Vulnerability in Active Directory may allow attackers to gain control of Windows Domain Controllers
- December 22, 2021
Shortly after the release of a proof-of-concept (PoC) tool on December 12, Microsoft is advising users to update two security flaws in Active Directory domain controllers that it addressed in November.
The two flaws labeled CVE-2021–42278 and CVE-2021–42287, have a severity level of 7.5 out of ten and are related to a privilege escalation vulnerability in the Active Directory Domain Services (AD DS) components. Catalyst IT’s Andrew Bartlett is credited for detecting and identifying both issues.
Active Directory is a directory service used for identification and access management that runs on Microsoft Windows Server. Despite the fact that the flaws were rated as “exploitation Less Likely” in Microsoft’s evaluation, the public exposure of the PoC has spurred additional calls for the patches to be implemented to prevent malicious actors from exploiting them.
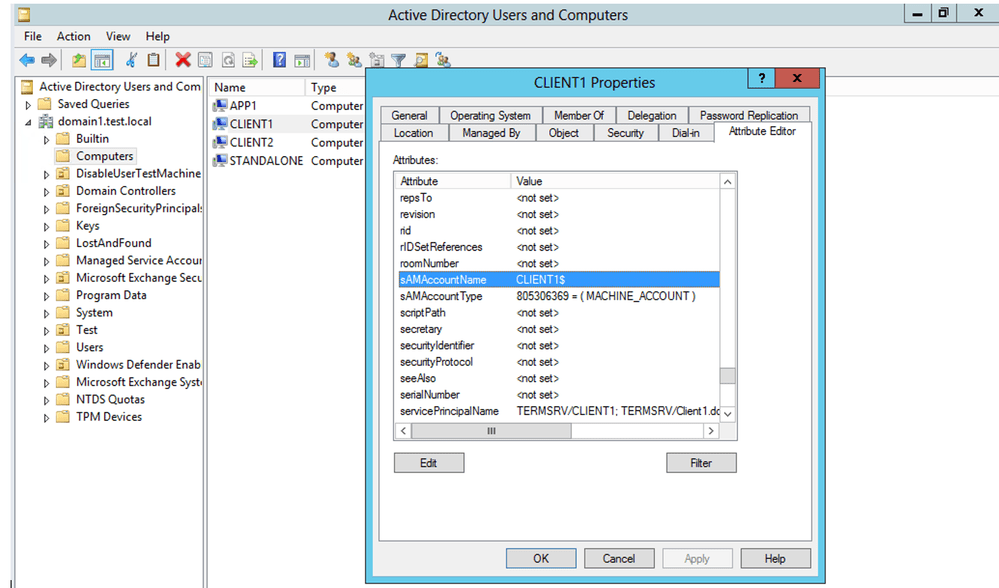
CVE-2021–42278 allows hackers to manipulate the SAM-Account-Name feature, which is used to authorize a user into Active Directory domain systems, whereas CVE-2021–42287 allows a hacker to spoof domain controllers. This effectively enables a bad actor with domain login information domain admin access privileges.
“An adversary may establish a clear route to a Domain Admin user in an Active Directory system that hasn’t implemented these new patches by integrating the two flaws,” Microsoft’s senior product manager Daniel Naim explained. “After compromising a standard user in the domain, adversaries can simply raise their privilege to that of a Domain Admin using this escalation technique.”
The Redmond-based firm has also offered a step-by-step guide to assist users in determining whether the flaws have been exploited in their environments. As always, it is strongly recommended to apply the most recent fixes to domain controllers as quickly as possible.
