Use “Cain & Abel” to capture the user credentials
“Cain and Abel” is a password recovery software for Microsoft Windows. It can recover numerous sorts of passwords using techniques like network packet sniffing, breaking different secret word hashes by using methods such as dictionary assaults, brute force, and cryptanalysis assaults. The software also removes the hidden passwords by showing passwords in specific software packages. It learns wireless network keys for forgotten Wi-Fi login information. The software has some security benefits, too, by indicating where passwords are insecure in an active system.
To download this tool, visit the “http://www.oxid.it/cain.html” page.

Once you install the Cain and run it for the first time, you’ll be greeted with an empty dashboard, as is shown in the screenshot.

Click the “Sniffer” tab on the top and then click the “Start/Stop Sniffer” button on the toolbar. Then, select the “+” or “Add to list” button to open up Cain & Abel’s “MAC address scanner” window. We can utilize the MAC address scanner to check all the accessible hosts on the system with an ARP Request broadcast storm. Since we are on a private network (10.10.10.0/24), Cain and Abel are going to filter for all the accessible hosts somewhere in the range of 10.10.10.1 and 10.10.10.254.
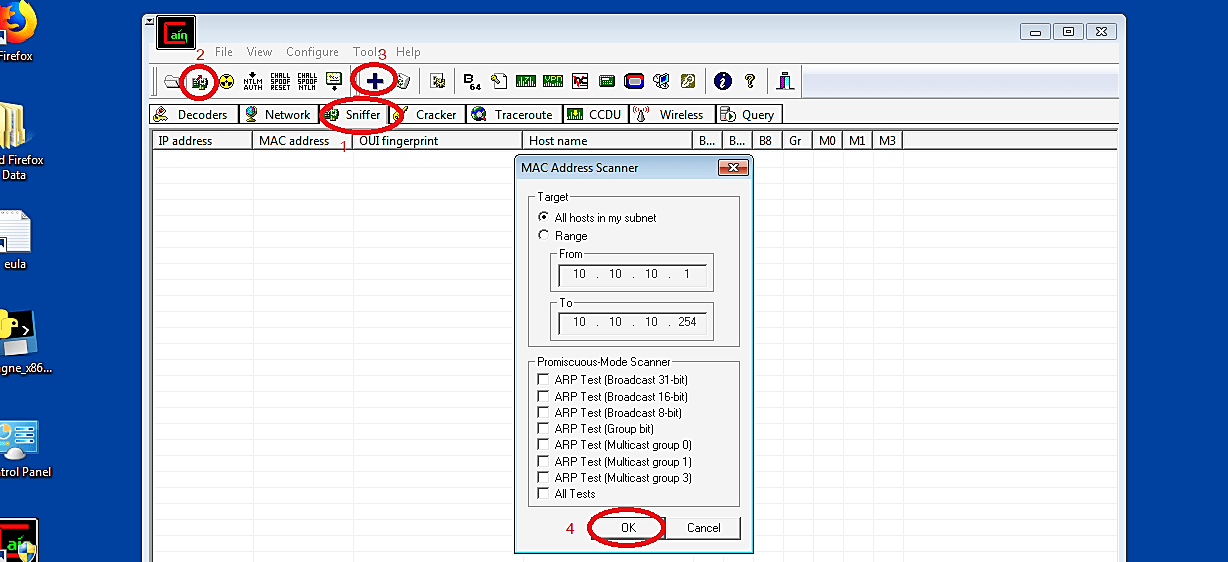
After the scan is complete, Cain will display all available hosts with their IP and MAC addresses. While remaining on the “Sniffer” tab, go to the bottom toolbar and click on the “APR” tab to perform the ARP Poisoning attack.
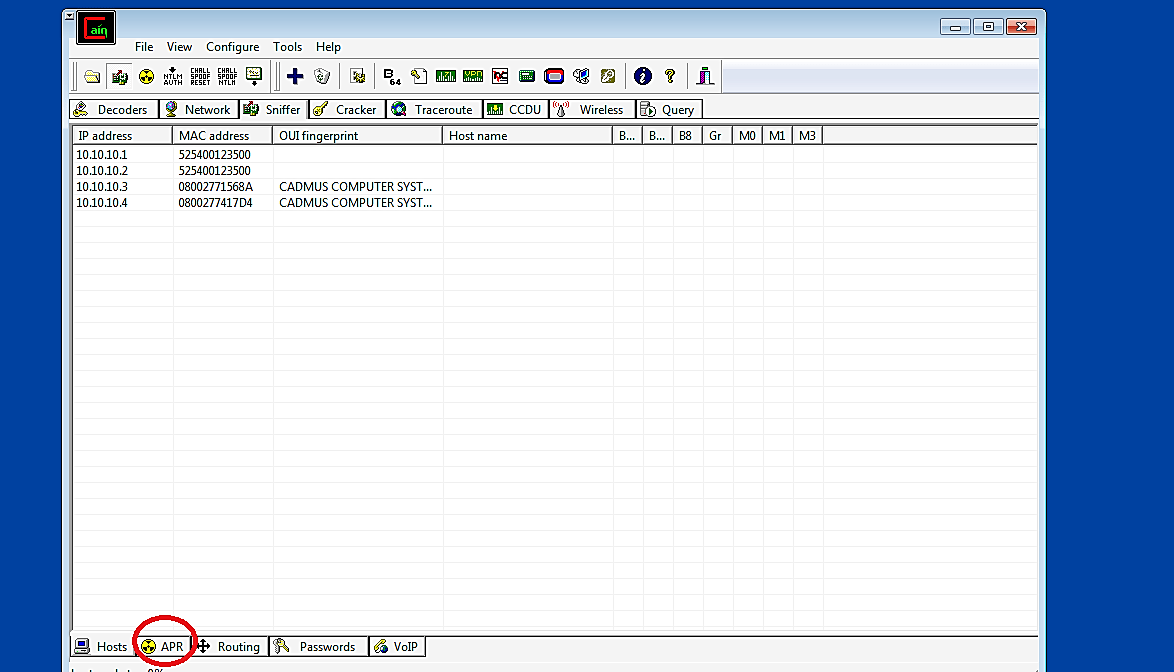
Click any place in the top pane and afterward click the “+” or “Add to list” sign at the top once more. It will open the “New ARP Poison Routing” window. To capture the traffic from the objective to the gateway, we need to select two IP addresses, one for the gateway (10.10.10.1) and another for the victim (10.10.10.10.4), and then click on the “OK” button.

After ARP poisoning is set and prepared, we can tap the “Start/Stop APR” button on the device’s top bar to begin the process.

It will change the status from “idle” to “poisoning,” as is shown on the screenshot.

With the man-in-the-middle assault started, we will most likely completely re-course the traffic returning and forward from 10.10.10.4 and 10.10.10.1. In this way, when the objective demands a Web webpage, that solicitation will make a trip to the attacker’s PC. The attacker will, at that point, forward the traffic to the gateway, and the gateway will then forward the traffic out onto the Internet to the web server facilitating that web website.
The web server will send back the data in a response that was to the gateway. The gateway will, at that point, forward the response to the attacker, and afterward, the attacker will pass it on to the objective. The objective and the gateway will have no clue that the whole traffic is intercepted.

Obviously, with this assault, we will most likely observe wherever the objective is going on the Internet. If the victim enters passwords, they will appear in the passwords tab (if it’s HTTP traffic). If there is a lot of HTTPS traffic, we can decrypt it with the SSLstrip tool (if applicable because some web browsers won’t permit it).
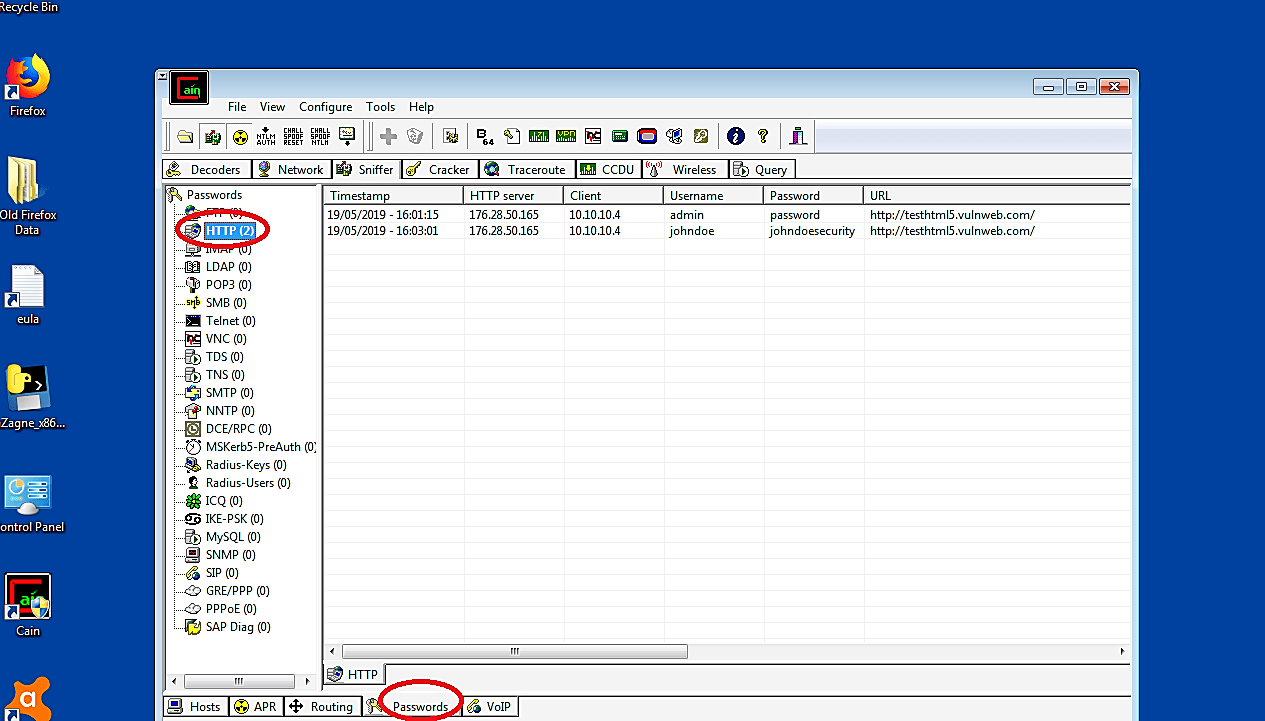
“Cain and Abel” is classified as malware or a virus, so it is sometimes blocked. However, disabling antivirus has no impact, and installation proceeds without a hitch. This is why it is regarded as a “false positive.” It has a user-friendly interface with a basic design. It addresses flaws in the protocol’s standards.
The great thing about “Cain and Abel” software is that it doesn’t depend on general bugs and errors in your operating system to locate passwords. Instead, it examines logs, caches, brute-force attacks, and stored conversations.
