Using BeEF scripts for XSS attacks
You may also use BeEF’s hook script and inject it into a vulnerable site, so whenever somebody visits the website, it will become a zombie computer. To do so, run BeEF and copy the hook script, as shown in the screenshot.

Paste the script in the vulnerable website, and change the IP address to the attacker’s IP.


Whenever any user visits this page, their device will be hooked in the BeEF framework and become a zombie computer.
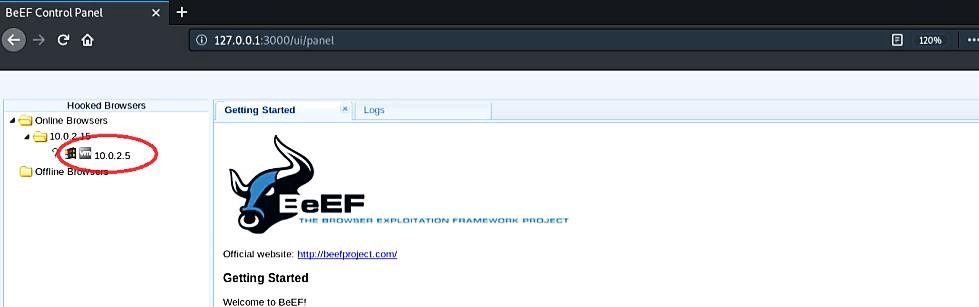
As you can see in the screenshot, we have one zombie computer hooked to BeEF. With this technique, you can create a vast “botnet” (network with tons of zombie computers) and compromise more target devices.
Note: If you want to change the port number of the BeEF tool, you may do so by editing the “/etc/beef-xss/config.yaml” file.

Never put your confidence in user feedback. In other words, all user input should be sanitized at both the client and server levels using escaping, filtering, and validating to delete potentially harmful characters, text, or code (or make it harmless). For any site, there are libraries that can assist you with this.
