Vulnerability Assessment using Nikto
The Nikto is a web security tool that will test a site for a large number of conceivable security issues. Including; dangerous records, misconfigured services, vulnerable contents, and different aspects. It is open-source and organized with modules that expand the abilities. These modules are frequently updated with new security checks.
Nikto is by no means a stealthy tool. It will make more than 2000 HTTP GET solicitations to the web server, making many entries in the webserver’s log documents. It is an excellent way to test an Intrusion Detection System (IDS) that is in place. Any web server log monitoring, host-based intrusion detection (HIDS), or network-based intrusion detection (NIDS) should detect a Nikto scan. Nevertheless, there is support for LibWhisker’s anti-IDS methods if you want to give it a try or test your IDS system.
To start this tool, type “nikto” in the terminal and hit “Enter.” For more help and information on usage, add the “-h” operator at the end.
Ex: (root@kali:~# nikto –h).
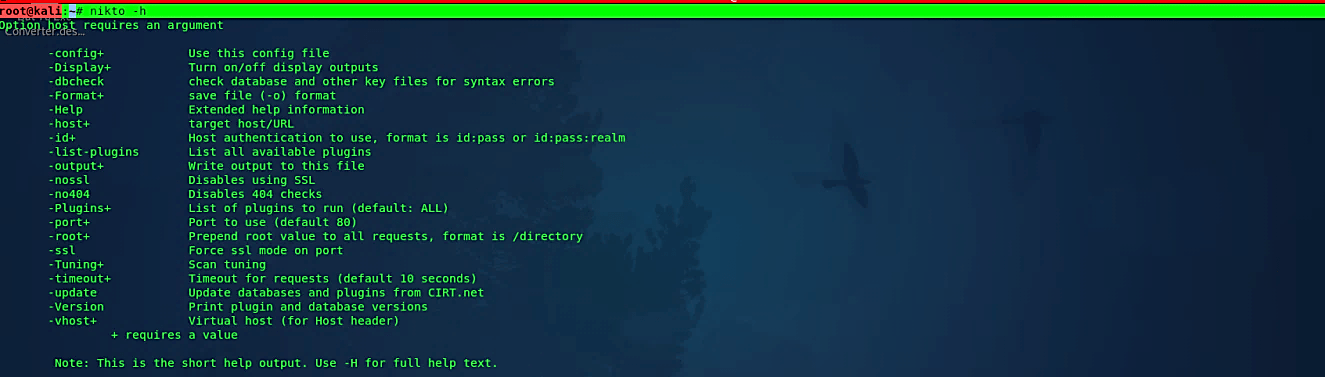
Let’s scan our web server host (-h) and output the results (-o) to the “/root/Desktop/” directory as “nikto_report” with the file type of HTML (-F).
Ex: (root@kali:~# nikto -h 10.10.10.10 -o /root/Desktop/nikto_report -F html).
From the scan results, we can observe the recognized issues alongside their OSVDB grouping. Nikto uncovers server subtleties like the webserver, txt document with the number of present entries, directory indexing that permits anybody perusing the site to get to backend records, and the Apache webserver establishment files.

You can also view the scanned output file “nikto_report.html” in the browser by double-clicking on it. It will open up a browser and show all the results in a very friendly, easy-to-read format.

The Nikto Web Vulnerability Scanner is a standard tool found in the backpack of penetration testers and security analysts. It will frequently find fascinating data about a web server or website that can be used later on for more profound exploitation or vulnerability evaluation.
Vulnerability scanning is just a part of the vulnerability evaluation — different procedures like penetration testing can recognize various kinds of threats to your association. Penetration testing supplements vulnerability scanning and helps decide whether it would cause harm, information misfortune, or different issues.
