (-s) on the target URL (-u) of your choice.
Ex: (root@kali:/opt/Uniscan# perl uniscan.pl -u http://10.10.10.10/ -qweds).
Once you hit “Enter,” uniscan will begin the process and try to find all available vulnerabilities and misconfigurations of the target website.
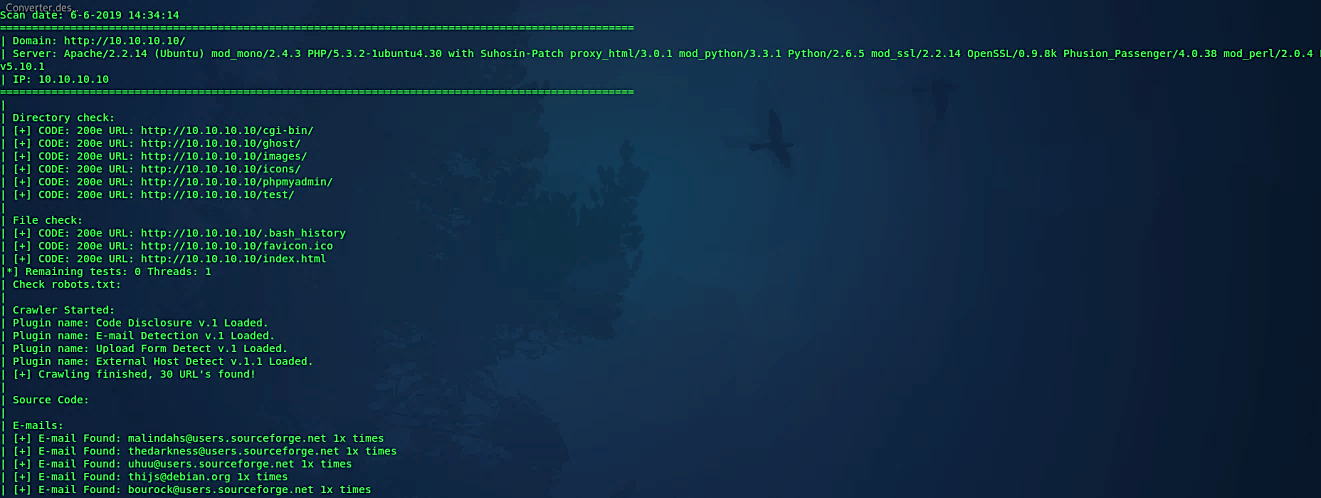
Uniscan has a text or CLI scanner as well as a graphical user interface. You can use either, but I noticed that CLI was a little quicker. Still, I may be mistaken.
